CIS41D Unit 9 Lecture: Industries and Technologies for Operation
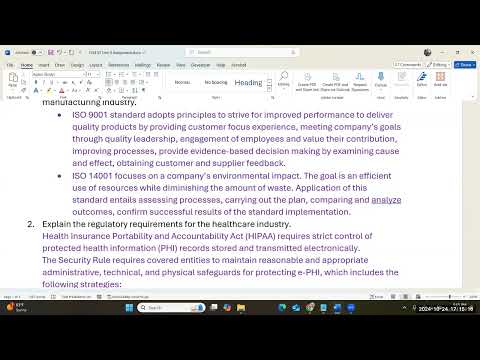
okay so we are going to cover Unit Nine this is actually one of the shorter chapter um in the textbook and my plan is for next week you just have a quiz because we're not going to have class do to Halloween um so the quiz is going to cover from unit 1 through eight and then um we will take care of the second part later um when we come back from Halloween um I'll release the project and we'll go over the project information on what you need to do as far as the project and build out some of the components um for the proposal okay um so the beginning of the chapter it's very business oriented it talks about um how organization have standards and requirements um so this chapter focused on industry specific operational requirement and how that relates to the the security aspect and the technical um implementation or deployment that we have to support um so the first part it talks about health and safety I think this is standard across many industry um including for education or even other type of Industry that's not listed on the page um but as you go through you would see that the regulations is required so compliance requirement um can be um there will be specific details on how the technical setup would be um additionally Additionally you would have um certifications um for the national or International standards and we'll touch on that um and what kind of requirements we have to meet in order to to obtain that certificate so that way um our customer can um have the quality products or service that they need so in the first question um it asks you to describe the international organization and standardization ISO 901 and 141 for manufacturing um this is a big area for manufacturing I think um and then we in support of products and quality of products you would see that manufacturing hi Amy um you would see that there are some uh Baseline requirement in the practices for manufacturing so the iso 9001 standard and this was not fully included in the textbook um this is something that I added to the notes so that way in the case if you provide security support for um the the manufacturing industry you would know there are a lot of them around here so um we would know the type of standard we need so the iso 9001 which is part of question one um it adopts the principle to improve performance basically uh the companies that are certified this area strive to provide quality products based on the customer experience so this is why you see a lot of survey feedback um how do you like our products would you refer our product to someone else um you know you would see those type of analysis or assessment so with the requirement it really comes down to the operation of the company that means that they have to have quality leadership um and also the um the employees engagement in the company is also important so engaging the employees in and include them in the contribution of the company's overall goal um and then they have to continue to improve processes and this has to be provided um in the documentation when you apply for certifications in ISO 9001 and then you have to also provide evidence-based decision making what does that mean um we would have to make the decision based on data um on how certain type of data would impact um you know systems uh people operations and so on so your your decisions is going to come from evidence and we would look at the cost and effect of you know that type of decision so if I make a certain choice for the operation so for example on the technical side we can uh make a choice like upgrading our systems so that way um our manufacturing plant will be able to have more efficiency you have to provide evidence that um you know there's cost analysis there's risk anal is that would be involved so you would see the cost and effect of um those areas so ISO 901 to really sum it up is it's about um really integrating what the customer needs are and how that's going to go into the processes in building better product for the iso 141 this is mostly for uh companies that would um in manufacturing that might have environmental impact so it it really look at how there would be waste um or consumption of resources that would impact the environment and the application of this would inil how we would improve processes um and then execute the plan so it and you probably hear a lot about green it on how we are we should be efficient with energy usage um and that can be a small factor in in this particular area right but overall you would see that company when they produce product there's a lot of carbon footprint um in various products especially with plastic based product um or even paper products sometime can also cause a lot of carbon footprint so ISO 14001 really look at the impact in the environment and how that can uh weigh into your overall production um and then implementing the processes to be able to execute what is planned and then analyze how your product outcome would be is it um better is it not as uh well as what we've seen in last year because in some cases you have to wait in the changes right we have to implement change management and also how successful that would be as far as the result um so there would be some some effort in research and and um prototyping before all of the processes can be implemented for production um and why is this important in it um or cyber security it's because sometimes changing processes CH means changing software um it also means changing storage um and then the practices behind for the operation it also you know we we need to think about how our system can be gred for the better the the greater goal of the company right so all of these elements are important and um when you look online about manufacturing and isos there are a lot longer lists um these are the two more of like the specific on the more General one I omitted some of the specific ones so if you work for a company that is um producing Steel or or you know having um a a a steel plant that processes steel to make tools or other things there are specific ISO that they need to follow um for example like the materials um certification so they have to utilize quality materials and certain type of material and then when they when they cut the steel sheets or rods it has to be a certain um width or length or um uh thickness um so and then if you look at man manufacturing company that use glass product they have to go through other ISO certifications and how that can impact the technical side of the house is that when you change the requirement in operation you really have to change some of the the technical aspect right in operation like the systems that we use the software that we use um and then be able to adapt the people um the the user for that those type of systems um and then sometime that can also change the the how our Network systems would be our infrastructure the applications that would entail you know um making a better product right manufacturing a better product so overall you kind of have to understand a little bit about the requirements and then in this case if you're obtaining customer feedback right a lot of that is going to come back to data retention um and then you know using applications to be able to issue uh some form of assessment like a survey for the customer and this is what you see like when you go to a a a restaurant or um any kind of things that you buy right on the receipt um it would say we want to hear from you can you please give us some form of feedback so I think in many industry you would see that there are focus in how the customer experience would be and the the products and the services that's being provided but in manufacturing in general um this is an area that we would see for standardization and then for the environmental impact I think overall when we're looking at all industry right we want to also think about how um the the things that we use the resources that we use especially in the it area the data warehouses um the data center that you currently own um or utilize right how that impacts the environment but manufacturing company they have to look at how their waste um can be you know a factor in environmental risk okay and this is where you see a lot of companies are being fined or you know uh have to go through various litigations because for example dumping in uh natural like dumping resource waste into the natural resources um like water ways and other things so um I think that we have this in place to make sure that there are proper control in how products are created and making sure that it is safe and healthy right that's the whole point at the beginning of the chapter and so with that um we look into Healthcare and I think for um the the chapter it really kind of very briefly highlight what Hippa really entails um I included some of the verbiage that you can find from the actual website um when you look into health insurance portability accountability act this was established um and been modified over time I think the most recent modification was 2020 um and so this allows um or requires Health provider or organizations that hold health records um making sure that it they protect right your personal health records and this is critical um because health records is really unique to the individual and with that we would require data privacy so this is a big area for many organ organizations um even when you're looking at non Health service provider like Hospital right um but if you looking at like an institution like education institution they do have have health services so therefore they also have health information um or companies that you know have health records of the you know like tech companies sometime that they would provide services like U mental health support um um so they do have that type of data or even insurance information right so that is critical in how we protect it and um the Baseline of this so I I I um you know there's an emphasis in for me in this area quite a bit right um in how we would protect the data with encryption we want to make sure that all the communication systems is transmitting data in a secure way so it tells you here that it is there is a strict control for protected health information so whenever that there's data leak um usually you know after the reporting process there usually uh some kind of fine um if you're not protecting your data appropriately okay so we need to make sure that things are stored properly like data that is being stored and then for the data that's being transmitted or in transit that needs to be encrypted and it needs to be transmitted in the secure channel so the security rules required um The Entity to make sure that there are Administration right in Technical and physical safeguard of health information so if they have paper files right like when you go to the doctor usually if the office doesn't have a tablet for you to use to fill out the information you're required to fill out a form and that form is then being scanned into the system so your health information has to become electronic however how they maintain that form that you completed is very important and that's also physical safeguard right they cannot just throw it into trash and then it becomes an element for dumpster diving so overall we want to make sure that we have the technical the administrative and the physical safeguards and what does it really do it's going to hit the the cyber security area it got we going to make sure that it is the data has integrity and it is confidential for Access so it will be to the individual right and then when that data is being transferred to other entity the individual must authorized the data to to be transferred and then the data needs to be available for the people who access it like Physicians nurses right service providers um and then even insurance company or the patient themselves when they're requesting records or accessing records online right it has to be secured so how it's maintained and transmit and with this we have to take a look at the infrastructure um like the network that that we're using the systems that we're using software and Hardware does it have the capability to meet the compliance right um for Hippa and then we want to also have anticipation of threats so that means that you have to do vulnerability assessment by the Baseline in the requirement so you have to have Potential Threat information analyze and then you also need to make sure that your your information and your data has integrity and so with that we would look it into technology like hash algorithms um and making sure that we encrypt the data and then the access level to the data so permission control right and then so there are various layered approach that we want and how we are looking at threats um internal threats and external threats that's important okay and then we for the security rule it requires that you protect your data against um impermissible use or disclosure right like data leak um breach um or even accidental disclosure of information right people might um accidentally send a list um to someone else um that is not not supposed to have the perview of that information and so on so we want to make sure that we have precaution measure and it should be a proactive approach in security we look at this and we would say so there's a lot that would go into this area right outside of permission control and access control you also want to have things in email systems or your email servers um also checking for malware that could be damaging your data or uh C circulate your data elsewhere um and then be able to make sure you train your users so there are a lot of elements for security in this area and then making sure that we fulfill compliance okay there is a website that you can also visit to I think I did that with CIS 27 right and other classes to kind of show you how frequent or how many organization actually have Healthcare information leak um and it's very common that you would see that right whether it's accidental attacks so those anticipated threats needs to need to be assessed and it you have to look at the risk behind that hi how you doing any question okay so for the next section um it talks about public utility regulatory requirements um and you know for our notes we're just going to focus on some International standard but not uh and Regulation and then for the majority it will just be um oesb United States base so the public utility their requirements would be the PPA public utility regular policies act and this is mostly to control how pricing um and the reliability for Power Generation Um or resource generation and how it's delivered so it aims to look at the domestic energy and renewable energy so when you're looking at that electricity in general right um how the service provider like Edison or other companies is able to offer uh energy to the household or the business and then also having programs for the business or the household to generate their own energy to connect back to the grid um as the shared resources or also right the the compensation and the price that we have with this organization so the enforcement of this particular rule or the requirement um is really coming down to how much they charge right um of late you might hear that a lot of people are saying um public utility company such as Edison have been raising their price because there's a higher demand for energy um in an Enterprise environment you would see that energy is one of the higher cost item um that the companies might have to pay um so and because all things Electronics utilize some form of energy whether it is battery based right or through your um electrical systems so the utility company they have a requirement on the charges that you know like there's a range of charges that they that they can follow so it must it must be fair and it cannot be discriminatory okay so that means what they cannot charge One customer a rate and another customer of the same tier right a different price um it has to be fair and it has it has to be non-discriminatory and then there has to be control in how the prices rise and I don't think they ever fall they just continue to rise because there's higher demand for energy and how it would if in the case that it reached the maximum the cap right so in in the case if we have inflation the economical um ground change and so with that we would see that there's price changing so so some of it you know there is an a a ceiling you can say on how price can or the rate can can reach um and not exceed a certain amount right so they have a cap on that otherwise you're going to have a lot higher rates and you don't see that across all the countes so so um we're fortunate that we do have this regulation in place um so that way you you know even though electricity bill is high right it's not extremely high like what you see in some other areas um and you know and they talk about how sometimes it is some cases it's state based U but federally you would see that they have to have the requirement for the federal based on the the regulation that's stated okay but then there are cases that you know like for example in Hawaii if you're looking at a lot of the utility company like gas and Power in Hawaii the cost for that is a lot higher than what you see in the mainland States like if if you compare that to Florida or some of the coastal State like us California right Hawaii rates are of tremendously higher um the the argument behind that is the cost in Hawaii overall right and the the cost in support and maintenance for the system systems on the islands can be different than what you see on the on on the mainland but I think you know with the state support and and some of that comes back to the political issues um and who's in leadership and so on so what you see is yeah there is something that's federally regulated and then there's sometimes there's exception because there's state law that allows certain things right and I think that mentioned uh that was mentioned briefly in the text as well but um you would see that across with a lot of different type of Regulation so here it talks about energy sector um and then you have the environment Protection Agency your EPA um who really is you know in my definition they're supposed to have enforcement to protect the consumer uh based on the compliance requirement and then you also have like non- Monopoly requirement where you do see that there's certain service provider in a certain region right um but then they cannot be across the entire State or the whole nation right so you do see that they can be some of the primary because they are dominating in some area but they cannot be across all areas right so they have a lot of that uh for communication utility based companies too and then I think I touched on the quality control for the I that's using ISO for manufacturing so you can refer to the notes if you want to read a little bit further or you know more in details so for four um we're going to move forward and we're going to talk about some of the technology right I think the beginning part of the notes it really goes into like um specific industry but if we're looking at Industrial Systems or or man in manufacturing or even at the utility company we often see that there are embedded systems right um in computer science and engineering they have to dive a little deeper on on how to engineer these systems and how to develop applications or write instructions for the eded systems and to really understand a little bit better about the embedded system an embedded system is simply a computer system that has instructions or software that's designed for certain processes okay and embedded system can be used for farming it can be used for manufacturing it can be used you know even uh some of your household systems can be embedded systems now unlike the microcontroller embedded system usually you know overall when we're looking at the technical aspect you would see embedded system would have like operating system or a more full- fleshed software where microcontrollers are specifically executing a certain set of instructions only so when I'm looking at embedded system it could be you know the red box that you use to rent your DVDs or whatever and those are diminishing because I think we're doing away with the optical dis or the coin star that you use to deposit your coins um embedded system can because it's really designed for that specific purpose right coin star system is only for you to deposit coin or exchange your coins for you know bills money in paper form okay or digal money ultimately so if you think about that embedded systems is really designed for certain processes or certain uh purpose so when we manage these embedded systems it's best that we put them on a network segment and we should manage that Network segment separately um because depending on the use of a embeded system so they can be for for full automations um or they can interface human beings so something like the kiosk that you use at the airport or train station or bus stations um all the way to what you see in the supermarket like Coin Star or the rental kiosk that you see right um and that is mostly for self-services purposes but you have AO fully automated system that that's used in manufacturing in uh Supply chains and a lot of things so what we have to do is on the network environment we got to make sure that these systems are segmented that means that they're connected in their segment and we need to manage their segment to support their purpose and their goals so any questions so in security when you're using things like switch uh routers security Appliance like firewall they are a form of embedded system right the firewall its job is to filter that's it right it runs embedded Linux or command line in the back if you're looking at Cisco it is really built around embedded OS so um some of the commands that you see is the same thing in as in L command like IP address so embedded system normally you would see them is Linux in the back whenever that you go through drive-thru and you speak into the kiosk and and you you know and they punching in your order the ordering system is an eded system um if sometime if you see like if they have malfunctioning system you see it boots Linux in the back right so the interface that you see is just an overlay application so that way the the the the person who takes your order they can tap the button on screen or the button on the keyboard to input your order cashier system is like that too um many of these things that is around us all the time is really embedded system and we're just not aware that that's by definition what it is so let me go to okay um there's some information about facility services and we'll come back to this when we talk about scatter or um your system to manage build buildings and things or the resources in the building but if you look at um page six and onward you would find more information about embedded systems and they've been around for a long time um I don't you know a lot of the things we use is just an improvement of what was in the past so over 50 years I think that our embeded system has changed um in how it's used and the purpose for these systems have also changed based on the need right of the users of the consumer and with this we will come back right we talk a little bit about how we would manage that in it and we'll come back and touch on so the security behind this because they are embedded system you got to manage them as a system as a host on your your in on your network and ultimately part of your infr structure so what you see is that you got to because they are specific to um certain objective right you have to think about their functionality and how that plays into the operation of the company and we got to make sure that we protect the security so the processes is not intervene then we have Internet of things and this is a lot more popular now than it was in the past internet of things can be many many many things from Alexa all the way to um your smart devices like your smart TV so um now question five asks you to provide an example and that you know you can add more to it internet of things can be your wearable devices like your Smartwatch but if we're looking at like household appliances and and um you know or Electronics we see that a lot of them are internet updates um internet of things could be your security camera that's connected to your wireless network or your wired network but it can also be your smart TV your smart thermostat your speaker that you can provide voice command to right your a smart speaker smart refrigerator and many things that we use so as long as they are a system that can be connected to the internet to sh there or um to have their data be available for Access for various reasons then they are internet of things so to support this um from the security side the number one area that we see is for more patching the the downside of this is it really depends on how the manufacturer produce these systems right some systems are more maintained or updated than other others um and so we can't assume that out of the box they are fully secur right and many of them will promise encryption and secure communication you have to take a look at the technology that's built within the protocols and the services that's used so the number one area that these systems fall down a lot is going to be your wireless um how wireless access is uh security measures are whether that's in place or not even if um you know if you use a certain technology or encryption for the wireless we have to really ask is this inscription going to withstand you know the the type of threats that I'm going to be facing so outside of home if you take this aspect into a business environment like a a hospital right or a manufacturing company or like something like uh logistic um or like FedEx UPS you see that you know Internet of Things is being used all the time this the hand scanner that they use to deliver your your packages that was so outside of patching we we want to see how we can protect the the the connection and the interconnection of the system in our infrastructure in the Enterprise and system hardening is a lot more than just updates right uh you got to make sure that you know you protecting it from malicious uh software or malware you also need to make sure that you know authentication and everything is also in place so system hardening is like a broad spectrum of things that we would Implement for the basis of the protection of the iot device and I think that there's just one chapter that's dedicated to that right we talked a little bit about mobile devices last week um and some of those you know things what we carried into the iot's area so for the next area um we would see some information on system on chip and this is s so and this is basically a CPU memory storage and IO so it is a Computing system right in a in a small format or maybe a compact way so it has to have some way to be able to interface so when you have input output it need either interface with the human or interface with other systems okay there got to be some form of internal storage and also temporary storage and then it needs to have a CPU so if you're looking at some example for these SLC can be your tablet it could be your smartphone it could be your uh fire stick right because there is an interface uh some form of input and output for that you got signal input with the cable and in some cases there might be other devices that you would see that would fall under that category so when you're looking at so the the processor that would fall under this area that would include your Apple M1 or M2 right and then you've got the armm processor so armm processor is in a lot of your Android based devices um you know from the tablet that you use that is Android all the way to um some of like the smart speakers and things that you have so these are the the some of the example for your for your processor like if you think about like the Roku stick or the the fire stick like the the the Fire TV stick right that you attach to um HDMI connection and and things like that it has a processor it has storage it needs power um when you turn you when you connect it you have a software interface so it is a full Computing system it's just in a different form factor um yeah many of those would use some kind of uh sock like this right I used to be fascinated with um various more compact based uh type of system that you saw so whenever they would come out with things like Intel stick I would get it and you know you it runs full uh embedded Linux so you can boot it um very similar to what You' see with live Linux USB where you just plug it into your TV and you have a computer um and then you can connect your wireless mouse and keyboard and then you can use it very similar to what you see with Raspberry Pi and other things okay okay then um the next question is going to lead us here in the application specific integrated circuits circuits so when you're looking at the computer system motherboard is a board of integrated circuits right um I's is everywhere in electronics whenever that you see even in toys whenever that you see like a board um that's attached and it would have some form of instructions um that incorporates integrated circuits but as asic's um they cannot be reprogrammed so when they are built they're really built with a specific program for a specific purpose okay so for example I go and I buy a toy for a kid uh let's say a little little puppy that barks right um that particular toy integrates Asic okay and I cannot take that chip that's integrated inside the toy and program it or modify the instructions for it um it it it it is written to an area of the storage where it's not programmable okay the old cell phones that you see right those are not programmable they are really used for a certain purpose right um if you're looking at your digital watch like the old school watch like not the new Apple watch right the digital watch that would have um you know just the number that you see um not even in color so in that case when you're looking at these systems you would see that the a asic's they're really m for a certain purpose but they they can't they can be vulnerable because if they're built with flaws it's hard to really fix that problem right um so the reliability behind it it's really depending on the manufacturing company um on how that's used but there is a wide range of Asic that we use for different industry so if you're looking at at Aerospace um if you're looking at Transportation there are a lot of different asic's that we use um and it's made for a specific purpose so for number six it asks you to provide some examples for Asic application specific integrated circuits so the application is really made right uh for a certain objective for that that chip set and how can a vulnerability be remediated with Asic so the example would be your electronic toys right the next time you go to a general store like Walmart Target right you look at the electronic toys um and and you would think about ASI like a toy car right the RC cars um the helicopters for the little kids or even like you know talking um stuff animals and things like that and then in some cases you would see like Bitcoin mining systems so we mentioned that the vulnerability cannot be remediated for the existing Asic so once that's built right that's not modifiable that's not reprogrammable so in order so let's say that if my company use a a a system like this um what can I do to fix the vulnerability the security vulnerability replace that system we have to retire the old system and re replace it with the new system so to really fully mitigate it you have to have a replacement so that means that a new application has to be created for a new Asic system okay there's no way that we can go back and Patch it there's no such thing as patching for this okay so it is just a one way so this is why you do see some versions that come out right like if you're looking at things like we can just relate like uh electronic toys for kids you would see that you know maybe last year the version have some bugs um maybe it's it's you know it's not functioning as it should or it doesn't last um normally they would reproduce the toy with a version to and they have to adapt a new asic's right so the the next line of production is going to be um the Next Generation system with a newer application any question regarding asic's okay so I'll have you go through this link um you can control click it and it take you to an article by spice works and it talks about fpga you can see some information in the notes but it's very brief um this is real programmable gate array and it gives you the breakdown on what it is how it works so that way you can have a better understanding of what it is so fpga is a form of integrated circuit it is an IC right and it is made of semiconductor material and semiconductor goes into a lot of things your CPU right if you buy a video adapter there's semiconductor that's integrated in that so integrated circuits but this is field programmable Gates array so the difference between your fpga and Asic is that Asic cannot be reprogrammed whereas fpga is programmable so when you let's say that your company uses fpga right after that it is purchased or acquired um you can you can uh program it right okay so as you go further it talks about how um like the the common format for it so how can you reprogram it well you would have some form of input and output interface so in this case I talk about pads and it uses the programmable logic block so the flipflops memory blocks is utilized for the memory components so it uses things like logic blocks and so they do have microprocessors for your fga and so to answer this question you would go down the article so at the beginning you can Define what that is right we we already answered this question in comparison with this should be sorry there's a type of Asic how is fpga different fpga is reprogrammable where Asic is not so how what kind of language do I use to program afga right so as you go down uh I think I can show you the section yeah so here you should see it talks about VAR log and vhdl so very different than what you see in like your regular so when we when we talk about highlevel programming a lot of the times we would go with like cbas language and so on um and fpga it's been around for a long time so it uses these two languages and it talks about how a common language for afga is your vhdl so very log and vhdl the co the programming languages and um it is a way that we can program the integrated circuits to execute certain requirements right to do certain things so here it talks about how you can configure the logic block um I think it talks about how it carries that and treated as cell so it works at uh with the control logic where and and we will get into the programmable control logic which is uh the next section okay but it also use multiplexers so you do have information so at the com the low level you have the flipflops the gates so when do we see Gates we see gates in computer systems right um this is when you can have applications in when you're writing a loop in programming language like if else right if this happen and this right it's going to have produce a certain logic so logic gates are really designed for that is to give you logic and so that where you can write the application that you need so it still have the logic but it just it's structured a little bit different than some of the other integrated circuit system you can have it interconnected or connected and there is programable routing so for the next qu few questions it says how can fpga interconnect you need to refer to this section of the page right right so it talks about using semiconductor switches for interconnection for afga so it uses a form of switches for interconnection and these switches are programmable switches and then you can also set routing path so it is able to fpga can to connect with one another right and then can communicate throughout so there are programmable routing hello so we see these sections [Music] for d and e and it asked you why is programmable routing used for fbga so here it mentions that um what was it in the design it's hierarchical that means that it carries top tier down right you can connect um the gate arrays to communicate from top level down so you have hierarchy But ultimately the goal behind programmable routing is for density and performance that means that if you have many AFP gas right we're able to reconfigure or change by programming the the routing process so that way it would be able to handle more loads or or you know the density for communication so look at this paragraph for the last question okay then we get into plc's and how plc's is used with scatter let me get to that section so one of the things we want to also note is uh fpga does have cves depending on specific uh type so you do have vulnerability and so we want to make sure that we looked at the vulnerability and how that vulnerability can be remediated and it says around 70% of the attack against embedded system and integrated circuits are performed remotely Ely that do not require authentication and exploit to be exploit successfully so that means that because these these systems um are a little bit more simplified you don't have a way to log into it accordingly or you don't have a secure authentication process so ones that they can connect to that system they can likely exploit that system so uh so how you allow connection is also important so that means that we have to look back and we wanted to make sure we update the firmware to protect right um to remove any kind of bugs or vulnerability also we want to look at how these systems are interconnected okay how it's used in our infrastructure and there's example and it talks about star bleed so physically you would see something like this okay so ic's are ICS or icc's are integrated circuit systems and it's used in Industrial Systems and also so for manufacturing and process [Music] control now when you're looking at scatter scatter can be used for a lot of things like controlling lights so for example like for a campus like this um we want to set up where lights can turn on or even parking lot lights can turn on at 6 or 7 p.m. when it gets dark um or controlling thermal that across the buildings temperature um so there are many things controlling utility use um or even production for manufacturing so you would have system that s that supervisory computer these are the the controller right that manages all the other components so when you looking when you walk into like retail stores and things like that right they have a system that control the refu duration I think that they're doing a way with like the individual units right all the units are interconnected so that way we can monitor like the temperature like let's say that I have Frozen sections and I have refrigeration for milk and dairy and other products um so you you might have something like that or even in the warehouses um you might have like Refrigeration warehouses that require supervisory system so you see a lot of that in logistic area in manufacturing in supplier and so on so this isn't a good example of that so you have the HMI which is a way that we as human can interface with the computer that controls the other element of our facility or our our process right so in my plan I might have equipment so let's say I um for my company my company does oil drill right um You would have sensors you would have equipment you would have Motors you would have generators you would have tools or even producing steel um so in manufacturing equipment you might have sensors and things and Those sensors are controlled by programmable logic okay so I uh on the plane one time I was flying somewhere and I had talked to a a technician that serviced um Refrigeration uh systems right and he goes to supermarkets to do that when we started talking because I used to service the cash register or the the it part of the the the supermarket so whenever that you walk up to the cash register when you're using transaction system I used to service those long long ago um and then he tells me that he service you know the the refrigeration where you go and you get your ice cream and so on and I asked him I said you know uh what kind of skills does it take to do that and he said well sometime you got to connect it to the network um they are programmable logic systems so um you know you just run the the instructions and it's cbase so I said okay I understand so you would see that equipments and things that are controlled by PL C's are generated with instructions using C based language or or that form of instruction sometime they use shell based stuff too but um things like you know uh check mon alert when temperature would go down so when you have system that goes down right it would send alert notification to the supervisory system it's saying that that refrigeration unit is down right or it's not up to temperature or there's leaks and so on so that way there's a way that they can dispatch the technician to come out um normally that gets contract out to the vendor who provides the refrigeration service I actually know some of the engineers that uh worked at the plant near Ontario that produce so when you go to Starbucks all these beautiful glass case that you get your cakes and all your pastries from right it comes from uh a national company but they have a close by manufacturing locations so you would see more modern and there are a few of them in the nation that does that right but surprisingly now that you see that all of these are are connected so P plc's right uh how they're used with scatter systems PLC receives the information like from sensors and we can use like temperature as sensor uh temperature for cold and hot we can also look at that as moisture um so in the case if you're looking at things for farming um it can also detect like soil moisture and and other things so they would plant that um I was on a a a project with another company long ago they were implementing um Smart City in some part of the world right um so when you're looking at Smart City they would have a lot of the sensors things like for train tracks um so in the case where if there's human that's trying to lay themselves down on the train track right they would have some form of notifications uh to monitor that or Wildlife that cross because uh when you tear down some part of forest to build out the train tracks the engineers they have to go in they have to take a look at how that can be safely implemented into the environment um so and then you know from kiosk and things and communication that's integrated sometimes you would see that they would have control like that for transportations and and so on so POC program logic controllers they're really used for sensing for actuators like for movement or even some robotics area and then also for punks right like for water systems and things like that and that allows some other automations now the H the hmis the hmis are really just a way to for the human to interface with the actual system right it it is a way that we can communicate or utilize the software to be able to to uh modify the what we want I think some of them they waited a little while longer to have so third or the say [Music] okay and then the historian systems so I have AA database is a database logging systems so whenever that you have controllers right uh it generates logs so when you have sensor instrumentations or other controls the logs is going to go into the database and that database is called historian the way that I remember this is because there's historian that's data historian so it gathers all the data and history of the system so if you have like uh sensors with plc's um then you would it all that data is going to be the repository of that data is going to be in the historian system now now this data is then interpreted and analyzed so that way you can change your processes so we can say because of the instrumentation so if we're looking at like utility company or a company that provides like resources like gas and oil um when they drill for that right um they will make adjustment based on the censor so the the data is being analyzed and then it goes back to the engineers and the engine they would modify the process for that particular you know to improve basically so that's the whole point and why is it important for us well this data is important because it really tells us how the performance of the sensor in the instrumentation system and if it falls into the wrong hand right um that can be uh that can cause some damage so when you're dealing with the grid right gas system stuff like that so hmis is here right supervisory system and it talks about how PCS is integrated is there and and when they referring to OT it just mean on the carpet so that just means that like uh the industrial type of of um organizations or systems there okay so one of the things that you need to know is POC do not use your operating system like Windows or Linux or Mac OS right they have their own specialized os's and the instruction to go with that okay so an example of that is this so you got the Seaman po models and then it talks about historian here so latter logic latter logic is a programming language this is used for Relay based logic um think of it like the latter you have to go from the first step to the Second Step so it's a form of um relay right in the logic and the way that it's designed is rung or ring rung like a ladder and then it's going to go top to the bottom and then left to right why is that because as human we design things that really represents us right we see things when you look at things you normally look at top to the bottom and you read in in uh Latin based language is going to be from left to right right um in other part of the world we we read right to left so it's really the latter logic process is designed right where it's going to execute from top to bottom and then left to right so you would have like sensor inputs for example like this sensor input is for quantity and then it's going to report to the next it's going to be um clear and then it's going to so if you think about like manufacturing even for conveyor belt um you know when you when you're looking at conveyor belt where it's going to open up let's say it dropped a box and then somebody on the conveyor belt put things into the box and then that box get grabbed right by the actual and then that gets moved into something else that could be a robotic arm and then and so on so all of that is really sensors reporting out to other sensors um and then ultimately so it's going to be sequential until it gets to the output three right where that exor open the gate so when you're thinking about shipping and receiving uh areas of the the warehouses it actually Ed something very similar to this so latter logic sometime is um fully integrated for automation purposes so basically the logic cannot occur in the middle right you have to go from the start which is the left to the next step to the next step so some sensor has to be activated now the things that fall down right when you have things that are backed up if you're looking at conveyor belt uh is when right things don't happen in the first stage that activates the second stage because now then you get a a bunch of things just get backed up from from the first part so to troubleshoot that they would go back and they would go to the first step and see why that sensor is not activating or not reporting out um and so on okay sorry I have a little bit longer for the historian but you can grab that information from bye from the the that section but I forgot to mention that historian system is the three components and you can find this in the notes it collects the data so there's data collector and that data came from the programmable logic controller your plc's um and devices right so if the poc's is connected to um you know your network at large then that data is then being sent to the historian system so it has a way to collect the data so that means that it has to CU those system right query then and the their their status and whether they have things to report or not then you have server application or software um that stores the data after it's collected because it's a database it's going to put in like for example system a reports at :04 p.m. this right s B report at 50:5 p.m this so it would put that into the database and then um from a client standpoint there would be another software that would be used to look at the trend of the data right so when I when I look at that I would say okay well my machine is uh in this section is performing well because you know there might be you know specific specific instruction for those machines compared to other machines and then for lad logic so it is a programmable language you can pull this from the notes up on relay based logic it's used for electrical electr mechanical relays so you are going to have mult multiple inputs or signals to perform a certain function and to design the circuit board the engineers would use ladder logic to activate the mechanical relays so we would say top to bottom and then left to right and following that we would have information on safety instrument instrumented system your Cy sis and how it's used where it's use this is a fail safe system in the case if there's lifethreatening or there's condition for critical environment gas station has this right or when you're looking at nuclear plants they would have this this is where they can turn things off right you've probably seen movies with spaceship or a certain area where they can just pull the lever and everything shuts down right that's a fail safe system so that's a Cy okay um so the purpose of this is it does a reset and on the spaceship you normally see that it has a countdown you got 60 seconds to get out of a certain area or everything gets closed and turn off right and that's a self s uh fail safe mechanism that they implemented and in the case if there's things are threatening right like things that explode or uh you know it it would combust um and so on so that means that there would be sensors that's implemented could be temperature sensor pressure right um you know thinking about if you looking at like submarines or even outside of you know now we're going to go from the sky to the ocean right yeah there would be sensors so we would look at like water pressure air pressure things like that and the these Pro programmable logic controller how that's managed so when you're looking at things things that we send out to space um like the Mars collar and things like that but whenever that we house human being on it like a spaceship right we want to make sure that we protect the the live form that's inside it so normally you would see implementation of fail safe but naturally here on Earth what you see is power station has that refineries for petroleum or or gas uh gas production for Mining and other instr uh industrial environment okay next is going to be your heat and air conditioning system heat ventilation and air conditioning right HVAC um why is HVAC important we had breaches through HVAC before Target was the the big case that we've seen in the past um hbac is controlled with automation right um at home we can have it automated through our smart th stack right if you're using Google Nest that's a form of centralized system that can be controlling others which is going to be next but h fact in a facility like a college campus or in a big Enterprise you would see that you you would control that through scatter through a supervisory system and so for the building automation system this is known as Bas or you can also set up uh digital control through the dedicated Network they are all networked and we monitor that the reason why is in some environment you have to have a certain temperature like your data center your server will overheat when it's too hot right in semiconductor plant when my parents used to work it is a dust free proper environment you cannot have things that be floating around and it has to be cooled a certain way temperature has to be controlled and there's proper air flow right so in some environment in order to have production you have to have proper agback so and you've seen that with like a lot of the manufacturing too like you have to have ventilation for the dust to fly into a certain area otherwise you're going to have contamination right so um or E even in the chemical related environment so the products that we use from beauty products to things for household products right some of that you would we would rely on HVB it is a lot more important than what most people think of it um we're like oh okay it's just going to cool down the building well it's more than that you keep the moisture away the heat away or at Bay right and in some cases you have to neutralize the environment with the proper temperature because bacteria can grow right food production there's a lot of things that can be involved um or even in the warehouses when we're dealing with refrigeration and such right so that's important so remember put it on a dedicated Network and monitor that segment of the network we cannot right based on target case put it on a regular Network because that's how they can get in normally these systems are they lack a lot of the security control so you want to make sure that you control it through a segment a group an area of the network okay and then um some of these things you're like why are we reading about this well they have vulnerability issues okay so let's talk about can or controller area network bus this is used in car industry automobile production I'm sure you've seen or heard about car being attacked right someone remotely controlling the car this is why okay so we need to know about this a lot of people say oh it's because of the iots it's actually because of the controller bus okay so can controller area network bus what is it right and where where where's the security implication behind it this is a protocol that is designed so that way you don't have a lot of cables connecting or wires hanging out everywhere okay in the vehicle because in wire management number one that reduce cost second right it it is a better design for the the automobile you don't want things to be just hanging around and and and production can be difficult so what that does is it allows this think of it like a Channel or a location where things can be communicated with multiple signal right and it's like a shared bus so think of like your computer system when you plug a device onto a motherboard that's a bus one bus right but the way that they Design This in cars is that that one connection can be shared by many devices so not just one to one but multiple to one because remember we want to reduce less connection physical connection so we allow that logically to have to receive multiple signal on basically it's a shared bus so to share this you basically assign priority first come first serve or based on the need of that device so for example when you turn on your car right your computer activate but your starter also works right and then other things would work like your crank and you know all of these things that makes the motor runs okay so that means that there is priority in components of the vehicle that would take place and it also have a a CPU so that CPU the the processing unit is going to be the controller for the timately the car so that means that you can have multiple devices or nodes send information at the same time to the bus and then the the highest priority of the device is going to get served first okay so p is really designed for that now the flaw of this is it lacks security so that means that there can be tampering because remember that instructions is sent to the bus multiple at once right and whichever the half priority is going to be served so man in the middle can occur because some some of instructions can be submitted to that bus and it can be executed for example right uh apply brakes while the car is moving even though you don't tap the brake pedal right so through communication they can intervene and be able to perform a manin the-middle attack that means that just uh interject with the code submit that to the bus and be able to execute your car attack another area for I'm going to move this down so you can see both sorry and yeah it's kind of long um but that's okay another security area that we need to look at and the technology for the automobile industry is the mod bus so mod bus is is a messaging protocol I think this one uses uh TCP and it uses uh in the integrated system for seral communication over cable ty
2024-11-01 11:55


