Azure Active Directory cloud authentication doesn’t just mean “sign-in” | BRK3194
Good. Morning everyone. Welcome. To the session so, I've, got very short space of time 45 minutes I love, a little bit longer to, go really deep into things but, what I've tried to do is just go through and. Look, at the sort of authentication, sequence, within Azure, in. That time so what I want to show you is, number. One how, do we get here, how do we get that log, on prompt and what are we actually being, asked, for at that point in time so. You know we've arrived here how do we get there what, are we being asked for and finally, how we can tighten up security on, that so, how we can enhance security, so. Three I think really useful, things to know so. Number one starting, off how, do we get here we. Get here because, an authentication, sequence. Has been triggered, and it. Could be triggered in lots of different ways but if you think you'll go to the portal and you, want to log in to the portal that's going to trigger the authentication, sequence, if you go to a SAS app and, that SAS app may be in. A partner, somewhere, that's, going to trigger authentication. Sequence, so. What, it's actually happening, is when we hit. Our application. What, the application, is going through is first of all is going to find out if you're already authenticated and, if you're authenticated. You will have a session, token of your like session cookies. But. If you don't have them what, it's going to do is it's going to say you're not Linda kated you, need to go to, an authentication, service, that I trust. Well. If we've got an app deployed. In Azure ad the, authentication, service oaths v is a zero ad and we, shoot up there and we. Shoot up there with a, authentication. Request, string and in, that string, in a very simplistic, way is, please. Authenticate this. User to. This application, having. Authenticated. Them please, return. The results, back to, this, URL and, that's. In its simplest, form now. Notice, I haven't, mentioned the. Authentication. Protocol. And it, really doesn't matter, what. I want to look at is what Azure is going to do with, the authentication, protocol, when, we shoot up to a zero we will shoot up to an end point if it's, the ws Federation, endpoint we're, going to be using WS veneration, if it's, the sam'l end point will, be sam'l, and if, it's the authorization, endpoint, it will be open, ID connect or two. But. The, string, is still very similar, regardless, of the protocol that's in use it just, becomes slightly, more complex, the syntax, is different depending on the protocol now. I've arrived, at zero, now, as here it's going to say is this, person authenticated. If you, are you, already have a session, token', or cookies. I like, to prove that you're authenticated. So. If you're, not authenticated, azure is going to prompt, you to do, the authentication, and having. Filled in your details, and will have to go through what, those details are and how we can choose different authentication methods.
Once, You've done that what. Azir is going to do is produce, a. Security. Token and that, security, token, is proof. Of authentication. Of the user to, the application. And again. It doesn't really matter if we're, using WS. Fed we're using sam'l, it'll be a sam'l, token, and we're using Open, ID Connect, or - it could, be a number of different things including a, a code, an access, token an ID token, and. Maybe a refresh, token but. We. Get a token that is proving. Authentication. Of the user to the app. What. If you will also do is give you back some cookies, and those, cookies, say you, are authenticated. To Azure and those, cookies, actually, hold how you've authenticated see. If you authenticate, it with a username password they. Username password, cookies so, if you go back and hit as here again and you're, quite do MFA, you, will be prompted for the second factor. Having. Got those we, then return. Back to, the application with. The, token. And what the application will do is it will consume, the token, it will validate it, and then, once, it's validated. That token, it will return. A page, and some. Cookies back to the user so now the user is authenticated, to, the app next. Time the user goes back to the app they don't have to go through the authentication. Dance again. Now. Totally. Different model what, do we have something, which referred, to as a Native, Client or a public. Client, typical, example, of that is Outlook, all, right so, what happens, we've never logged in before the, first thing that's going to happen is we're going to be prompted. We're. Going to be prompted, to put in our credentials, and it's effectively, opened a browser, all, right we're being prompted with that it's a redirect, string up to us here alright and what. The client is doing is setting the redirect, string, and it's. Going to be using, Open ID Connect, and that what I was to in this particular instance, it's please, let's indicate this user to, this application. And return. What. It's requesting. So what is it requesting, back what, it needs is an access, token it. Also gets a refresh, token as, well that. Access, token is used. To. Communicate with the backend API so. We're if we're talking about Outlook, as a client we're, talking, to exchange, all. Right and we're. Talking to exchange online and, what it will do is it will use that access, token it simply. Places, it in the header it's a bearer token, it's sent through in the HTTP, request to the backend API and. The. Backend API. Validates. That token. And on, that token, will be the identity, of the user and a, scope which, is a permission, for, the actual. In the, access token and what the access token is it's, about authorizing. The front-end, to, gain a limited. Amount. Of access, to the backend system. Okay, now, that access token has a one-hour lifetime, and, when. It expires, we're. Not going to be able to get access anymore. So, that's where the refreshed, can comes in so, the. Client, what it will do is it will check the token, if the, tokens about to expire it says ah I need to send the Refresh token, up to zero and say, please can, I have a new access, token right. Now. If the Refresh, token, for some reason has been, revoked, and it could be revoked by. The, fact that you've changed your password then. At that point what's. Going to happen is going to say no, you can't have a new access, token so. What, we'll do is prompt the user, for. Credentials again, all, right and. Every. Time we, use a refresh, token then this is really really key is what, we're doing is we.
Are Complete. Evaluating. That, users, authentication. So. Every time you send a refresh token up, which is approximately every. Hour, then. At that point we reevaluate, conditional. Access so. Having a conditional. Access we. Can decide whether, that particular user, that particular device etc, still. Is allowed, access. So. That's, the the great thing about the, use of the Refresh token, is we continuously. Re-evaluate. So. It gives you an idea of, how we get, to a signing. Prompt, and what are we being asked, for with, the sign-in prompt, the answer is it depends, it, could. Be that, we need to supply, the. Username. And as, you, will consume, the full user name so John at XYZ. Comm consume. The lot it could. Be that all of 0 needs to find out is, what. Domain is this user from and if. They, want it's worked out which domain, the users from it can, do an authentication. Flow, right. In which, case what, we can do is in, the request string from the application, we, can say please authenticate this, user to this application. Return. Here and by, the way this, user is from this domain we, can add at the main hint. And if that's all that, this login. Prompt needs is then, what it can do is it can automatically. Flow. Without. Asking, the user to put a username in. We. Could choose a sign-in method, and the sign-in method, could be that we would like to use Windows hello or now, we can, use a Fido to key alright, so we can choose to use a key rather, than actually, identifying. The user and. Maybe. Being asked, for a password, passwords. We, may have to put in but hopefully. We can get away without them. So. How, do, we actually authenticate. The user and again, in various, if we've got a cloud only user then. The username, and the password. Are put, in and actually. Checked, directly. Against, data held, in a 0d there's, no concept, of a hybrid, user, which is a user starting, off on prem they, are purely, cloud based so all of the user's. Authentication. Context. Is held up there in. Terms. Of what. Username, reviews we need to use a verified, domain name now, when you create a tenant, and by the way tenant. Directory, I'm always asked, what's the difference between a tenant of directory think of them as the same thing when. You are when you create a directory, you'll be having a tenant, name so, John at tenant, name dot. On Microsoft, com that. Is your verified, domain, name for a tenant and then, you can add additional, dns. Names into the tenant, so. Cloud only purely. Authenticated. Against, data held in the cloud in terms, of a password the. Password is. Controlled, by Azure, ad, policies. In terms, of whether, we use a complex password and so on. If. We look, at using. A, hybrid. Identity. Then, what we're going to do is synchronize, our users. From on-prem, up into. The cloud having. Synchronize, them into a cloud we now know that users in the cloud but, the problem is how, do we actually, authenticate, them, what. We can do with, password, hash synchronization. Is synchronized. Their password. From, on-prem. Into, the cloud and this, is where Microsoft went a little bit wrong with, their original, selling of this they called it password. Synchronization, and. The. Chief security officer said. No way are you putting my, passwords, in that, cloud thing, so. It got, a bad name right from the beginning if Microsoft, had actually said look its password, hash, synchronization. Alright, and actually, explained, right, at the beginning they've, got a really good paper on it now but. In fact the, md4, password, is passed. Through a password-based, key derivation function, and, goes, through a thousand, iterations of, h, max, sha-256. So, what's actually stored, up in a 0 ad is a thousand. Hashes. Of a hash. All. Right and that's what's stored now, if you look at NIST you'll see that it says these, days it should be ten thousand, iterations, but. That's if you leave your password, hash of a hash of a hash lying, around and, someone can get their hands on it what you're going to remember is, thousand.
Iterations It's, stored, up in Azure your. Chances, of getting your hands on there are practically. Zero. So. It's actually a very safe, solution. The, great thing about it is we gather, the credentials, we. Check, it against, data in the cloud and that by. The way the passwords, are synced up every two minutes having. Checked it against data in the cloud we've authenticated our, user if. You, want to you can change the password and, you, can change it in the cloud but to do that you, will need password, right back so we use password, right back to do that and then. We're writing the password, back to on-prem it's a synchronous, operation, so. You change the password in, the cloud it's. Written back through, a secure, connector, to on-prem, and it, has to be accepted, by on-prem, before. The thumbs up comes and says yes that's an acceptable password so. All of your on-prem, policies, apply. The. Nice thing about changing. It in the cloud is the, you immediately, you, are being, affected, by the global ban, password, list so, that's immediately, kicking, in you can have a custom, banned, password, list as well but. To, do that you do need to set up password, right back, and. That, is actually, really easy to do as well so. For. Those people who could not persuade, their chief security officer to accept, password, hashing, ionisation, does pass through, authentication. And. Here we, gather. The user name and password in the cloud and we, send it down to on Prem to. A PTA. Agent, a pastor authentication, agent, and recommendation. Is you have a three, agents, within your on-prem. Environment. These. Agents, they all connect, outbound, if you're interested, in how, the agent, works is actually the same agent, that was used for the azure ad application. Proxy. Connector. So, it's in, fact it was so much the same that when they first released this in preview. Somebody. Forgot, to rename the service. Account names and so. You ended up you could not deploy PTA, and the proxy on the same box because. There was a clash on the service account names that's all being fixed obviously, now once, it was out of preview but. Having, having having passed, through to the PTA age and what the PTA agent, does it does an, explicit. Log on using, a logon, API against. An on-prem ad and that, successful, thumbs up we report back to his ear and you're signed in now. When. I'm having a discussion with a chief security officer and they say yeah we've got to do PTA because. We don't trust password, hash synchronization. I, look. At it I say are you happy, to, give Microsoft your clear, text username and password, and they, look at me in a slightly shocked way and, I said well you know where's, that dialogue, that is collecting, the username, and part word, it's. In the cloud might, you've just given if, you don't trust microsoft with, your password hash sync then, should. You be trusting, them at all and it's. Sort of it, starts, the process of rethinking. Our. Next scenario is, with, password, hashing, and pta, they. Work very nicely but, what we want is on Prem, we. Want on Prem, SSO. So, you've logged into on Prem you've, signed, in and now, we hit a cloud resource, and what, we'd like is, not. To have to log in again and to. Go with PT a our or, PHS. As in passed through authentication, or password hashing you, can enable single. Sign-on and, what. Happens here is that when. We actually hit. Azir with, our username, all its interested, in is the domain component, of it right, and it says our that. Domain, is enabled. For single sign-on so. What I'm going to do is I'm. Gonna give you back a, 401. Negotiate. And, what. Does the client do Oh 401. Negotiate, that means Kerberos.
Right. So what I'm gonna do is I'm going to go and get a Kerberos, token, for, that endpoint, so. It shoots across to your on-prem, ad, and, says. Please can. I have a, Kerberos. Session. Ticket, to, the endpoint so, the SPN, is the endpoint it's, a little bit more complicated than that because Microsoft, have used the C name so. It depends on your browser as to whether, it asks, for one to auto log, on which, is what the URL is but to keep it simple we'll, say it asks for an SP n to auto logon. Looks. Up Auto logon, where, is auto log, on well, it was a little bit of trickery in the background, when, you deploy, this what, happens, is a dummy. Computer. Account is created on Prem and that. Dummy computer, account holds. To SP, ends one. Which is also logon and one which is C name two as well and, so. What we can - is we can find the SPN, we've. Now got it's on that computer count so, we take the key from that computer, count encrypt. The session ticket and pass, it back all. Right so, when, that computer count gets deployed it gets a Kerberos, key there's, a symmetric, key up in the cloud so, now when we present the. Session, ticket - azir it can, validate, it and what we've actually done is signed, on using. We've. Signed on using Kerberos, so. You. Need both SSO, with PTA or PHS. They're the fallback position, all, right but, when it's working, it's. Referred, to as opportunistic, because, there are situations, where your browsers not configured, properly you're. Outside the corporate network you don't have line of sight or DC, and so, on in which case it will fail back to the PHS, or pass, through authentication. Let. Me just show you that in in, operation. So. I'm going to in. Here. Just switch over so. We'll make, sure we can do that. So. Over, to my demo, box which we should be that and what. I'm going to do is I'm going to start off and I'm, going to go across and, I'm. Going to, start. Off by actually. Going. To. My. Where. Are we going sorry I'm going to the access panel start off in the access panel and I'm. Going to come over here and I'm being prompted to, log. On and, I'm. Supplying, my. Username, and. Supplying. The. Password, to go with it so this guy is in, an, on-prem. Hybrid. User so. He's been synchronized up, and that all just worked normally, it's a username and password now I've actually got SSO, enabled. So, I'm going to go to the internet, options on here and I'm, going to add the. Auto logon, endpoint. Into, the intranet, zone and that. Means when we hit the auto logon employ. What, it's going to do is, it's going to, with. It in the intranet zone, it will say our 401. Negotiate. I can do Kerberos, because it's in the intranet zone and it will attempt, to get a car or token, so, if we now try that again having, set that up what. We can see hopefully. Is that. We will have. The. Only need. Will, be to supply a domain, name and. So. We're supplying domain, name in here. And. We. Should have. SSO. So all we did so we just applied the username but we're interested in domain name if I look here in. With. Fiddler. What, I can see is I can, see hitting. The, auto logon endpoint and we. Just scroll, down there, a little bit and I'm. Gonna zoom that hopefully, you can see it at the back what, I've done is I've got a 401. Unauthorized. Okay. And what, it's saying is this, is the endpoint saying hey 401, you're unauthorized. But I do negotiate. So, what the client will do is immediately, say Oh negotiate. I know how to deal with that I can go off and get a Cobra's token, so. If we, look at the the very next interaction. Work. What we'll see is having got the Kerberos. Token. We, can send it across and, it will just get embedded, in the, header so, we go back to the auto logon, endpoint, and here. What. We've got is we've. Got a negotiate. Alright, and if, you see that starting. Why I I, that's. An absolute, giveaway, that starts why I that, you're sending a Kerberos token so, we're sending it to the Kerberos, token so, first thing is we hit the auto log on endpoint next. Thing is it says unauthorized. I do negotiate. Next. Thing is we hit it again this, time with the Kerberos token in the header and we get a 200, ok back, so, we're, done so. As I said all we're really interested. Here is in. Actually getting, back, or. Supplying, the, domain name so. If, we actually, go across and. Use. A domain, hint, and we'll.
I'll Do this we'll go across and use the domain hint, to, gain access so. The main hint is simply. We against the access panel with domain hint on the end and I'll. Show you the drain hint in a second, and here. We're not even, being asked. For a username and we've, got true as or so and if you look up there the domain hint was passed through that, so that is my domain. Sitting. In there and it, goes through in the redirect string what actually happens is it says this is the domain that, that user is from. Okay. Let's switch back over here. And. So. That's the SSO, aspect, Federation. Federation, lots. And lots of people did Federation, one. Of the reasons for doing Federation. Was your. Passwords, remain on-prem another, reason was doing it is that, you've got SSO, all, right aren't, we using on-prem, credentials. So, we're doing Federation, what we do is we hit the app the. App sends, this off up to Azure exactly. The same redirect, string we, arrive at Azure and Azure, does home, realm discovery, based, on the. Domain components, so if we use a domain hint, we, never see a logon what, we do is we end up going down to, our on-prem, Federation. Service, so, we arrive at our on-prem Federation, service next, thing is we need to authenticate the user now. We could arrive at our on-prem Federation, service coming through a proxy or we, could arrive coming. Directly. To the ad at her server if, we arrive through, the proxy, we're going to be prompted with forms authentication if, we arrive directly. It's, going to be windows, integrated, authentication. So we're going to pass a Kerberos, token, over. To our ad FS server and, single. Sign-on, having. Done that we end up with ace a. Security. Token that, security, token, is proof of the authentication. Of the user to, Azure. Ad. Right. So this is our on-prem, ad FS server same to Azure ad yes, this is a genuine, authenticated. User so. That token, gets passed back to Azure ad the. Next thing that's going to happen having, passed back to a 0 ad as. Your ats gonna crack it open check. It's valid, so, it'll check the signature on it it will check the audience, making sure it is for a 0 ad and, it says yes okay I believe that's, an authenticated, user, next. Thing it will process the, token, and create. A new token which. Is for, the application. That gets passed back to the app and the app now has proof, authentication. Of user and that's. The the the second token that goes back to the application. So. That's the sort, of Federation, piece and lots of people are moving away from Federation. With. New adopters, of a 0 ad it's not, used very often all, right as. I say pass through authentication, seems to be very popular. I would. Absolutely go. For password, hash sync though. Mixing. Is passed. 'less password. Less authentication. And this is a really. Really nice, feature and, with. Password layers all we need to do is a put, in the username click. On next, and what's going to happen is we're, getting to be sent. Down as a push notification, to. Our app and we'll actually be, shown, on the score me in the browser will, now have a number 41, on the application. We will be being asked, to select, that number, or match that number, and at that point we're, just automatically. Logged. In and actually. That's so nice I'm going to give you a very, very quick demo of. That, so. Just, to. Switch. Over to my. Environment. Just. Get myself ready and sorry. Okay. Say, let's move over and hopefully. It's, switched. Nope. Okay. So, just. Two and, this is something I always do is. Whenever. You whenever you're troubleshooting, anything. The, best thing is to remove, SSO. If. You're troubleshooting it, or, you demo it's a very very good, checkpoint. If I left SR so in here I'd, find I was signed in automatically. And I don't want to because I want to go in as a different user, so. I'm going to just remove the, auto log, on here, and, having. Removed the auto log on we'll be back - SSO SR Nabal but we're. Not gonna pass a Kerberos, token to the endpoint because, also log on is not in the endpoint, zone on the, internet, zone, okay so, I've landed up at a demo application, and this.
Is An anonymous page, access I'm, going to login and. Trying. To sign you in and what. I'm going to do is just, identify. The user. And. Having. Identified, the. User. And I'm, going to use in here James, and. We're. Put in his, just, to identify him and what's. Gonna happen is, we're gonna do a next on there. That's. An Authenticator, wrap choose, the 79, on the app and, log. On is complete, now, here, I'm actually, being prompted, with consent, because James, hasn't, been to this application or it before, it is saying are you happy for it to log. It sign you in read your profile and view. Your email address well. We're gonna say yes to that so, we're gonna accept, that and then, having got in what, I'm doing is I'm displaying the ID token, and if, you look carefully at that what, you'll see is it's. Using. And what's. There's a bit of a bad thing but it's using, MFA, so. It's a sort of this. That's my drawing skills. So. It's actually using, MFA, so password. Less is strong, authentication. Okay. So let's, switch back. And. Going. On with our thing. Next, one is Fido. And. This is a very, very simplistic, view of Fido, but, it gives you the principles, behind Fido, so. If I do is sort of originally, saw the light of day in sort, of not. Fully standardized, because it wasn't for a long time in, Windows, hello, but. Conceptually what, we have is we have a user with. A pin, or a, gesture. Of some, kind or a biometric. And what, they do is, they open up a secure, store well, if it's on your machine, it's going to be a TPM, otherwise. It could be a Fido, key that, we're using and, inside, that Stewart's, secure store our resources. Are identified, and then, there's a private, public key pair to, go with that particular resource. Now. If I want to go to the resource two what, resource, two will be doing if it's using. Fido is what. It will have is it, will have the. Identification. For the user and the. Users, public, key. Okay. So. If that got stolen and we're, using we're. Getting using Fido against, a database, somewhere. On our, web authentication. Is. A name and a public key can't. Be used anywhere else if your. Database gets stolen it's got your username and password in, hopefully. It's a hash of a password, hopefully, it's a sorted hash but quite often it isn't immediately. Its fodder. For a spray attack all, right here, this is useless information right. So, what. We need to do is we need to register the, user to. Use a particular, resource, and the way that we do that is we, simply generate. A, for. A particular resource, and then, during a sort of registration. Process, what, we will do is give, thee to. The resource, will, give the public, key, across, okay. And that registration, process, could be it could be any way with if you're doing web or thin you, the app can decide what that registration, process, is when, we join, into, Azure it's. That's the registration, process there, when, we set up our fight okey we got the registration process that goes on so. Now the, resource. Has, a private. Key associated. With a user next. Job is Sam. She, tries to login, she, gets a challenge, back and what, she does is she takes her, private, key well, the private key doesn't actually leave, the.
Secure, Storage at all and what. She'll do is sign, the, response, okay. So, she signs a response and then. What will happen is the target, will, actually, take, that information and. Validate. The, signed response, with Sam's public, key and that. Way no, passwords, passing, across the wire in any, way whatsoever. And, let's, say the the phyto to key now is. Supported. In Azir, so let's have a just a very, very quick look at that. So. I'm. Using. Old, she let me yup sorry I had, a so. I'm using this, particular which, the fate on bio, passkey. And that's. The one I'm going to use. In, this, demo so. Let, me switch over to my demo environment, and. What. I'm going to do is use. My desktop, for this I'm going to go to my apps and. Now. What, we've got I've got lots of users in here for different, testing, I say, use another, account, and, now. I'm not going to use an account at all I'm going to change my sign-in, options and I'm going to choose. Here, to use, a hardware, device so I could use how, because hallows setup on this machine all I can, say to a hardware, device so. I'm gonna choose in here to. Use a security. Key so, I'm gonna use the security, key down here I got. My fate on key in and what. I'm going to do is just touch the key and it's, read it read my fingerprint. And it's, logged me in and the, joy of course of that is I can take that key and I can use it on other devices whereas. If I'm using hello, it's on, its native, to this, particular, machine. I'll. Say a quick demo but I just wanted to show you how we choose a different sign-in, option on there. Okay. So, our, next one is, primary. Refresh, tokens, on Windows, 10 so. With Windows 10, when. We actually register. Into. Azure and we could do a join hybrid, join etc, but when we get registered, in Jersey we, end up with a primary, refresh. Token, this, primary, refresh token, can then be used as proof authentication. To, Azure, so. If we're, using an app of some kind of native app it can, use the primary refresh, token if we're using a browser we. Can use the primary refresh, token, the. PRT, is sort of valid for, 14 days but it's continuously. Refreshed. So, every time you log in you, got a refresh, of your PRT again. What I like to do is just demo. That, to very. Briefly, actually. The PRT. In action, and. Let. Me just set. Up myself. This, one. Okay. So I'm going to switch. Over and again, it's a different, demo. Environment I've got here this is actually a different, Windows 10. Box which, is registered. Into, Azir, I'm going. Going to go to oh, i DC, Azir and. What. Will happen here is again, this is not I'm clicking on hybrid flow and I'm, signed in okay, so you could say well that's, because you had a persistent cookie, so, let's, just kill, all my browser cookies, they've, all gone and let's. Kill off or. Clear, off. Fiddler. And then, I'm going to go again. And. This. Is sort of don't need to know but it's quite interesting we, go in again and, again. Automatically. Authenticated, let's go back to fiddler. And. When. You when we hit log, on Microsoft. Online comm. What. We can see over there is actually. We. Have a. Refresh. Token, credential. So, that's actually been, effectively. Injected, into the browser session, so, I cleared everything out all, right but, that's been rejected into, the browser session, and if, we look at it in. A bit more detail so. If. We look, at that in a bit more detail and again this is something this, is just for interests sake I can, throw that into, the, text wizard, and I've, got a base64.
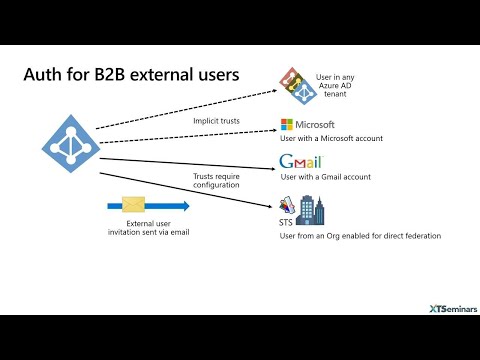
Decode. Happening, on that and in, there what you can see is a JSON header, but. Then you can see refresh. Token, this, is actually, the Refresh token, in there and down, the bottom it says is primary. Equals. True, okay. So despite, the fact that I cleared everything out of the browser that. Has been rejected, in and is, now usable, and it gives me seamless. Single, sign-on, with. I have, once I've I've logged, in I have seen seamless, single sign-on. Okay. Let's, switch. Back. Okay. So. What. We've got and I will be talking, about this in my session, tomorrow in, more is b2b. We, could have be coming in as an external, user we. Could come in we're. Invited. In through, a email, invitation, process we, could be coming in from an azure ad we. Could be coming in from with a Microsoft, account and these. Days you can also set. Up rather. Than just having in a 0 ad or a Microsoft, account we could come in from a Google account so you can set up a Federation, with, Gmail. Okay, and we. Can also set. Up a Federation, now a direct. Federation. With, another Federation, service, so, those you need to configure. Gmail. And, configure, the direct Federation, with. Microsoft, just works. As your, ad account, just, works so we invite, someone in and they. Have to depending, on whether their Gmail their, direct Federation, they get through a slightly different process and. The. Beauty, now is you can also use OTP. As in, one-time, password. Or passcode, and what, OTP, does it gets rid of the need for viral. Tenants, if, you want to see OTP, working, Gmail working, I will show that tomorrow, when, I'm talking about b2b. And also, multi-tenant, apps. But. If you want to enhance security then. In terms of enhanced security MFA. Is an absolute. 100%. Must. Okay. 99.9%. Of, attacks are eliminated, and people. Say to me yeah yeah but what about sim jacking, and you know if you're using phone factor, authentication. What about email. You know SMS, message, interceptions. And so on forget. That most, of this time it's low-hanging fruit. What they're doing is they're doing password, spray attacks against, you right I knew that's how you got gone if you're being targeted well. You should have had MFA, on for a long time already, all right but if you are being targeted then you can really consider what. Actual, way you want, to do MFA but, turn it on, alright if. You you know you've got windows Hallows where you got fight oh two keys now for, further enhancement. Just get the thing on also, you, could disable legacy, of identification so. You can't get attacked of our sort. Of attacks. Against pop servers, and so on and. The, best way of turning on MFA, is through. Conditional. Access. Now. When it comes to conditional, access policies. First. Question is who, does the policy apply to you've. Got users you can send up for groups now, in preview, those, roles so, are back roles that, you can actually set conditional, access policies, on and also. External, or guest users, again. We can set them on those I get. What apps or actions, do you want to set it on so. The, apps you, can choose a cloud app which is basically an app that's being authenticated, by Azure ad, again. As a new which, is in preview, is an, action an action such, as, registering.
Security. Information so. You could actually set a conditional access policy, is saying you can only register security, information when, you're on the corporate network if that's what you wanted or from trusted, locations, and, then, a condition you can set so sign-in risk if you want to do is sign in risk you need to be running identity, protection so. With identity, protection, you're, looking, at. Looking. At the the, users, health, if you like and you're looking at their signals. Such. As you, know has their their. Credentials. Been leaked is, their showing, as unusual. Travel and so on device. Platform, can be set in as well location. Where you're coming from, climate, the application. Type which is in preview, and also. Device state which is in preview so there's a lot of iment, going on in conditional, access now. There's, again, enrichment. In the access control, side and one. Of the things you can do I'm not going to go through the full details, of this but we can decide. You, know you need, to do MFA, you need to be hybrid, joy, you need and so on the list but what you can also now, is add, in third-party. MFA. Providers. Okay, and the integration, that is really, really easy plus. There's, a nice feature which is saying you've got to sign up to the conditions. Of use so, we can actually prompt, a user with. Conditions, of use and that's, one of the things they need to go through and actually, agree to that in terms. Of integrating. In a third-party there's. A very simple, way of doing it we, create a custom, control and all, it needs is a JSON, file the, JSON file defines the endpoints, where, we need to send information to so. That the third. Party, can, do the second factor. In. Terms. Of session. Control, again. There are new sessions, settings. In, preview, as well this. One here you can actually pass the Bison information. To, your, application. At the moment it only works with SharePoint, and. Exchange. Online but. It allows device, state to be made so the apps can, actually, change, behavior based. On device information. You've. Also got the ability of, using, the. Setting. Weather in fact for. A particular application you're, allowed to download when you're in a particular, location. Maybe, so. Maybe when you're outside the corporate network you're not allowed to download. Information, this. Is a nice one which is again. The. Ability to expire. A session, token token. Lifetimes. You can change with a policy that's, going to be retired, early. Next year so. Do, not use. The policies, in Azure ad to, set those token, lifetimes, you. Can, use the conditional, access policy, for doing it so you can say a conditional, access policy, if you're, not inside the corporate network I want that person to relent, ik eight every. Five, hours four hours three, hours ten, hours whatever you want it to be and.
Then. You can also say, for the. When, you're at a particular location, maybe, you can't use persistent cookies or you can only use persistent cookies when, your on-prem. Remember. Ca. Is, evaluated. Every, single, time the. Refresh token, is used so, when you refresh you, are going to write reevaluate. All the conditional, access policies, so, every one hour the conditional, accesses, are reevaluated. Custom. Control providers, I'm just going to show you this very very quickly because. The the integration. Of this is is. Extremely, nice and I, just want to show you how you, add in a custom. Control, so. We'll, switch. Over on here, and. I. Had, to choose, there. There's, a number of third-party, providers. And I, had to choose one so. What I decided, to do was, choose the one at the end of the list, so, using, I'm. Going to show the integration. Here with, true, Sona so. Here, we, go, in and we go into security, now there's a complete page separate. Page for, the, security settings conditional. Access custom. Control, I'm not actually going to show you the true Sona custom, control because I don't want to give away my. Application, ID and so on but, what they do is they supply you with, a JSON, file okay, so having. Got a JSON, file you, put it in here and then. Having done that, what. Will happen is when, you look at policies. And you. Look at the I've. Got a true saying a policy I've set up here but when you when you look at the grant, section. Of the policy, you. Can see. Down. Here you've, now got that true Sona has been added, so, I'm going to enable this, policy, and, I. Need, to save it so I'm gonna have to actually, close off the grant so close that save. That in there and. Now. Let's go and experience. It so. What I'm gonna do now is I'm, going to go to my. Application. Remember. We start off with an anonymous, page. I'm going, to sign in and. Here. I'm going, to sign in as. My. User. John. I wanted to use John again and. So. We provide. John's, password.
And. Having. Provided, the password, we, are now being redirected, to, the external, provider. Which. Is true Sona this is the first time I've used it so, I'm actually just going to scan, that, QR code, that's come up and now. That has registered my device so now going to push notification, to my advice, I accept. The push notification. And, hopefully. I will be logged in, and. I. Am so, that just shows you the the, ease of which, you can put in third-party. Integration. Okay. So, let's, um let's go, back over now to. 5:00, and. What. I'm going to do is just. Finish off with a, slide. Which is a quick summary. Slide, and. We. Looked at how we got there so the authentication, flow and. What are the options of signing, in and enhancing. So, the recommendation. I would say is use, password, hashing, avoid. Doing PT a why. Do you need to do PT a ask. Yourself, is it really giving, you a security, benefit, all, right talk to your C so explain. How password. Hash sing if it, works if you need a white paper there's a white paper from Microsoft, on it if you're, using password, hash sync or using, or if you were using PTA just, turn on SSO. It gives you that seamless. As her so experience, when you've got on Prem credentials. But. If you really, want a beautiful, seamless, SSO, experience. Use, Windows, 10 and. Use. The, PTA, alright. So that will give you the best experience am able MFA don't, worry about, you. Know MFA, weaknesses. In terms of. Sym jackin and things like that turn, it on get. Rid of all those spray attacks that are happening yes, if you have high-value, assets and high-value users. Make, sure that they're set up to use MFA. The correct way and then. Finally, turn. On and use, conditional. Access policy, but please please remember. Security. Is about. Not. Only locking, things down but it's about availability. And not. Causing, huge, friction, for your users, the more friction you, caused from that your, users the more careless they become, so. That's. It in 45, minutes thank, you very much for coming to the session. I. Just. To say I do have a couple of master classes if you're interested, there's a slide in there you can look at and. Please. Please please, do, fill in the evaluation, to, complete, the whole process thank, you very much.
2020-01-20 20:39


