An Introduction to Blockchain with Mark Russinovich
Noon. Everybody. Almost. There almost at the end good afternoon everybody try it again much. Better House bill Moines yeah. That's hard to see so looks. Like there's a few people in here it's nice to see the interest in blockchain, my, name is mark russinovich I'm, the CTO of Azure and this. Session is an, introduction to blockchain, and cryptocurrencies, and smart contracts, how. Many people are have. Invested, already in Bitcoin, or another cryptocurrency, just, out of curiosity yeah. How. Many people are here just because they want to get rich. For. Those of you watching that was everybody raise their hands so. What I've got is a. Session. Here. Where. I'm going to cover the. Background, of this whole Bitcoin, cryptocurrency, blockchain. Craze that's going on and take you inside some of the technical details that tech behind the technology behind just. The headlines that you're seeing I'll start. With an overview of Bitcoin mania for those of you that maybe haven't been paying attention and living. Under a rock for the last year. Or so I'll, give. You an overview of what's been going on with respect to Bitcoin, especially, in other cryptocurrencies, then. I'm going to talk about where, Bitcoin came from its origins, and, some. Of the theories are on how it emerged. I'll. Talk then about. Blockchain basics. And this is around they get into some cryptography. Just a very basic level some of you are too might be familiar with it but I'm going to cover the, fundamentals of some, of the cryptographic key. Cryptography, that's, really behind, what. Block chains are made of and. I'll take you inside then, what. A blockchain actually, consists, of underneath, the hood then. I'm going to explore, some, of the other blockchain, network's besides Bitcoin, and some of the other uses of those, networks specifically. The. Use of smart contracts, which are, transactions. On the blockchain that can actually be executed. I'll ton, talk about the limitations of, blockchain some of them with, respect to the current technology that are deployed and, dive. In a little bit into what we're doing to try to help enterprises over. Those limitations, with their current technologies, out there and then finally I'll just give you for, those of you that do want to get rich a little guide on how, to get started with blockchain. So. This. Is what you've probably been seeing. It's article, headline, from The New York Times everybody, else is getting, rich and you're not because you don't own Bitcoin, and, you've. Probably heard, your neighbors talk about it your kids talk about I mean I've got friends that their kids basically. Are saying that they're gonna retire because they're making all this money off cryptocurrency so they don't need to go to college and so. This. Is really causing this, big this, is a new word I've learned FOMO. This, is causing this FOMO, effect anybody, know what FOMO is yeah. So the Millennials in the house they're it's a fear of missing out that's. What this is causing and. You're. Seeing stories like this that it's contributing to it this is one from Seattle just a couple months ago where somebody actually went in bought a house at least that's the headline in Tukwila. Using. Bitcoin and actually this is an, example of the press kind of stretching the truth to get some attention this. Person, didn't actually buy their house with Bitcoin they put. The downpayment on their house with proceeds, they've, gotten, from the, sale of some Bitcoin that that had so but. So. Not quite, the. Way that and then you saw this kind of stuff this is just crazy stuff companies, that, would put. The word blockchain, into, their name and, then. Their shares would just go, up this is one example this is a company. That was working on, in. Bioinformatics. In, the UK they changed their name put blockchain, in it repeated. That's pivoted the Silicon Valley word for I'm failing so I'm gonna do something different. And, they're. Stocking up and then this one Long Island iced tea this is a popular, consumer, drink. Maker they. They're, doing decently in the tea business but then they said hey you know what we can change our name and.
Then. We'll do a lot better and so their shares went up 200%, when, they change their name to long, blockchain. And. So. They're putting, iced tea on a blockchain. So. The end but, if you take a look at what's happened, we're, in kind of a, small. Market, correction when it comes to crypto currencies like Bitcoin this, is since. May of last year, and you can see the price there. Five. Thousand dollars 10,000. 15,000. Dollars it went to just above twenty thousand dollars right, around the holiday period and then, you, see that it's had a correction and and as of today, it's somewhere of nine thousand, nine thousand one hundred dollars, Bitcoin. So, a little, bit of a correction but still if you invested, a while ago more. Than a year ago you're you're actually in pretty good shape with a Bitcoin, investment. And. This. Kind of pot burst bubble, you're starting to see these kinds of headlines but calling hype vanishes, just like that we're in the boring phase now actually, I don't, hear my friends, kids talking about Bitcoin so much anymore because I think they probably bought in right around the holidays when they were off from school and. Then. You see this people. That really are. Bearish. About the future, of Bitcoin. And other cryptocurrencies this. Is just from a few days ago Warren Buffett and I'd, never thought I'd heard hear, the words rat. Poison squared come out of Warren Buffett's mouth but. There it is his, view on Bitcoin and Bill, Gates said he would short Bitcoin he just said this yesterday he would shorten Bitcoin if he, could and turns. Out you actually can there's a futures market for, bitcoins so I sent. Him an email last night. Now. This is me I started, to play with Bitcoin, last year and aetherium, and I purchased a little bit and this is from my, account as of, yesterday. You. Can see that I but, just play and spent enough to play with it fifty dollars and that's, what it's worth yesterday, three thousand two hundred, so. That just to put that into context, that's almost enough for, a new iPhone. And. The. Thing is I'm killing myself like when, the prices started to go up oh my god why didn't I just put in a thousand, because that would have been a million dollars, at, this, point so I missed out but let's get to the history, of Bitcoin. Bitcoin. Was, created or launched, as a paper back in 2008, and this. You, see the titleist paper it's academic paper Bitcoin a peer-to-peer electronic, cash system actually has no references, no academic references so it's written, like an academic paper but. Not treated. Like it didn't treat it like academic. Paper referencing, other, sources. As foundation. For this work. But this. Paper if you're gonna read one thing. About Bitcoin to understand, the way it works you should read this paper because it's very clearly written it's. Very succinct, and, really. It's what, I'm going to be talking about for the next 40. Minutes or so most of the the bulk of the middle of a talk is just. What's in this paper. This. You can see that the author, Satoshi, Nakamoto. Nobody. Really knows who.
This Guy is in, fact, there's, nobody. Knows if it's a single person or an organization, some people speculate it's, the NSA, some people speculate it's some other, mysterious. Organization. Or somebody that's just a hermit and just said here's the technology for the world but you, can see whoever it is because. They. Gave, themselves a bunch of Bitcoin at the start, whoever. It is they're incredibly, rich right now the, market capitalization, of Bitcoin, is a, hundred, and fifty billion dollars as of today and so. Quite. A lot. Of money now there's tons, of speculation, about who, Satoshi. Nakamoto, is and somebody. From SpaceX. Published. A blog post at the end of last year, I figured. Out who it is it has, to be Elon Musk and they provided. All this evidence, that lines. Up to Elon Musk is the kind of person that would have done this and not taking credit for it and and that's, why he's so rich no that's not the reason he's so rich but Elon, Musk responded, to this I, don't. Have that response, here but Elon Musk responded, and said I am NOT satoshi, nakamoto in, fact he said in fact. I never, bought Bitcoin, somebody. Sent me Bitcoin once and I've lost it so. And, now. I'm really sad because imagine, how much richer I would be if I'd held on to it he didn't say that but. But. Nobody so nobody knows but let's talk about the difference between these crypto currencies like Bitcoin and, traditional. Currencies like the dollars or whatever a foreign, currency you might be carrying around with you the. That, kind of currency is called fiat currency it's one, that's issued, by. An. Organization, that backs it and they. Stand behind it, now. One. Of the challenges with fiat currency, especially. When it's transfer, you're transferring large amounts of money from one, entity to another one is that, there's long, delays between the, transaction, itself and the settlement of the transaction, this, period, in between where, the money's neither here nor there and. If, you do a wire transfer you're familiar with this it's 2 or 3 days for the wire transfer to clear from one bank making. Sure that everything is lined up and then the other Bank making, sure everything's lined up and then accepting, the payment and saying okay we've got it now. In. Addition most of the time even for things like wire transfers there's intermediate, the intermediaries, involved especially for large transactions. Or transactions. Across country borders there's organizations. Like, Swift, which sit there in the middle and, help. With. The validation, of the transaction, other organizations, that sit and will back, up the transaction. In the case where the whoever's. Paying, the transaction, fee defaults, on that transaction amount they. Cover, it so there's insurance there's, fees they're. The ones validating. It so you can kind, of trust the central authority, to say everything looks good before you accept. The transactions, amount. And start to use it and. That. Adds a bunch of fees to, the transaction, also introduces, additional delays, and. Because. The money's neither here and there there for some period of time and you have middlemen, and in the middle this offers, a lots, of opportunities, for fraud fraud. And loss. Like money actually can get lost and so. This, these are some of the big challenges with fiat currency, now cryptocurrency. Comes. Along and tries. To address these challenges, it's. A distributed. Decentralized. Currency so there's no central authority nobody's, issuing, this money.
Somebody, Creates the cryptocurrency. They, specify, how, the currency, gets generated I'll, talk about that later but once. The, cryptocurrencies. Often, running nobody's. In control of it it's, really, everybody's, contributing, contributing, as part of a network there's, no transaction. Settlement, clearing you. Send a payment. From one account on the cryptocurrency, network, to another one it's, immediately, once that transactions, accepted by the network it's, instantaneous. Settlement. And. There's no intermediate involved like, I said send, one same money from one current account to another one it's there as soon as the transaction, commits. Another. Very interesting property, of these cryptocurrencies. It's, got an immutable history. Of every single transaction going back to the beginning of timer or the genesis, of the cryptocurrency, and what this means is that it's possible, to go track, when. You get a some, currency, a Bitcoin, you can go back and track its lineage all the way back to the beginning of time all. The way back to where it was generated, or mind. Which I'll talk about so. This has made it very interesting or, merry very attractive, for, people that believe, in no fiat currencies and want to overcome all these limitations. Now. If, you'll read the Satoshi's paper, bitcoin. Is built on a technology called blockchain, against that the title introduction, block, chains and, block. Chains you'll, hear them also referred to as distributed, ledger technology or deal tease and if. You think about what a database is one. That's keeping track of assets, for example payments. Funds, from, one account moving, to another account there's a effectively. The. Digital version of the old Ledger's that kept track of who has what and with each account so, this is why you'll hear them called this tree Leger technologies, distributed. Again because everybody can see exact see, the Leger at the same time everybody has a consistent. View of what's going on in it. But. As I, hinted, before. Blockchains, get their. Capabilities. From cryptography. So. If you read satoshis paper you'll see lots of references to cryptography, and. What I'm going to do now, is just take you so it's from the basics, of cryptography, that is used in blockchain, so.
You Get an idea of what, mechanics, go on behind the scenes when, somebody talks about block chains and why, they're immutable and how they're decentralized. And how you can assure that, somebody, that is paying somebody else that. There's. Incontrovertible. That, that person, or that organization is, the entity that authorized, that payment there's. Three concepts, like, I said some of you might already be familiar with these but I'm. Gonna give. It a kind of a light touch as I go through hash, functions, public. Key cryptography and digital. Signatures which build on public key cryptography. So. Let's start with hashes. Hashes. Are algorithms, that create a, shortening, representation, or digest, of a, larger piece of data typically. It's a fixed length, digest. That represents, that data and the. Characteristic. Of a good hash algorithm, is that you, can take, a piece of data and. Modify. It slightly and it will generate a completely, different digest, and it's, extremely. Difficult or close, to impossible using, current, computing technologies, to. Generate, another. Piece of data that generates, the same digest, as a. Different, piece of data, in. Other words it's a very difficult to create intentionally. A collision, of hashes. One. Way to think about a hash is to. Think about summary. For a movie like Star Wars which, if. You'd summarized Star Wars here's what a summary one paragraph summary would look like and there's no other movie that would have exactly this same summary just, based on the, uniqueness of Star Wars and by, the way we're. All friends here so let's, just admit that the evil empire was you know the Empire was just trying to restore, order to the universe. And, and. By. The way the exhaust port will be patched on Tuesday. Alright. That's a old Microsoft, joke, but. So let's touch let's, take a look at how a little bit more about the technical. Details behind, what. A cryptographic, hash function, like a sha hash would look like sha-256. Hash you, take the word Fox you, hash it you get the digest you see a slightly different piece of text hashes, to something completely different and the. Digest, is the exact same length you change. Just small, you change you, v2u, you get something completely different you switch, the order of the letters you get something completely different and that's, the, characteristics, of a hash you can uniquely identify, any. Piece of data using, its hash. And. So. The next concept i'll talk about is cement is encryption and I'll start with symmetric, encryption which, everybody is familiar with this is just take a unencrypted. Message you. Pass it through an encryption algorithm which. Has a key, that. You apply to it that key being unique and then. Out pops, an encrypted message. This. By the way looks I've. Seen this kind, of thing before when I vote but accidentally opened a word document with notepad which.
I'm. Sure everybody how many people have done that before yep okay. Then. You can take that piece of data and using that same key. Decrypt. It and since, it's symmetric, cryptography same key can both decrypt, or encrypt. And decrypt and. Those, are very fast and that's the kind of algorithms that would be used for like BitLocker. For example to encrypt your hard disk contents there's one key it's used to encrypt the data and when you go read the data of the same keys used to decrypt the data now. Public key cryptography, is, is really. Interesting because it's. Asymmetric, and so. The same keys can't be used to encrypt as to, decrypt and, the. Way that this works if you think of it as a lock and that. Lock here, has three positions in the, middle one it's unlocked, like you're showing I'm showing here if you. Take the public key it can only turn the lock in one direction and when. You turn the lock in that direction, it. Moves to a and it, gets that, lock becomes locked, that. Public, key cannot be used to turn it in the other direction so it can't be used to take it from a back, to be the, only key that can be used for that is the, private key the, private key can turn it in the other direction so the private key can be used to move from A to B or from. B to C but. It can't go back. From C to B or B to a and hence. The. Asymmetric, nature of it now it's called public private key cryptography, because these. Are generated as pairs together. Using. Prime. Factors, and. They're. Paired together such. That no other. Combination. Of numbers can. Lock. Or unlock the. Locks the same way that the public and private key can of. Course the public key is something. That the, part. Of the, the. Key, that you would give out to anybody you could give it out to literally anybody in the private key you would keep to yourself and keep it secret you would hide it away so nobody else could have a copy of it once. You've got this scheme. In place we've taken one. Part of the key and, you said that's private the other one is public you can do some really cool things with that one. Of the things you can do is encrypt data and, you, can encrypt data so. That only somebody, else that, it's intended to can, receive it in a way that you do that is you take a, piece of data you take the person's. Public, key that, you want to send this data to and you, encrypt it so, just like symmetric, encryption this. Keys used to encrypt the data but. Once it's encrypted to that person's private, key. Nobody. Else with. The public key can look at it even you cannot decrypt it using that person's, public key that they shared with you the, only person that can decrypt it is the, person that owns the private key so they can take their private key and they. Can move. The lock to the unlocked position, on their side, decrypting. That data so. It's a great way to if you want to send a secret that nobody else can look at just besides, the intended recipient, that's. What you would do is encrypt it with their private their. Public key. And. If you take a look at what this looks like cryptograph, graphically. An encrypted message encryption, algorithm with receivers, public key you get the encrypted message you hand that to the receiver now, they can take their private key, and decrypt, it and now they can read the message. Now. Digital signing, is, something. Else you can do with public key cryptography and this is heavily, used in block, chains, if. You want to prove that you're the person, that did something you can do that using.
Your Private key and then other people can verify it using your public key that you're the one that did something and the way this works is just, taking the lock in the opposite direction you take, the piece of data you. Encrypt. It with the private key and. Then. You. Hand it to somebody else and they, can decrypt it using your public key. Only. People with the public key can, decrypt it and. They. You know that, if it's decrypted, with somebody's public key that they. Must have encrypted it with their private key there's no other way anybody, else could, have produced that, encrypted, data because. You're. Using that person's public key that's the only, key that will unlock that. Data and so, that is called, signing, the way that you, do signing actually is to take a. Message. You. Take this message here and you want to give, it to somebody else and prove that you, authorized. This message you said this message is the, message that I want to give you the. Way that you would do that is hash, that message so you get the digest and then you, encrypt that digest. Using, your private key so. What. You other person gets is the, unencrypted, version of the message the, encrypted digest, of that, message and now, they want to verify that you're, the one that that, message they received an unencrypted, form is what. You actually intended, to give them so. The way they do that is, they. Take your public key they decrypt the message they, get back the hash, and then, they compare, the hash that. Was unencrypted, with. The hash, of the plain text document that you shared with them and if those match that. Means that. They, actually digitally. Signed that. Hash that document, effectively. Nobody. Else could. Forge that signature, because. Nobody, else has that person's private key that matches the public, that. You used to unlock it and so. You. Just compare the two if it's equal you know that that's a verified. Message. Or authenticated. Message a signed message, and. Those are the the basic tools. Public. Key cryptography that are used in block. Chains and now we've got the fundamental, building blocks we can start to talk about how we put these together to. Implement, something like a crypto currency like Bitcoin. The. Fundamental. Operation. Performed, in a cryptocurrency or any blockchain is called, a transaction, it's. Executing. Something changing, some state in the, case of cryptocurrency that, state is transferring. Assets from, one account to another account and. The. In this case we have Bob that, wants to create a transaction, and a cryptocurrency that's saying pay Alice 10. Of my Bitcoin so. The way that they do this is they take the, idea of a previous transaction, that. Shows that they received. Ten Bitcoin, so. Their account in, that previous transaction, was assigned or transferred, ten, Bitcoin now, somebody can go back at that previous transaction, verify.
That, Bob, really owns ten Bitcoin and the ten Bitcoin that Bob is trying to pay to Alice and then. Bob would then. To. Give it to Alice and nobody else, would. Take and, encrypt. A, transaction. That. Includes Alice's. Public key and then. Sign, it with, his own private. Key. Now. That this transaction, is signed it says that Bob, authorizes. That. Transfer. Of ten Bitcoin from Bob's account to Alice. You. Can prove or, verify, that Bob actually authorized. This by going and checking. The diddle sick digital signature with Bob's public. Key and if, the hash of the unencrypted, transaction, matches the encrypted. Hash there that, was encrypted with Bob's private key you know that this transaction is the one that Bob actually intended, and, put. The stamp of approval on give Alice, these ten Bitcoin and so. That's the that's the fundamental way that a transaction, is authorized. And why, when you're talking about trip, public. Cryptocurrencies. That. Keeping. That private, key secure, is so important, if you lose that private, key then somebody else can masquerade, as you they can go on authorizing. Transactions, that. Appear to be you because, that private key represents, something, only you should be able to do. So. Once, you've got this basic transaction. You start to build up transaction. Chains and I've kind of hinted at one before because I was talking about how Bob is referencing, some previous transaction, that shows that Bob owns ten Bitcoin, so. You see in a transfer straight forward transfer of asset from one owner to another owner in this way you, can see there's one transaction, here owner one, owner zero signed. This transaction, that says give, owner one. Some. Amount, of currency and owner one that can unlock that transaction. And. Execute. Another transaction, that, says give, this, to. Owner, two. And the way that being unlock, it of course is by digitally, signing this transaction, that they just created saying give this asset now to owner - and then the chain. Continues. Like that owner, - then can take and create another transaction digitally. Sign it and then somebody, else owner three can verify and other, people on the network can verify that owner to really transfer, this asset to owner three so. This, is. You. Start to see this this. Immutable, kind, of characteristic. Of blockchain, show up here with, these transactions, that reference one another so. That and have this immutable. Record, of who authorized, the transaction in. This case owner zero, giving something known or one giving some that giving, something donor two so. These are the transaction, chains that flow, through a blockchain, now I haven't gotten to what a blockchain is we're going to come back and look at that in a second when I show you how, you can explore. Transactions. Using. There's. A bunch of different tools to go explore, transactions, on public. Public. Blockchains. Notes. And. I've got this, site, here it's blockchain. Info. Block info dot info, it's a great site for just exploring the bit. Blockchain. And. You. Can see at the top of it we see something called blocks, I'm. Gonna talk about that later but if you scroll down you can see some interesting stats so there's bitcoins, value right now 2200. You. Can see the number of transactions, a day so, this is number of transactions, that, have been executed on a Bitcoin network in the last 24 hours, you can see here the market cap 157. Billion and, then. What. We're gonna do is just click. On this block I'll explain what that is in a bit but. Blocks contain, transactions, and so we can go take a look at, one of these transactions, and, what. We see in the transaction. Here. Are inputs, and outputs, these, inputs are the, addresses, of. Accounts. In Bitcoin. And. They're. Really crafted, from the, public, keys of those. Accounts, those private public key pairs for. That account so when you go create a Bitcoin. Address you're. Basically, and then advertising. It to somebody your. That's basically derived off the public key that matches. The private key that you keep yourself, to, be able to execute. Transactions, like this in, this case the. Transaction, has one input and it's, got two outputs, and so what that is saying is that it's. Taking some input. From a previous. Transaction, and. Splitting. It among, to output, accounts and it's splitting it this way, so. You can see the total input, total, output.
Matches. In this case and it doesn't always match I'll talk about that later and. It. Actually doesn't match this is the difference right here so I'll talk about that later and, that. Is the. Fundamentals, of looking. At a transaction, underneath the hood what. You would see are references. To previous transaction. Hashes. Signed. Here, by that account the private key of that account the person that owns that account on the left side that input account you. Can have multiple inputs in multiple outputs so I just happen to pick one that just had one, input. In multiple outputs but you can have multiple inputs as well so you can take currency. From multiple, accounts basically. Combine it together and then spread it out among multiple outputs, one. Little, piece of trivia about, Bitcoin, transaction, is the input amounts. Have. To match the output amounts, if there's, a difference, that, money goes to somebody called a miner and I'll talk about that a little bit later you can see the difference there the fee that goes to the miner but, there's, no way to return. Unspent. Money to. Yourself if you want to actually. Return you know gives if you got 10 Bitcoin in your account, and you want to give somebody 7 and you want the change, back basically. One of the outputs has to be back to yourself of the, 3 Bitcoin difference. So. That's what a transaction. Looks like now, we're, ready to move on to the, the. Next building block in a blockchain, and where it gets a sexual name from and that, is the, blocks themselves and the, way to explain, how blocks. Where. Blocks come from you, got to talk about how the, network agrees. About. Transactions. So. The. Challenge, here with these networks, in with transactions. In this, decentralized ledger, is that, everybody. The network is asynchronous everybody's. If, they're sharing transactions, with one another we're all trying to keep track of what's going on we. Can receive transactions. In different orders and. You. Can imagine cases. That. Are inadvertent, or deliberate, where Bob would say I'm paying Alice 10 Bitcoin and they, sign that transaction, and send it out to the the, network and, everybody gets this Bob's giving Alice 10 Bitcoin, and then. You can imagine that. They. Also send out something else saying I'm giving using, the same coin I'm giving, 10 Bitcoin to Joe and now. There's transaction, flowing around that. Has Bob giving 10 transactions, to Joe the, order matters. Because. One of those is going to fail if, you put, the transaction, Alice first then, the transaction, - Joe fails because there's no ten Bitcoin, and Bob's account if. You put them in the other order, that. The reverse thing happens and so. The network has to agree about what, the order is because. Everybody, needs to know and. Agree. About how much money Bob has how much money Alice has and how much money, Joe has and to. Achieve some, common understanding that's, a process called consensus. And the challenge with consensus, in these. Networks is that nobody trusts anybody you. Might call this Thanksgiving, at your play in your house. But. This is, nobody. Trusts anybody in fact there's people that are actually actively, trying. To gain the system and double, spend their coins this is the double spending problem that, these networks need to overcome and so. The. Solution, to this. Double spending problem is to. Accept proposals for. In transactions. From. The. Network from. Entities. On the network that combine a bunch of transactions, together and say here is my proposal, for the next batch of transactions, that we're all going to add. To, the ledger and process. Now. The challenge. To this is how do you determine. Whose, proposal, to take and how, do you stop, the system from getting spammed with, a bunch of just, bogus, proposals. For transactions, to. Be added to the ledger the solution. For that in the case of Bitcoin, is something. Called mining. In. And, this is. Mining. Gets. Its name from the way that Bitcoin, is actually generated, and. I'll come to that in a second, the. Entities. That try to collect, transactions.
Up And then submit to them the network and say hey everybody here's, a bunch of transactions, let's, add these to the network and here's the order that they're in, that's. The mining process and if you take a look at the mining process they create these blocks with, those transactions, in them and, they. Link it on to the ledger in. A specific place, by. Having. That block, include. The hash of the. Previous block and, then. What. That does is, creates, this immutable, connection, between one, block in the previous block, because. That. Block that was added has. The hash of the previous block. And. So. You can see the the network, here blocked four five six one block four five six to, referencing. Hashes, of basically. Everything. That goes back to the big of time. Because. The hash of one block includes the hash of the previous block which has the hash of the previous block which has the Ashley the previous block in fact you can think of it as the hash of the most current block has. Some information about the very big first block in the whole network you, change anything, in the middle and everybody, can tell something screwed up because they can't follow that chain back if, I modify block four five six one that, hash that's sitting there in block four five six - is not going to match that block. That, unencrypted, version of that block. So. That's where. It gets we get the name blockchain, and also. How we get this immutability, this, immutability that. Shows. The evidence that's that. The entities, that owned Tran assets, are actually executing, those asks those transfers, of assets as well as the immutability of everything, that has come before in. The, blockchain, so. That's what miners are doing is pulling, up these transactions, and submitting them now. It's. Called mining, because. They've basically got a dig for, the. Wind the award the award that comes from actually producing this and having it accepted, by the network there's lots of entities. Are out there collecting transactions. That are being submitted. To. This peer-to-peer network, they're putting them together they're, putting in the blocks and then they're sending them out and everybody, else is trying to get a view of what the ledger looks like so they get blocks from lots of different entities and. So. Like, I said one, of the goals is to stop try. To prevent spanning, spamming, of the network with bogus. Transaction. Blocks so. The way that. The. Legitimacy. Or the. Genuine, desire to participate, in the network is established, in the case of Bitcoin and many. Other cryptocurrencies is, something, called proof of work in, proof. Of work a. Miner. Has to show that they've invested something, to. Produce this block that they're submitting to the network that. They've spent some something, that, it's cost, them something that they're invested, in that thing being, legitimately. Accepted, by the rest of the network because, otherwise they're just wasting their money and so. The way they do that is by solving. A cryptographic puzzle. Talked about hashes, before and how there's no. Way to, or. Using. Current computing technologies, to. Generate. Collision. Meaning, I'm gonna generate this there's, a target hash I want to generate so I'm going to produce some document, that hashes to that so, that's. Why hashes are called one-way functions I can't go from the hash back to a document, I can only go from the document, to the hash. So. The. Way that they, prove that they've invested energy, is they've. Got to produce a block that has, a hash that. Meets. A certain requirement. A hashing difficulty. So. For example we got to find a hash, we've. Got to generate a block that it's hash. With. All, of it in in it is. Below. A certain value. Now. Think about that because. The hash values, there's 256.
Bytes In a hash that's massive, amount of space how, do i generate a, hash, below a certain value I, can't. Do it deterministically, I don't know what data, to put in the block, to. Do that but. The miners are given one little piece of data in, the, block format. Called a nonce that. They can mess with to, try to get the hash to come out to a specific. Target, value or range of values and so. In the case of Bitcoin, what. Happens is the. Miners are, given. This puzzle and they'll, have to find a way. To generate a block with those transactions, in it that they want to submit where. The hash is has, a certain number of leading zeros, so. You can take a look at right here the. Only way to do that is through brute force just to explore take, that nonce and. Mess. With it and so you can see the nonce here goes from zero one two you, can see four two four eight four two four nine boom four, to five oh we generate enough leading zeros for, leading zeros at that, point we, submit our block, to the network and we say look we, did the work to go. Find this. Nonce that makes the hash of this block have, a certain number of leading zeros and, now the rest of the network can, easily verify yep, the hash of that block has, nomura leading zeros the only way you could have figured that out because it's a one-way function is to, actually go brute-force it and. So. That's what miners do is they brute force they just search the space randomly, trying, different values for the nonce. Now. Before I come back to that, there's. Something else that can happen once you because you can have some different miners that are, producing legitimate. Blocks they all are, solving. That puzzle in about the same time, plus. Or minus probabilistically. And so the network because, it's asynchronous, different. People on the network can get different, blocks that, are legitimate, that. Have that proof-of-work puzzle solved, and. That's what's. Called a fork. So. In this case we have a fork here after. Block two four two three four four one three there. Were two legitimate blocks, mined by. Different miners that. Both have, the hashes of block, two three four four one three in them so. The. Network at that point if you're sitting, on the network and you're keeping track of what's going on with it you get one block you add it on do you get the other block you look at it oh this is legitimate, too you're. Not sure at that point which. Block the majority, of the network is going to accept, so. What you do is you just keep them both and then. Wait for the next block to show up and, the next block that shows up in this picture is block 2 3 4 4 1 5 that. Points at 2 3 4 4 1 4 and so what, you would do is say oh this. Is the block that, I think is the one that's going to win so. What I'm gonna do if you're, a miner is mine, on top of that and try to create the next block that is on that part of the fork. The. Winner, here. Is. The. Longest, chain and the, network basically converges. On the longest chain over some period of time because. Of the probabilistic, nature and, that long delays, in, time. It takes to generate a block it's. Likely that one block one fork is gonna start to grow, longer than another, for while, long enough amount of time that everybody even, though the network is asynchronous, agrees.
On That view. So. This is called the deeper chain chains are considered, deep so, the deeper a transaction. Is in the chain the more solid, it is the, more likely it's not going to be undone. The. Risk, of acting. On a transaction. If it's, not deep enough is that. The block that that transaction, in is in, gets. Invalidated, because that Fork of the, blockchain loses, in the network agrees on a different, branch. And. What. Exactly is that risk well. If I for, example accept, a payment for. A cup. Of coffee because I'm a store, owner and. I. Accept. That transaction. And the. Network then. Chooses. A different, fork than, the one that that block was in I never. The network doesn't recognize me having gotten that money and that, person that paid me that money, might. Have be paid it to somebody else now it's unlikely and that person's gonna be malicious and try to double spend but. That's what the risk that could happen. It's. The stakes are very high in cases where somebody is problem, might actually, try, to legitimately. Screw, you so, if I'm selling, a van Gogh for example, that's. A expensive. Painting, and if, I sell it for cryptocurrency. And. I'm. Selling, it to somebody I don't know, that. Person might really try, to double spend it's in their interest, to double spend the money that they're giving me and so, what they might do is give, me a transaction. You know give the network a transaction, that gives. Me the money and then immediately create. Another transaction that. Get transfers the money into a different account the. Same money. And hope. That the. Branch that they, gave me loses, and they, might their, use techniques, like going and messing with the network to try to get this to happen and. If. I give, this person that van Gogh and then. That branch. That has the payment, to me, loses. I'm, just out the money and the van Gogh so. This is why the. Recommendation, when, you pay some when you accept a payment for some good or. Looking. At a transaction, that you don't consider it really, solid, until it's got some depth in the blockchain and the, rule of thumb for. Any decent-sized, transaction. Is, six. Blocks which, in the blockchain network is about 60. Minutes because in the blockchain network the. Goal for solving that cryptographic puzzle, is, ten minutes and. What. Do I mean by how do they set this goal of ten minutes it's. Kind of interesting because the. Blockchain network, the code that executes sits watching how long it takes for blocks to show up that illegitimate blocks that have solved that cryptographic puzzle, and, if, blocks, show up for. A while. Significantly. Let faster. Than ten minutes it. Raises the difficulty, of that cryptographic puzzle, says oh looks, like the networks getting stronger it's, able to brute-force more, quickly. There's. More miners. Out there brute-forcing. Hashes, so I'm gonna add one more zero to the puzzle and make it harder that's why it's called difficulty, and, if the network.
Starts To slow down these blocks show up more. Infrequently, than 10 minutes significantly. For a while then. That means that there's, less mining. Activity going on fewer, people are brute-forcing. And so we're gonna lower the difficulty of the puzzle to try to get it back to ten minutes so that's why you. Hear about Bitcoin transactions. Roughly. Or blocks roughly be generated every 10 minutes or so so you, really want to wait about 60. Minutes and there the, chance of another fort coming along in the, network that, obviates. That, deep fork that deep chain that you've already got, your transaction, in is highly. Unlikely there's, so much work. Generated. Right now by mining that, it's almost impossible for that scenario, to legitimately, show up whether you've got a some, miners off in the corner that are mining off a different chain. To, try to double spend and then. Obviate, that, transaction. That you've got somewhere in the chain. So. Why do these miners do all this work why. Do they want to prove that they've got, a stake by doing this proof of work well. They're rewarded, for it, there's. A transaction. At the, beginning. Of a block called. The coinbase transaction that they create. That. The, network agrees whoever mines a block that's accepted, by the network gets, a certain amount of coin bit, coin. This. Started at 50, Bitcoin in the Bitcoin network when it long, and it has roughly, every 210th, where its haves every 210 thousand blocks so every, 210 thousand blocks the code, that executes the, Bitcoin network. Says. Oh, time, to only accept coin. Based transactions, that. Are half of what they were before and we're currently at to point at twelve point five bitcoins, so this is having, roughly, every three to four years you can see the Bitcoin money supply is going to run, out sometime, in the 2030s at. This rate at, the rate that blocks, are being generated and. That's. Intentional once the. Rewards. Through coin base are gone the, way that the miners are incented, is through fees and you. Saw the fees that, were there paid by that transaction. And ever executed that transaction said I'm transferring. Money to this other account I'm leaving. Some unspent, any unspent, money. In. A transaction, that a miner mines. Goes, to the miner so. That's, effectively the way to give a fee is to not spend. Everything. That came on the input to, the output and. Right. Now the fees you can saw it was a relatively small fee that was paid on top of that transaction but as, this. Coin, base becomes more and more scarce the. Fees are going to continue to go up and. That's the way that you're going to incent when, you submit a transaction, to the network miners. To, take your transaction, and add it to the blockchain in, fact already today, the. Basic rule, of thumb that, miners follow this. Course is to be. Incentivized. To put those transactions, with higher fees into. The blocks they mind because. That more money for them. And. So. How, they're doing, this mining there by. The way this is a picture of my basement. No, actually this is not a picture of my basement my wires would never be, a rat's nest like that but. Here's. A picture of my basement. So. What you're looking at here are mining. Pools, so. It's very difficult for unis now sit, on one computer with the GPU, even and successfully. Mined blocks because. There's so many other, miners. Out there that. Are trying to generate, blocks. And doing proof of work and doing proof of work at massive, scale, like. This in these forms of computers. Just, do nothing but.
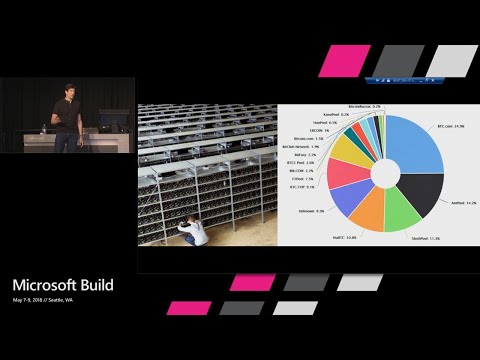
Search For hashes, search. For nonces that matched the. Difficulty, of the Bitcoin hash puzzle. These. Mining, pools the way they work and you can actually buy into them yourself you, go contribute, to the money to the mining pool and the, mining pool is represented, by basically. In an investment from everybody, that's contributed, money if you, contribute 10%. Of the money that goes into the mining pool they're going to buy more mining gear and if, the mining pool wins a block. They. Distribute, the. Coin. Base in the unspent fees to. The, members. Of the mining pool according. To the percentage of their investments, so, if I contributed, 10%, to money pool and my mining pool won a block I get 10%, of whatever, fees, and coinbase came out of that block and that's. An incentive for people to all, get together and have a higher probability of winning blocks, you. Know you're gonna get less money out of the block but you get a higher chance, of getting something, than if you're just a loner going after it you can literally you could win as yourself. But it's like winning the lottery at this point. Now. As far as who's doing mining. There's. No basically, there's very few individual, miners out there it's almost all mining, pools. 99.99%. A, Bitcoin. Is done, by mining pools and you can see here. They. Can advertise who, they are when. They go and win a block. The. Reason it the reason they advertise who they are of course is because they want you. To go oh this is a winning mining pool I'm gonna go put money into that because then I'll have a chance of getting some return on the money that I put in the mining pool the. Interesting thing about these. Mining, pool, is where. They're located. You. Can see that China mining, pools. Control. More than 50%. Bitcoins. Mining, and. That's. A potential, concern to people you've, probably heard of the civil attack or 51%, attacks on cryptocurrencies. With. That much mining, power if they all got together and said. We're gonna do double spending, they could do it most. Likely they could force the, network to create have big deep chains that fork and the. Doom. Have. The the people accept transactions, on a long fork keeping, a longer. One to themselves until they say okay now I we've gotten all the van gogh's in the world let's, go unleash the other, the. Other fork that we've created that's longer and now. Everybody's, out of their being goes and they still have all the money all the cryptocurrency. Now that the disincentive, to do this of course is that. If the somebody did that the. Value of their currency would, go to zero but, in. The case of minor. That is saying you know what I'm gonna just do one last thing before I'm out of here and. Basically I caused this whole thing to crack come crashing down but I'm walking away with a lot of ENGOs that's. The potential risk. By. The way here's the other one slash bullets in Czech Republic. Now. Then also the interesting thing about China is that the Chinese government the financial regulators there have banned crypto currency. And. This is from about two months ago, game. Over China wants an orderly exit basically, they said we're banning cryptocurrency in fact we're also banning, mining you can't do mining anymore now. I've, tried to look and see what's going on with this but. It's. Still that's, that mining chart is from yesterday, so the, miners are obviously still hard at work mining, and, so. I it's not unclear at this point what's gonna happen to those Chinese miners what I really think is gonna happen to those Chinese miners is it just go offshore with.
Their Mining operations, but. It's. Gonna be interesting to watch this play out given all, that's my name power in China with the Chinese government saying, they, don't like cryptocurrency your money now, speaking of all that mining power we've. Got a potential problem here it's you know what's, considered, an environmental catastrophe if, you. Consider. The amount of compute. Power that's thrown at mining Bitcoin at this point in time, each. An individual, transaction, right, so only one miner wins and the amount of energy they spend on just mining, that winning block is relatively small but, all of the energy everybody's spending trying to get that winning block all, adds, up such. That an individual, transaction, when you clear. It on the Bitcoin network when, you submit a transaction, to give somebody else in some of your Bitcoin is about. 270, kilowatts, of power has been burned, for. Getting, that transaction, onto the blockchain the. Total amount of energy now consumed, by the Bitcoin network is. About. The amount of energy of the country of Denmark consumes. So. This is why there's, a lot of people that are concerned about how much energy is being spent just solving this cryptographic puzzle, for these cryptocurrencies. Now. Let's go take a look quick look at blocks, before. We move on. So. We were here in this transaction and you can see that there's a it's included in this block right here in. This. Block, has. A bunch of information that's embedded inside, of it like the the number of transactions, are in it you can see the total output of all those transactions, is this, amount of Bitcoin which is. The. Estimated transaction, volume is 317, Bitcoin. So. That's the amount per transaction, roughly, that people have spent in transactions, on this you. Can see. The. Difficulty, so that's effectively the number of leading zeros that, the miners gave to hash and. If, you scroll down you can see all the individual transactions, what we're seeing before so you can see most of them are here's, two inputs to one output, here's, one input to many outputs so. Somebody's splitting, up a bunch of coin and setting off in different directions so that's a quick, look at blocks, and of course you can take this and you can say well here's the hash of this block here's. The hash of the previous block and we can follow this chain all, the way back to, the beginning of time. Or. The Genesis block that, Satoshi, Nakamoto, made. So. That's a quick look at at the blockchain for, Bitcoin if you put this all together the, Bitcoin network so, there's, different kinds of nodes on the network the. Ones that are keeping track of the full state of Bitcoin they're called full Bitcoin nodes there's about 10,000, of those and that's really what. Determines what's. On the ledger what's in Bitcoin is all these nodes agreeing, this. Is the way the. Bitcoins all divided. According to these rules that we all agree on that, the. Most work wins. And. Anyone, who can spend transactions. You can go, buy it you typically buy it from somebody that owns Bitcoin, give, them fiat currency, in exchange for it you, get now your, own account that. You've created you say tell, them to send it to and once. It's there you can then go and send, Bitcoin to other people on the network. There's. A bunch of other cryptocurrencies that, have evolved over time that are very popular and also have decent mark market, caps like coins one ripple. X RPS another one how many people have heard of ripple, I'll. Come back and talk about that one right now the ripple, is one. That's got the cryptocurrency. Purist. A little upset because. The. Way that I described Bitcoin, there's no central authority the, money is created. Through mining, so, nobody controls who gets it nobody, controls the amount except, for the algorithms themselves in the, case of ripple there's. A or, X R P there's a company called ripple, that, actually issues this. Currency. And the way that they've generated. Is they've given a bunch to themselves and so. You can see. This is not a decentralized. Cryptocurrency. It, is, a cryptocurrency but, it's not decentralized, it's, based on blockchain. Everybody's, got a common view of what's going on but, given, the cryptographic, keys, to the network only the. Ripple founders can go generate, more XRP so. It's not mined. In the traditional sense or at least the. Mining doesn't account for all of the that well, the XRP that they can inject into the network and so this, puts. Them among the richest people in the world now ripple prices have come down since this article came out at the time this article came out they, were worth get, this sixty, billion dollars, so.
That's Kind. Of money that's going into cryptocurrency and then. Here's another one etherium there's. Another public cryptocurrency, Network this. One has. A decent. Market cap as well it's, up in the tens of billions of dollars but. This network. Isn't, designed to, be a cryptocurrency. Network it's designed to be. A network, for. What are called smart contracts. So. Let's talk a little bit about smart contracts. This. Is extending, the blockchain not, just to have simple, transactions. Of asset. Transfer from one account to another one but actually to store programs, and. Those. Programs can be used to encode business, problems. They. Basically. You. Can encode, contracts. As code. Itself, on the. Network. So. These they're, called smart contracts because they basically execute, on their own nobody's in control of executing, them you can send events to them you can send you can call functions in them the network executes them in the case of aetherium is a theory, in virtual machine the, language to write these small contracts, is called solidity I'm going to show you example of that in a minute and you. Can basically. It's turing-complete so, you can write very. Complicated. Contracts. Inside, of solidity. And run. Them in the public blockchain, on aetherium. And, again. Every state transition, is logged, into the. Blockchain the etherion blockchain so it's immutable so you. Can go back and, follow. The execution. Of a smart contract back to the beginning. If. You take a look at what a smart contract looks like I'm going to show you this in a second but, it's got some characteristics. Here you. Can hold. Or transfer on chain assets meaning you can even have smart contract can own ether the currents cryptocurrency, of aetherium they, can send ether to other accounts, they can receive ether but, they can also generate. Their own forms, of currency on top and that's something that people, have been doing that I'll talk about in a minute the. There's, some big challenges to. Writing. One of these smart contracts because once you put it on the ledger it's. There and you can't change it and if, you have a bug in it. You're. In trouble there's. Been a high-profile. Case of. The. Dow a distributed. Science organization, back. In the middle of last year they, had a bug in their smart contract, that. Allowed some somebody, to go and call it recursively and, empty. It of the, ether that was assigned to that smart contract and give, it to themselves and. They. Gave, themselves tens, of millions of dollars before. This thing was shut, down and. What. That caused is the, great aetherium, Fork of August, of 2017, where. The, etherium. Founders. And. Committers. Who. Are faced with this conundrum the, dow had lost huge. Amounts of money through. This bug in their smart contract so the question was oh well, they screwed up let's. Just continue because, this is a decentralized, currency we, shouldn't be the police for. This if, people screw up they screw up and then, there was the other faction, that said no no no if. This can happen like this for huge amounts of money like that then, that's gonna undermine people's trust in this network and we. Actually but they're not unwilling. To invest in it because their risk of losing, something like that to bug like that is too high so you, know what let's go fix this and so, what they did was for kathiria m-- at, a certain block they said we're going off in a different direction. From. The main network and, this. Direction is going to give the money back we're. All going to agree this money goes back out of that account into, this account into. The DAO account, and. So, there was a rift and there were two aetherium, forks that that, were that are now out there and. The. Etherium that I'm talking about here is the main net the one that forked, the one that gave the money back to the dowel that's the one that's got about five times, the market capitalization of the, other one by the way bitcoin is also forked into do, different Bitcoin cash and and Bitcoin, BTC. And beat th, and its, forked because, of differences, in opinion, between the, people writing the code for the network the ones there, was one faction that said we didn't want to make the network execute.
Faster And have larger, blocks of transactions, so, they and. Another group that said no we're not ready for that so, they. Forked now. Bitcoin, was, the side that didn't, change the. Algorithms Bitcoin cash, is the one that did and now, that's about one-fifth the market cap of the main Bitcoin. So. Let's take a look at it smart contract business process, you have a buyer you, have an escrow agent, you have a seller and the. Business, process is the. Buyer. Gives money to the escrow agent and, when. Everything. Is approved about the sale of the house then. Bob. Gives Alice the house effectively, the, titles transfer, now, you can encode that business process into a smart contract where, the escrow. Is basically, baba alice, and eve the. Escrow agent agree. That. They return the money back to Alice if Bob and Eve agree they, pay the money to Bob and otherwise. They. Split the money between Alice, and Bob but in the case there's a dispute so, the escrow agent here is in the middle that a dispute, resolution is encoded in the smart contract a dispute between the buyer and the seller where. The buyer is already given the money to the. Escrow agent and we. Can resolve that sitting, right here in the smart contract and coding it in code, and then executing. Functions, to cause the state-transition, here. To. Say signal, basically Bob agrees and the way that Bob can off show, proof that he agrees is by. Signing a transaction. That says he, agrees and that transaction, is a call into the smart contract and. Changes, the state of the smart contract to Bob agrees and then. Alice, can. Choose to say I agree or just don't agree she. Can sign a transaction, that indicates her, choice and that way. That kicks off the next step in the transaction, in. The smart contract which is just to say okay they don't agree so. If. Alice and Bob. Agree. I guess that don't. Agree is not in there then. We've. Got the escrow, agent in the middle to kind of resolve the dispute and they'll be the pick Alice or Bob and the money will go one way no there so that's just a very simple example of a business process, that's encoding a smart contract now there's other, kind of more frivolous processes. There. It encoded in the smart contracts on the theorem network how, many people have heard of crypto kitties, so. Quite a few of you this if. You can go to that URL right there you can buy yourself a, kitten. Now. As kitten, exists. Only in the the, if there am blockchain, and it's. It's. Randomly, generated, kitten so. It's got there's like 1024, characteristics. Or genes that these crypto, kitties have they're. Randomly generated, and, what. Happens is, depending. On your genes that you get randomly generated you get a different looking crypto kitty with different characteristics different, colors different eyes different tails, and. What's. Happened, is that people have. Decided, these things are really cool. And. They're. Starting to collect them in fact, somebody.
Actually Spent a hundred thousand. Dollars for, a crypto kitty so. You can have your cool-looking crypto kitty you can offer to sell it to somebody and then. Get ether that then you can transfer, into real cash and so somebody's spent. $100,000, of ether to get somebody else's cryptic Kitty that I thought was really cool, over. Twenty million dollars have. Been spent buying. Crypto kitties so. This, is an, interesting phenomenon. Now. The other thing you'll see on smart, contracts our initial. Point offerings, so. I've talked about Bitcoin, aetherium but, both are platforms, that you can use to launch other currencies, on top of them and this. Is called an ICM, how many people saw a Silicon Valley this Sunday by the way the show HBO, show so, if you haven't seen it Pied, Piper the. Fictitious company there that we love because they're an azure customer. They, launched an IC o---- Pied. Piper coin, so. Everybody's. Getting into it and you can see the amount the initial, point offering is like you know a public sale I'm gonna create a new token and. When. You set. You can sell the token then for the. Cryptocurrency that you, want so ether. Or Bitcoin, whatever, networks on and people. Can buy coin from you and then, you get the money and you can see that this. Is the way now a lot of companies are raising money as through these icos over, for billions been raised regulators, are like wait a minute this, is like an initial public offering of stock sale but it's done on, cryptocurrencies. On this blockchain that's the centralized nobody has control of it and so rules. Around that are still vague. Let. Me now take, you into a theory and smart contracts and, what, I want to do to demonstrate these. Are theorem smart contracts is. Today. I'm gonna launch mark, marks. Token I'm gonna do an IC o---- today. That. I hope you all by. No. Actually this, is I'm not really launching an IC o---- today but I'm showing you what it would look like and, how. Easy it is for you to do your own IC, o---- this. Here, is an, editor, here as visual studio and it's got the solidity plug-in, for it and this. Is a smart contract I've got here loaded in a visual studio it's more just Mark's tokens contract.
And, I'm, gonna show you some. Of the code. In here we've got some safe math that safe math. Necessary. In any smart contract, that does math to prevent overflow and underflow because, if you do that and you're playing with crypto currency you can really screw. Yourself so, you want to use safe. Math functions, and. Then. You can see I've got something here defined as an interface. This. Is the ERC 20 interface this interface, is the standardized, interface for tokens, built. On top of the etherium blockchain so. Any, IC, o---- on the etherion blockchain, is going to implement, these interfaces and, that allows tools like we're gonna see in a minute be. Able to look at the tokens that are implemented, by this smart contract, that i've got here you. Can see that there's functions like what's the total supply of the. Coin the token I can. Call, f
2018-07-17 18:14
Timestamp pls
no. 3
Foyzul Karim Text +1(631)3644664 To triple your bitcoin In few minutes it’s real and confidential
Bryan Bagayas Text +1(631)3644664 To triple your bitcoin In few minutes it’s real and confidential


how can we get the slide? you don't even give the channel9 link here