Cloud Threat Gamification: Lessons Learned and How to Set One Up
- [Jon-Michael] Welcome, everybody. I'm Jon-Michael Brook. I'm a principal security architect. I handle basically a business information security officer for Starbucks.
I handle MarTech retail and emerging technology as well as APAC. And so what we're gonna talk about today is very applicable to each one of those market segments. - [Randall] And I'm Randall Brooks. I'm a principal technical fellow with Raytheon Technologies. A lot of the stuff that we're gonna talk about is through work through the Cloud Security Alliance. So we'll make a lot of references to them.
I am our principal representative to the Cloud Security Alliance, and a lot of the stuff that we're gonna talk about is work that has been done through the CSA, which we greatly, prop up and say something that you guys should check them out if you haven't looked at them, especially if you're interested in cloud in general. They are pretty much the definitive place you want to be for cloud security. - [Jon-Michael] And then I'd share that same working group top threats as well as a one of the research fellow with them. So long history, really good work coming out of them. And again, it works nicely when you see the rest of the presentation here. Or, oh, that's the other question.
Who is actually in the lab on Tuesday? Anybody see? That was a little bit later in the day. So those people were up not at eight 30. - [Randall] Yes, this is actually the second presentation that we had this week. I actually wasn't supposed to do the first one, but I was able to attend it.
And so some of the lessons learned even became even more lessons learned because we just ran this like two days ago. What we're gonna talk about here today. So a little bit disclaimer, this is kind of the RSA one. Ours is, it's basically our opinion.
It doesn't even necessarily represent our company, nor does it represent the Cloud Security Alliance, which a lot of this work was done with. So just if you have any complaints, please send it our way. That is Jon-Michael. And then just a little bit more about myself, I also do our, I'm a chief engineer for our product cybersecurity group. So I work directly for the Chief Product Cyber Cybersecurity officer for our company out of corporate.
And I went to Purdue, which I'll have to always bring up because Eugene Stafford, who is my professor, and if anyone wonders why I wear bow ties because of him, he's signing a book I believe today and so forth. - [Jon-Michael] Make him a bo best selling author. - [Randall] So what? - [Jon-Michael] Nothing. Anyways, please forgive us. This is a working title. Apparently nobody researched that.
Game of Threats was trademarked, so kind of ha had a had a quick moment. You can see the Game of Thrones reference there. We're going to fix that. We've got a couple of ideas already.
- [Randall] Yeah, the TKI Alliance has been going through a varied number of potential titles for this document. We actually don't have it out, but this should be coming out and available on the Cloud Security Alliance's website in about a few weeks, actually, - [Jon-Michael] June. - [Randall] June.
- [Jon-Michael] June. - [Randall] Okay. They say June. Here's some of the main authors of it. Kind of started off with kind of a brainchild that Jon-Michael, and myself had.
We brought it to the CSA and got a bunch of folks to help author the rest of the document and so forth. So one of the things that we've been doing with the top threats is we've been surveying a lot of companies out there and kind of say, what are the biggest risks that you would use? And by the word, the top threats is a trademark term by the Cloud Security Alliance. They are more issues that you have to deal with respect to the systems that you interact and those types of things. So (clears throat) what we're trying to do is kind of take that knowledge of those threats and figure out how can we make this a little bit fun? How can we gamify it? And we're trying to help get folks involved, understand. And we had some additional work on the area of threat modeling. And so we tried to look at cloud services and things that you might have, how do we apply the top threats to that and figure out how can we use that information to help teach folks and help folks learn about the threats and how they might affect their system.
And so as such, we came up with this idea of creating a game based on the work that was done through the CSA. All right, (clears throat) of course, this one is eye charting. I, it's hard for me to see it from a distance. So when we do threat modeling specifically for the cloud, we focus on really what we wanna protect, how my, or how we are going to protect it, how likely will we need to protect it and some of the consequences of failure. And so we applied that same concept with respect to doing some of the threat modeling with respect to the cloud.
So the first item that we do, and we do this in the game as you go through it, is we kind of identify our security objectives. What do we need to achieve? What's, system are we building and what goals that we might have. And then we kind of create a scope of the assessment. So in our instance, we draw out a system really quick, and then we look at that system and we start to decompose it and look at the piece parts that comprises that system.
We kind of focus on really the ingress and egress points and how the system, might interact with other things. And then we look at those potential threats. So we reference back to, it came out last year called the pandemic 11 for top threats to cloud security. And so we took that pandemic 11 and then applied that based on the system.
And then look, and from that, as a group, as you play the game, you start to talk out and identify any weaknesses and gaps you might see in the system. So it kind of like has that tabletop exercise kind of feel where we're trying to get folks speaking and talking to each other and understanding what issues that you might have, and then come up with ways of fixing that with controls and just getting everyone together and coming up with a plan on how to improve a system like that. All right,(clears throat) so in our system, we do try to make a little bit of randomness to it since it is the pandemic 11 and unfortunately not a 12 or even sighted thing.
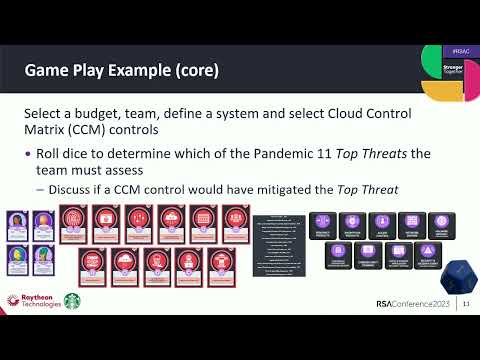
We came up with utilizing dice, for example, where you roll a dice and of course one in 11 kind of will address to the first item there. You can see it a little bit in the red cards. And when the full document comes out, there'll be whole big detail on all of these little items here on what they are and how they might, how might, you might read this to play the game. So you do roll the dice and let's say you roll, number one, then you say, okay, we've selected controls, we have people to operate our system, how might that threat have affected our system? And then we add a little bit of extra randomness and say, "Hey, you know, even as good as you possibly did that potentially this threat could still affect your system based on just a extra bit of randomness. " We've selected about 25% of the roles, even if the best you did an unknown vulnerability comes out and you're still hit with that particular issue. All right, so in our case, if you did roll a two, that that equates to, in the pandemic (indistinct) the insecure interfaces in APIs.
And so as you roll that, you basically say, "Hey, do you know, did we have any kind of application security processes? You know, did we put any kind of, money and controls and effort into securing that portion of our system? And then to add that little extra part of, does it affect us? We chose 10, 11, and 12. You roll that and you say, "Oh no, the problem happened." And then you roll it again, you get a six, and then you lose a little bit of budget. Now we do let the folks, we have a person, he's the kind of the person in charge. He's the CISO, a program manager.
That person will start off with the $5 million budget. He'll, he'll buy his controls, he'll buy, he'll hire his staff. And the controls are basic, are based off of whether their platform as a service, software as a service, infrastructure as a service and so forth. And depending on which one you choose, they have a certain level of cost and what we call an ease of use factor with respect to that.
All right, you wanna do the- - [Jon-Michael] Sure. Advanced. All right. So one thing that I would like to add, so that top threats marketing term, the risks that go along with it, those are something that comes out of a survey that we run every two years within the top threats working group. And then we do a deep dive quote unquote deep from the standpoint that it's ancillary of minimal.
We, it's more than just, hey, this is what we came out of with the survey. It's actually looking at case studies. So colonial pipeline would be one that's coming up pretty shortly. Some of the log four J, the breach incidents that occurred with that, those will be included in there as well.
Now here you see the advanced version of the game. And this is what we ran on Tuesday. We've run this about five times thus far.
You guys are seeing the, the first four. And with each iteration we've tried to incorporate more easily run and well at the same time trying to make sure that the randomness and the overall playability works. So with the advanced version you see up there, similarly roll the die, come up with one of the pandemic 11. You could also, we chose the die just because of the randomness that goes along with it. However, you could also do it with like a deck of cards if any of you have played the horses game where, you have one through one through 12, you take money off depending on the dice roll.
So here you see the, you roll two similar to the easy version of the game, but in this one you have mitigations that you also add in there. So again, the cloud security alliance has a complete gamut as far as a cloud controls matrix. So similar to like a NIST 853 or an ISO 27,001, a series of controls that give you a framework that you can work against.
Well, it's got things like encryption, it has things like infrastructure and perimeter defenses. So we incorporated those. You can see network defense, you get your choice, as Randall mentioned, infrastructure SaaS PAS you can also roll it out as a hybrid on-premise.
So with this particular incidence, you or in mitigation set, you see the CICD pipeline as a SaaS offering and then SaaS and dat. So we initially said, okay, use some of the previous work that we'd done with threat modeling. Let's create that system, put the mitigations in place, and then go ahead and roll and see what gets exploited. At the bottom there, you see the roll of seven. So you create a team within the little purple cards that you saw there a second ago. They have costs and they have capabilities, right? So a CISO is going to have, I think it was a 10 as far as their overall capability.
Whereas a deputy CISO is going to have more time during the week to work on things like incidents. That's the idea. You got interns in there, they're going to have the lowest applicability, the lowest capability, but they also have the lowest cost at the bottom there, you see those calculations. The project manager is actually the kicker.
We had a lot of people gaming the system and we'll talk about that in a couple of seconds. Good. So far more or less, A little confusing. Yeah, that's what we found in the present area in the labs, yes. - [Participant] About capability requirement.
And we're talking about capacity change. - [Jon-Michael] Yes. So those are, unfortunately, I didn't catch that one.
Within the document it says work capacity, everything's capacity. So, and that was actually one of the things that we picked up during the run throughs. That particular piece became problematic from the standpoint that yes, people were like, what's cap a capacity capability? So, all right, lessons learned, general lessons, the top there, this needs to be run if you are going to create one of these, right? It's what we did. Let's just suggest that it has an applicability to large corporate organizations. I'll just say it that way. Build it versus buy it.
If you go through and utilize the examples that are within the game as it stands, those examples are generic, right? They're not customized to the environment. Whereas when we go through on a larger organization, you can pull those directly from the systems that you're actually using, right? You want your developers to learn. Well, in doing that, you're going to have much more project management style work. You've got time that's going to be required to, for upkeep. And so that's that first bullet duration. We found this out.
So the version as it stands right now, that'll be released in that document. We tried it with a two hour timeframe, right? Description, how to play the game, 40 minutes is what we use to do all of the setup, et cetera. The background explanation.
And then 80 minutes. - [Randall] 80. - [Jon-Michael] For the gameplay. The first one about a year ago, I won't say it was a disaster, but we did not have the example systems.
And we just expected as a technical audience that, RSA, we expected that there would be at least one architect or one engineer, one developer that could come up with a system, right? Hey, what does a lamp stack look like in the cloud, right? What can you actually deploy as a platform, as a service with Kubernetes in Azure? Oh my goodness, it was a disaster. So we kind of gave them a system, kind of drew one up on the whiteboard and said, "Hey, if you don't follow what we're doing, try this one." So we created two of the systems and eight examples as far as, "Hey, what about a human resources system," right? Learning management system, internet of things, what would that look like? HR, et cetera.
So we gave two single examples, or two fully decomposed examples. And then where those cloud controls matrix pieces would come in and mitigate, right? You put in a perimeter, perimeter defense, you put in a firewall, what would that look like? What would that protect you against? Within the game itself. You see the learning time. How long does it take? That 40 minutes versus an 80 minute gameplay, right? It seemed like it was okay. It'd probably be better to have a 20 minute learning time versus whatever that would work out for a two hour, three hours, 40 minutes of learning probably about right. Durability and longevity.
How long do you want this to work for, right? The examples that we included might not be relevant in another, say, six, eight months, year, whatever it is. As far as the maintainability running this at a conference, again, we expected a technical audience and in some of the conferences we had that, some of the ones we didn't. So when we run this at an executive level, right? It makes it a little more understandable as far as the business aspects go, but the actual technical gameplay and what mitigations you're going to put in, et cetera, didn't quite translate, right? So they understood the business side of it, they understood why they're dealing with headcount, what it looks like on an annual basis as far as the dollars and cents go. But when you started getting into, hey, we need to put a an audit capability in there and that's going to mitigate X, Y, and Z of the pandemic 11.
Oops. Right? Didn't quite follow training objectives. Again, we run that top threats, the working group, we put those surveys out every two years. So theoretically you should be updating it every two years, right? Is that something that you want to do? Is that something you want to take on nist on the other hand, I mean, how long did it take between R four and R five? At least three or four years.
Five years. - [Randall] Yes. - [Jon-Michael] So how many places will this be presented, right? Is this something that you're going to use for an entire year? Are you a consultant? Are you going to do this at multiple organizations, one a week, one a month, one a quarter? If you're just doing it internally with your developers at that particular organization, probably a little more, a little easier to run through with teams that already understand the system, the requirements that you have in place, et cetera.
And then trainers. So we had four trainers, we had the two authors and two facilitators at the one just this past week. And even one of them, one of the guys that helped review and write the material still had a little bit of difficulty as far as capability versus capacity, right? Having those particular words in there didn't quite add up. And then cloud specific challenges.
Does your training, the people that are going to your attendees, do they understand the difference between IAS, PAS and SaaS, right? We kind of took some liberties in saying that SaaS was easier to implement, but probably less effective. And we'll explain that a little bit more here in a second. You wanna cover this one or you want me to? I've talked a lot. I'm boring. You can do this one.
All right, you can do the last one. So, randomness, some of the things that, that came out of that, those five courses, right? Randomness seems silly, but if you take a pair of dice, who's gone to Vegas, who plays craps? Yeah. What happens when you throw a three and a four, a five and a two, a six and a one, right? You get paid on the pay line that's crapping out or not crapping out, but you lose all your money if you had a point. So it's easier to roll a seven versus a two or a 12. And that randomness actually impacts the gameplay quite a bit. So we wanted an even distribution between one and 11, probably should have used a deck of cards 'cause you can actually pull out the kings or the ACEs and you'll get that one through 11.
However, we didn't, because we originally thought of it with the die, right? The 12 sided die, you can use a spinner, those probably work pretty well, except you gotta create it in advance and then you're going to tear 'em up or somebody's gonna take them with them. Pseudo random number generator dude, really, I mean, you're gonna have each person download an app or something along those lines and one person's going to use one that doesn't have a good randomness generator, et cetera. That framework, authoritative source. What does your environment, what do you as a company use for a framework, right? You want something that is holistic from the standpoint.
And if you've got requirements written against those, even better, you start looking at things like cryptography. You've got a set of requirements that you can put in place based on nist, based on iso, based on the standards that you have for your organization. Design examples, I mentioned that a little bit earlier. People are like, what the heck do I draw? Right? What am I going to put together? What does it mean when I do everything with in a cloud Azure active directory versus ad on site, right? Some directory service that you have running inside of your corporation today. The game examples, going back to Randall's easy versus the advanced version, the easy version was just roll the dice, it hits, it hits you, take some money, you say, "Hey, why did it happen? Why did it work? Why did it not work?" The advanced one, it became more fun.
The, some of the feedback that we got was like, the anticipation of whether or not that die roll was going to hit was fabulous. I was like, cool. But it was also a little more confusing to set up, right? That mitigations and scoring, this is one of the things that will come out within the document itself is a scorecard on how you can put together this game, right? That was one of the big findings. People were like flipping back between pages.
The first one we suggested, "Hey, why don't you take a picture of this one?" Don't do that. That was that made it impossible. People are flipping back and forth on their phone, it's just not enough screen real estate. So we ended up figuring out how to put everything onto one page.
Even that was a little bit difficult. We ran it with the sample document and there was some feedback that came out of that like, "Hey, why don't you put together a YASI style scorecard?" Right? So we'll take those. Maybe there'll be an even more lessons learned, I don't know, but we're trying to incorporate as many of those into our document as we can. And then presentability, right? Printouts extraordinarily important. Oh, and don't print them on glossy paper people. I mean, these are things that you won't really think about.
You want it at that high res, but then people can't write on the page unless they have like a sharpie marker. Maybe that's something we do in the future is have like Sharpies. - [Randall] Yeah, we did have a Sharpie, but we had it like on a frames. So yeah, it was one of, definitely we had people commenting on that particular item. - [Jon-Michael] Okay. Application, Mr. Brooks.
- [Randall] Okay. So there are multiple variants of this particular game. The initial concept was to make it a dice game. We also had the idea of making it a card game. And there is in the cloud security alliance's threat modeling document, this idea of playing cards.
And in the playing cards, you'll have an asset, you'll have a threat, you'll have a result or an impact on your system. And so one of the things that we tried to do is say, okay, let's look at something like Colonial Pipeline. It wasn't necessarily a cloud issue per se, but how would that apply given the idea if you took any threat out there and looked at it with respect to specific results and so forth.
I actually can't see from that side. My eyes are not that good. (Jon laughs) (indistinct) Yeah.
Okay. All right. So we went through each one and for the Colonial pipeline, we basically said, there was a system out there that had a single, username and password for a VPN access. Well the attacker was able to leverage that and get network connectivity and then propagate crypto ransomware into their environment.
So we looked at that and we said, okay, there is this asset that we have, we have this threat, we have this control. And, to try to mitigate those different issues and try to look at, what was the items that it threatened and so forth. So that exploit or that threat exploited this particular issue and then it affect this asset and then it had an impact and you had what mitigated it.
So the idea, or one of the original ideas, a concept for the game was we were gonna have people do all of this, right? Go through a particular story and think about writing all this down and making this into a game. Well, it didn't sound very fun initially. So we decided to make it a little bit more random and add a little bit more items to it such that they could make it more fun. And so when we started to do this and had this concept, and we're gonna do it for RSA in 2022, that was our kind of our idea.
But we print, we had like we had, we said, we'll just use an A frame. We'll have them right up. And so for each dice roll, they'll have their system, they'll roll their dice, they'll fill out the carts.
We found out that filling out those cards takes forever. One group did it, but they got zero dice rolls in because they spent all of their time designing their systems and creating, creating cards and so forth. So I would say, although this idea works, you only really should use it if you got like a day of time. So huge lesson learned cards can be hard and scorecards was a lot easier.
In fact, in the actual document when it is released and we do have a few pre-printed copies here. We have a scorecard in the back and we kind of try to think about the same kind of idea where you could just check it off and move forward with the card. So. - [Jon-Michael] These are a great artifact. If you are doing the, doing this at a corporate organization event, those fall out and then you can reuse them, right? You actually know where they fit within your development environment, you know where they fit within your enterprise environment.
You understand that you don't have good auditing or maybe your may, maybe your security operations center doesn't have a good incident response plan. You can uncover those through those artifacts. - [Randall] Right? Yeah.
And the more time you have, the more effort you can spend with respect to that. So the one that we tried to focus on was kind of this whole incident response idea. Like you make up a system, you roll the dice and here's a much bigger version. So you kind of can see it there for roll 11. I still can't read it 'cause my eyes are so bad.
But you roll 11 and then you have that threat and then you basically go around and try to help facilitate the group talking about what the issues are. And if you're in the group and you don't know anything about it, you can learn from your other participants as one of the things we definitely found out as a lessons learned that folks attending learn from other folks, they talk about some of the same things. They may chat a little bit before the session runs and they'll talk about their own particular experience with those particular threats. And so our idea with rolling the dice is hopefully to get an even distribution across all of these 11 items. Now we did use number one for the first time for one in, sorry, one in 11. And that's because people just mess up authenticating all the time.
So that one hit a couple times, but then some folks would say, well, it was okay because one time it didn't become an issue for us with the next time it did. And then we had to go into the next level with that anticipation on what was it gonna cost in cleanup time that this particular item did affect us. Now this is the pandemic 11. If there is a future 12, which I will probably poke on them to make it 12 or something nice, nice. And even then these will all change, of course in the future.
The CSA does put this out every two years. In fact, the very first version we did of it had the egregious 11, which was a former name for it, sinister. And so we had to go and update it for all of those and draw out a bunch of little icons and stuff like that.
- [Jon-Michael] The first one was the sinister seven. There've been like six of them. - [Randall] Well, the first one we ran the game.
- [Jon-Michael] Yeah. - [Randall] Yeah. - [Jon-Michael] I gotcha. - [Randall] Yeah, so we ins we instituted a game with the pandemic 11 and then right at CSA, I'm sorry, right at RSA 2022, they released the pandemic 11. Then we had to go and re-update all the slides.
So part of the durability is you'll end up updating it depending on what your system is. So say that you did this with, like the CW top 25, right? You're working with a bunch of developers and you say, here's the top 25 weaknesses and code, and we're gonna look at our systems, we're gonna say we're gonna learn about these weaknesses. We're gonna say, do we have, stuff in there to make sure that our code doesn't have these problems? And you can take the same concept and apply it and adapt it any way that you would like.
- [Jon-Michael] Okay, this way. - [Randall] Nope, I can't seem to make it go forward. Oh, we're out of, okay, all right.
Another thing that we had a little bit of difficulty with folks was gaming the system, right? We had to look at, and this is, that capability or whatever, we decided to name that. But the idea there is that you had a CISO and you know, a project manager, a consultant, a deputy CISO, a senior manager. There's one or two I think not particularly depicted here.
Well, we found that one group hired like 16 interns and that kind of game, the system, right? And so we had to kinda set it up so you know, they were only 50 K, but if you added it up, they got a lot of work and sometimes you do get a lot of work outta interns, right? So not that that's discounted, but we tried to make it little bit more realistic like that you'd have a guy in charge and so forth. And we added this capability with respect to the program manager, where the program manager had the ability to enhance the group's ability to do work, basically, that they were getting them organized and moving forward. These are some of the example of the controls.
And so one of the things that we tried to integrate to make it a little bit more readable for doing this as a conference talk or a conference activity, was not to print out the entire cloud controls matrix. If anyone has seen the clouds controls matrix, it is a big long Excel spreadsheet that no one's really gonna have just printed out, right? So what we tried to do is go to the CIS 18 critical security controls. We did kind of skip over the policy ones and we kind of like said, okay, you might, some folks might want to add back backend policy, stuff like that. But we'd looked specifically at technical controls. And so this one's business continuity and resiliency. And so we kind of called it the resiliency products.
So we came up with whether, software as a service, platform as a service, infrastructure as a service and so forth. Given the ideas that if you have it in-house, it's a little bit easier for you to utilize, but it takes a little bit more work where if someone is doing it for you, it takes less work, but it's not necessarily as effective. Now, definitely as a huge lessons learned is to give example systems. Now, if you're doing this on your own system, and this has been done, folks have taken this in some of its pre-release set and said, "Hey, I've got a HR system," this is what our real system looks like, draws it all out and then thinks about, these particular items, we actually did a payment system and an HR system. Folks still use their phone to take a photo of what that might look like.
So it's always nice to have like a printed copy of an example system or drawn out. We had easel boards so folks would ease and draw that out too. All right, do you wanna go over. - [Jon-Michael] Sure.
- [Randall] On the specific examples? - [Jon-Michael] So as mentioned a little bit earlier, one of the things that we did additionally find people complaining like, well, why is SaaS for this more effective than a hybrid environment for that? And so again, we took some liberties as far as prevented detective corrective controls one of those that, hey, it might be harder to find somebody that actually knows the PAs environment within Azure, right? It's going to be easier to find somebody that can I i that that somebody can identify and put out a firewall product that's on on site, right? So we took quite a few liberties, we grabbed quite a bit of blowback in the original version. We covered that in the document as well. So in the decomposition we got this far right and we ran it with this level of decomposed system.
We listed the top six potential mitigations and what those would look like within the environment. And you know, the idea being, look, here's some examples, here's what you might look at as far as the system goes, this also flopped. Yep, that's right. People are like, well we don't have all of these, we can't take all of these aren't on the scorecard, darn it. So then we put these together, right? And one of the comments was Randall didn't want to put something out there that people were going to complain about even more. Well, why do I have Azure active directory in there? What does that look like? - [Randall] Yeah.
- [Jon-Michael] Right? - [Randall] AWS. - [Jon-Michael] Is this hamman, is this really a lamp stack? You know, I mean from that standpoint, again, there were complaints and we're like, gosh, darn the heck. So we got one further in and actually showed (chuckles) where all of those controls would fit in. So you see the ais control. So you've got a SaaS tool that's actually running through all of the code that people are developing. You've got that identity and access management with Azure active directory versus ad on-prim, right? And so we set one of these up for AWS as a pure PAs play.
We put the Azure active directory with some IAS and some of private cloud hybrid organizational elements such as the seam or the syslog at the bottom. And then those cost factors start coming into play, right? You see that, oh gosh, which one do I choose? And so man, we really were learning the whole time. Here's the first of the mitigation tables, let's try to get as many of these pieces put together in one slide as possible.
And people forgot what the icons meant. Darn it. You know, you try to make it simple. And so we got a little bit further, darn, what do the icons mean, right? You see all of these Xs on the screen.
Those were hard to follow, right? We actually went through and within the top threats documents, the CCMS listed, well, that's not what we used for the first cut. We used the CIS 18 critical controls. Well that didn't quite make it as holistic. One of the findings was, hey, you might benefit from having a complete soup to nuts implementation, right? CSA has the CCM, they've got the top threats, they've got the this, they've got that. You can put all of those together and it just makes sense. Whereas if you're dealing with nist, you've gotta get some OSP in there.
Maybe you've got some requirements that are derived from your overall control framework, et cetera. Oh, you were supposed to do that one? Yep. Go for it. - [Randall] All right. Yeah.
So to make it even more easy, we gave them a printed example. Like here's ones that we would choose in our group that we had just a couple days ago. They said, "Well, we don't like those controls, we'll buy them all right?" And so they literally chose every possible control and to try to also to game the system, they chose the cheapest ones, which is tends to be the SaaS ones, right? So they purchased every single possible SaaS solution. So in our case, the whole thing would be green for the whole thing. But then they realized, and we kind of talked about this in the advanced section, that you do need a team to actually run the system.
So I helped them determine do they have the right team? Well, they only had like three or four people, but they had bought every possible control. It's kind of like walking out in the RSA show floor saying, I've got millions of dollars. Come sell me something, and hundreds of people are gonna come and, pester you for the rest of your life. Well, they had their team, they were not ready to do that. So they had to cut some stuff back when doing that. And then we eventually, we, and so in our, lemme go back one, in the one that we have now, we use this as a blank slate right now.
This is our current scorecard without the numbers populated here so that you could just write those in for the folks. - [Jon-Michael] One of the other game elements that from a lessons learned standpoint, hit one back, we put in place that you had to have a high enough work capability capacity to cover all of the elements, all of the mitigations that you you bought, right? So that it at least forced some sort of team to run the system versus just having all of the mitigations and no people for your costs. - [Randall] Okay. All right.
So just in conclusion, basically we do recommend, adopting a game like this. This you will be able to download it. We do have a couple printed copies here in the front.
We don't have enough for everyone in the room. I think we have like maybe seven or eight ish printed copies if you want a pre-release version of it. - [Jon-Michael] Of the documentation, not the slideshow. Slideshow you can get on the website.
- [Randall] Yeah. The slideshow are on the website. And if you look on for a Tuesday lab, all of the labs is already on there. You can go and download that set too. But we have the printed document in the front.
We had some extras. We gave it to everyone in that particular group there. - [Jon-Michael] On the high res that didn't take ink. - [Randall] Right? Well, whatever you do choose, and if you modify or, or say we only wanna deal with these certain set of threats, we do recommend an even number. We did, say that okay, could use a deck of cards or something like that.
So if you remove out the king and the queen and treat the ace as a one, you basically have 11. If you take your four suits, so shuffle up the cards. You can do it that way if you don't wanna have, a 12 sided dice or something like that. So definitely take a look at this. It's gonna be out very soon in a couple, well at least as June, it'll be out. Take it back to your organizations, think about your own systems, build one out and then, get a to group together, spend a couple hours.
It helps with the idea of threat modeling, right? You are definitely thinking about threats, how they affect your system and try to find ways to mitigate all those risks in the end. And I think we're at questions with about three or four minutes left. I think. - [Jon-Michael] One last comment, please run through it ahead of time. - [Randall] Yeah. - [Jon-Michael] Because you're gonna find some things, again, similar to.
- [Randall] Maybe two or three times in our case. - [Jon-Michael] Yeah. - [Randall] But yeah, the. - [Jon-Michael] The gaming, the system aspects, those do come out.
The $5 million budget, you torched it or you got 2 million afterwards, it doesn't make it interesting. Yes, sir. - [Randall] Yeah. - [Participant] Might sound like a silly question, but when you were putting this together, how many people around the table were really gamers? I mean, gamers, gamers that played board games and role playing games and those kind of things? - [Randall] Couple, couple.
And they all took our dice. (laughs) Yeah. So we had like a couple tables that still had 12 sided dice when we were done, but no, actually they were, we had a couple tables that were D and D players and all sorts of stuff. Or magic the gathering or one of the other ones.
Yeah, we, it surprisingly happened. Yeah. Quite a few times. - [Participant] Because I have friends that do board gaming edition, that's what publishing, that's what they do.
And a lot of the common issues you're seeing is going through play testing of all their games and all the thing that are written too small, people don't remember icons and those kind of things. So if you have board gaming friends and you're trying to do this, invite them over even then, even if they don't know anything about cybersecurity, because board gaming is a lot of what you're seeing is really a lot of common issues there. - [Randall] Yep. - [Participant] That's kind of interesting.
- [Randall] Absolutely. - [Participant] Cool. Thanks. - [Randall] Thank you. - [Participant] Cool presentation.
- [Jon-Michael] All right. Anyone else? - [Participant] The threats that you guys were looking at, are they all internal or external? Like in terms of, I guess everything you guys (indistinct). - [Jon-Michael] So the pandemic 11 includes insider risks as well.
- [Participant] Nice. - [Jon-Michael] Yes. So there are identity and access management issues over provisioning. For instance, within the deep dives, within those two page overviews of individual breaches, et cetera, those elements are covered and where the threat actor came from, what was actually the vulnerability that they exploited, et cetera. So we try to include with those deep dives, we try to include all of those aspects that were on the threat cards that we mentioned a little earlier. - [Randall] Okay.
I think we have- - [Jon-Michael] Sorry, did I repeat the question? I forgot it was, where do all the threat actors come from? Anyone else? No. Yes. Maybe. Alright, well definitely thank you for coming. Thank you for tolerating us at 8:30 AM in the morning. (Randall laughs) And thank you for being awake.
Yeah. (participants applauding)
2023-06-13 08:44


