Credential Protection in the Password-less Era - THR3048
Hello. How's, everyone doing. All. Right I'm, Steve welcome, to my presentation this is a credential, protection and password lacera. Today, it's a very brief, presentation it's, only 20 minutes so I'm going to hold questions until the end if there are any but. What we're going to look at is a, brief. Overview basically. Of how we protect your credentials and Windows. Targeting. Starting, from you know from almost. The very beginning all the way into what, we have in the password lacera so. Let's. Level set first things first how do people steal credentials well very. First thing is you've got to start somewhere you're running on a box at some point, you. Know us. Callate up to an administrator, and. You start rooting around you, know at, some point you find other interesting, secrets other passwords other credentials, and you start stealing those and use those to move to other devices, once. On other devices you do, the same thing you start looking around what are the devices do you have what other credentials do you have on there and you. Repeat this process over, and over and over again until you get some really really interesting credentials. At. Most companies you do this enough you end up getting domain admin, you, know that's probably not good to get enterprise, admin, you. Know you start with just a standard user you move all the way up it's. Not a good story it's how how quite. A number of attacks, out in the wild end up you, know completely, destroying. Companies, and. So. I'm. Actually just going to show you really briefly how you do that this. Is Riley by the way she's, a 2 year old dog she's cutest, dog in the world has absolutely nothing to do with stealing credentials, but she's an adorable dog. So. You. Guys can see that. One. Of the common tools that people end up using either. As a demo or as a baseline for a lot of their attacks as mini cats the, way that mamie cats works is it attaches itself to our logon. Processes, in Windows. And. It, routes around it looks for passwords it looks for things that are that are that are juicy that are interesting and so. If. We. Run just a single command, get. The logon passwords it dumps a ton of stuff and as, we start digging through them we. Can see some really really interesting, things for, instance your ntlm hash for your domain password. That's not my corporate domain password, that's a demo, password, if, you happen, to copy that drop it into being or Google or anything like that you'll actually find the password really, easily it's p @ s SW 0 rd 1. After. Some point you just kind of start recognizing them there's, a bunch of other things in some cases, you.
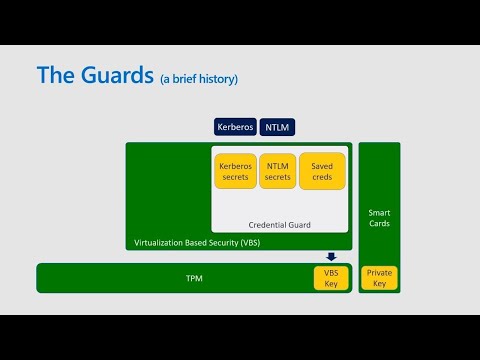
Know As you scroll through the bunch of other corporate accounts, you. Start getting you know that's your host computer, account oh by, the way hey there's your host computer Count password in the clear text not, good so, as you start collecting these credentials, you start moving to other devices you switch. To do you you ping the networking search for other devices as you find oh I can connect to that I'm gonna go run, software on that and oh hey I know about this administrative. Privilege. Escalation, I'm gonna elevate, to admin switch. To that and repeat, the process over, and over and over again. Some. Of the other things that you can do in a non, Windows, environment, you can start stealing session, credentials, from websites, you, know for instance you. Know you're logging into your. Email. Or you're logging into your, your, line of business applications, on the web you, can do things like grab, the session cookies out of the headers and use, them on other machines, and. As, you do this over a period of time you start collecting a massive, credentials. So. What. Do we do about that in Windows. We have a collection of. Technologies. That I affectionately refer, to as the guard's, you. Know, in. The beginning we started with Kerberos, and ntlm, these were the main. Protocols that you used in enterprise environments, they're ubiquitous they've, been around for, in, Windows for ever, basically. And. They, allow you single sign-on into, everything, and so. Over, time we, start to protect these and, the first thing that we did was we use smart cards we. Offloaded, the authentication credentials. Onto physical Hardware so that you couldn't so. You couldn't steal things out of memory there were no passwords, to steal you, had a physical device that you plugged into your computer and you use that to log in, problem. With that is this. Thing called the Kerberos tg2 it's the ticket granting ticket it lives, in memory you use. Your smart card or your password to, talk. To Active Directory get, a TGT, and use that TGT, to start accessing other resources. For. Better or for worse that TGT, is stealable.
So. Then, we introduced the TPM in this case the TPM doesn't actually provide. A lot of value at, the Kerberos level because we could not modify, the Kerberos, protocol, to, have Hardware support so I'll come back to that, then. We, introduced the guard the credential guard credential. Guard uses. Virtualization. Based security which if you're not familiar with it is very simply, it's a virtual. Machine that you don't know about that's running on your machine it's. A very tiny virtual, machine it takes up very little resources, it's, running a secure, version of the Windows OS it's tiny, absolutely. Tiny you'll never know it's there but. What, it does is it offloads, all of the security functionality. Into. This, hyper into, this virtual machine so. When, you're using Kerberos, when you're authenticating, when you're doing any of these things any of the things that were originally, stealable, now. Belong in, credential, guard and in actual fact the way the credential guard works is it, uses secrets from the TPM. Rooted. In the TPM specifically, and encrypts. All of these secrets for you so they still live in. Your side of windows in the user mode side of Windows so that we can use them but. You. Can't decrypt them you can't steal them if you pick them up and you send them to another device they're completely useless. Then. We. Started getting into modern protocols modern protocols are things like Azure Active Directory so, cloud join or for. The consumers, we have your, Microsoft, account authentication. In. Some of these cases their TPM, bound so that means that. You. Can't take. Tokens off off the device, and. What that what, that allows you is if. You, take the token off the device you require the TPM, TPM. Is not there on the other device so you can't use it. There, are some interesting. Side effects of that the TPM is kind of slow it's. Actually, really really slow, so, when you're doing when. You're looking for fast authentication, it's. A little problematic, in some cases it takes a couple seconds to. To. Do anything under, under load. So. We'll. Come back we. Introduced Windows holo which. Is a way. To. Change. How you authenticate, we get rid of passwords, and we switch to buy authentication, so, it's using things, like facial. Recognition or, it's using thumb prints for your fingerprints, or it's using pins or what, we actually recently came out with were security, keys you. Can use a fight o2 security. Key we call it the windows windows hello security key you, plug it in you, tap your finger and you. Can login you can take this to any device you want, but. The value is with Windows hello because, you're not using the password you're using the security key that's bound to the TPM so it's Hardware bound again, it's. Not portable anymore except if you have something, like this which is designed to be portable so, no. More password you, login with your face you login with your fingerprint, you have this way to, it's only tied to a specific device or if. You, have something like this where we guarantee, that you, can't steal the credentials off the device. And then. One. Last thing which is keyguard how, many of you heard of token binding, know, a couple. Of people cool okay so token. Binding is the last step, of our, protection. Mechanisms, that we have in place and that actually doesn't help with authentication, specifically. It actually, helps you with session session, protection, so once. I've logged into the computer I'm starting to access, applications, I'm accessing, exchange, online I'm accessing SharePoint, I'm accessing drop not. Dropbox what's ours. Onedrive. That's the one. You're. Accessing these applications. The problem is going back to that cookie you're, using a cookie using your, using a bearer token here you're using a thing that if I hold on to this thing I can do whatever I want as this user I am effectively, this user token. Binding, much. Like the things that we're doing with Azure ad with the TPM, binding, and the windows hello binding, all these different things were, binding, that token, or that cookie to that device and the. Value is as soon as I steal, that I can't, pick it up I can't, move it it's totally, useless, now. You. Take these last few things you put them all together we have this really cool feature called cloud credential, guard there's.
A Moratorium on, calling things guards, now, Windows. Defender something. Guard we're, gonna stop doing that I promise just, because, everyone seems to like. The guard name and. The. Value with this is it's. Completely. Transparent. To the user no, one ever sees it going on it's actually been going on for the last four years if you've, been using Windows hello with Azure Active Directory if you've been using Windows hello with. Active Directory all of these pieces have been in place for cloud, credential, guard and it's, just been working you. Know over, the last few months we've been moving, to newer versions of things where we're iterating we're, actually moving to the, latest version of the token binding it was token, binding spec was finally ratified. So. Let's. See some of this in action. So. This, is Bruce, also. Has nothing to do with stealing credentials, or protecting, credentials, but, he's also one of the cutest dogs world. So. Coming. Back to the demo machine, so. In. The last demo I very quickly showed you this is how you can steal credentials with. With. The tool called mini cats. One. Of the things that, we have which, I showed very briefly was. Credential. Guard credential guard is intended to protect Kerberos, secrets amongst other things but, I have it running on this machine on this honest VM and. So if I run that exact same command. What. You will end up seeing is a. Lot of random garbage. Now. It kind of looks the same because it's dumping a whole bunch of stuff really quickly but if I jump to the top real quick you're, not seeing the same data you're not seeing those hashes in those. Hashes, unprotected. What you're actually seeing is encrypted values so, whenever, you're needing to talk to Active. Directory basically. What happens, is, our. Kerberos. System calls. In to credential guard credential, guard then, connects, out. Sorry. Decrypt, the key connects to Active Directory gets. The token brings it back uses credential guard to re-encrypt it and there, you go you have an encrypted encrypted. Value again so an attacker cannot actually take, these keys or cannot take these secrets and use them elsewhere. Some. Of the other things that we also happen to do as, part of our constant, ongoing process, is we, just start removing, stuff out of our security processes, entirely, there's, a lot of data that we've just removed you don't end up seeing so, so for instance we, just have everything's, encrypted or it's just not present anymore. You, still in some cases get a couple hashes, but. We've, designed it in such a way that the hashes that you can actually get to are completely. Useless you can't take them off while well you can access them you can't take them off box and do anything interesting with them, in. Some cases you also get encrypted, so, that was the that, was the the. Host host. Account is the encrypted password you can't steal that you, can't decrypt, it there's nothing there's nothing accessible, to you. A couple. Other things. Token. Binding so. This, of course locked, by account. I built. This demo special for you it's, a tiny little test app if you want to go try it out you can't ignite - TB identity, and rent intervention, calm the, way the token binding works is there's an agreement between.
Your, Machine and the site, you're connecting to over, TLS, or SSL, whatever, you want to refer it to as, and. What. Happens is when I've connected to a particular, domain, your, your your, browser basically says oh okay I'm going to guarantee that whenever I connect to this domain I'm gonna use a special key and I'm, gonna make sure that whenever, someone, asks for this key within this site I can, prove that i own this key now. If you think about it the value of this is that, if, I have this site give me a session cookie and I've bound it to this value and I, try and take it to another machine and the site says hey I need you to prove you have that key it can't because it doesn't have that key, so. If. We imagine for a moment that I'm logging in I get. This weird session, value this is just demo, this is a demo for the sake of the demo but, the idea is that this my user name is bound to this key and so, if I copy this, and. I open a new tab and I. Go back and. Load. This up again. What. Happens is and I drop this in this is like how you would do a session cookie you. End up seeing this value hey yes I'm logged in it's the same session you're good there's no no problems there now. Let's. Use the right keyboard combination, open up and in private view one, of the things the browser's decided, that is if you're using in private view we shouldn't actually be able to tie you back to a regular session so, if I pull this up again. And. I. Drop this into the session. Suddenly. It. Doesn't have anything to bind it against and suddenly I can't. Use that token anywhere, else so if you take that off box you're. Completely you're completely hosed you can't do anything about it. All. Right. So. That's. My presentation, very. Whirlwind, tour of all the different technologies any questions a. Lot. Of confused faces no. Yes. Yes. Sure. So the question is what, are the benefits of using hello windows hello for business with credential, guard I very, briefly talked, about what windows hello for businesses its bio it's, its bio authentication, of users using. Your device so, when. You're using credential, guard credential, guard is there to protect your Kerberos tickets so when you're doing Active Directory authentication.
Its, Used to protect the Kerberos T GTS when, you're using Windows hello for business and you're still connecting, to on-prem, resources, you still have to use Active Directory you're still going to end up getting that TG to you so the value of those, two together is, that, you're protecting, your TGT and you're still using Windows hello so it's a they go together quite well. Any. Other questions. Yes. Yes. Sorry. Say that again. Yes. Yes. Oh yeah. So so I think are, you doing Azure Active Directory joining in that case yeah. So in that case there. Is we don't we don't grab the group membership tickets, yeah. All right sorry the group membership sins. No. So what you're actually seeing so when you're doing who am i that's. Actually showing you what are the group's id's for that machine so when, you're actually exchange, it so you're not seeing the entire pack yeah. So you're actually seeing you're only seeing a subset of it so. The whole pack does include all the tickets are all. The sins. Questions. Yes. Yes. No. You never do so the question is if you're using Fido, with. Remote desktop to a remote machine are you, exposing any of the credentials, to the remote machine from. A or. To the local machine. Oh, I. See yes so in that so is. The is the key is. The credential exposed to the local machine in any case even if it's not remote desktop you're still not exposing that credential to the local machine because. You're using the phyto you're using the final hardware key that key never leaves the device so. For. Instance using one of these this is a phyto to. Biometric. Authentication, key. The. Key itself lives, on this device so that's how how it's portable. How I can plug it into multiple computers, and login. Yes. Yeah. That works. Yes. Isn't, it great how, many of you had a chance to look at the Fido keys few. People yeah so, the value of the value of the security key is that with normal, Windows hello your, account or your credentials, are bound to the particular device so if you ever have to move to a different computer. You. Have to re-enroll on that device that, can be problematic in certain scenarios so if you have this Windows hello security key, the, credentials. Tied to this instead. Of the, device and the value is you can start moving to different different, pcs at any time without having to re-enroll. Yes. Sorry. You would revoke it at the server so, the way that this works is there's a private key on this device there's, a public key attached, to the authority which in this case is Azure Active Directory you. Just remove it from, Azure Active Directory and it can't authenticate anymore. Yes. Yes. Yes. I'll. Talk about it so the question is. Paraphrased. In just, this week at blue hat at our Microsoft, security conference, Benjamin, Delfy released, mimikatz a new version of mini cats which, allows you to even if you have credit card running steal. The passwords and, I. Just. Said previously, hey, if you run if you run credential, guard you can't steal the passwords well I kind, of fibbed a little the, thing is the. Way the credential guard works is it protects derived secrets, it's intended to protect your Kerberos T G T's it's intended to protect the things. That you can take off box and use. To. Go. Across machines you can do that with a password, but. The issue is that there's, a specific gap, between, when, the user enters their password, into the PC into the keyboard goes, up into Windows, and then gets authenticated, to Active Directory there's a gap that we cannot control in many. Systems, and. That's one of the reasons why we don't actually want you to use passwords that's why we're recommending you go to password lists in, some, cases with. Windows, 10 s we, block it out right there's no way you can do that at all that's one of the benefits of Windows 10 s there's no way that anyone can actually inject into that code path to, get those passwords.
So. Does, that answer your question yeah. Yes. Oh, allow. The phyto keys I, don't. Know, it's. An interesting question, I will give you a business card after and we. Can look it up for you. Any. Other questions. Going. Once. Going. Twice. Alright, thank you very much I appreciate it.
2018-11-01 23:54


