Onion adventures how to use onion services & the Tor network in your web endeavors - Silvia Puglisi
So. I'm Sylvia. Some. People that know. Me you're lying know me as hero, I. Work. At that art project and I'm, got my PhD not, too far away from here actually two or three minutes working at UPC, in Barcelona. Researching. Privacy and security of information. So. Today, I'm going to talk about tour and how you can use it especially. We're. Going to talk about how. To are provides, privacy, about how it provides anonymity. About. How you can use the tor browser and, then we're going to talk about honing services. Which. Is something, to start as a toy project, but it's actually a very cool feature to lets you use the Tor network. And. The, last point is how, you can use runyan services, for. Your project, personal, project, or your web applications. So. What is story and what, you can do for you especially. Tory. Is a privacy tool which. Is the. Biggest wider, definition that, I can give but. It's also free software, it's, a community of people. Develop. Over. Tor research. There. Are relay operators, that done runs the, tor. Nodes that, you can use when you connect through the tor network in, the lab volunteers, that. Do lots, of different things. So. Is a noble network is also no profit. So. There are about 2 million daily users using. The Tor network and. These. People use. The latter for a bunch of different things that sometimes, we don't even know but. The. Example, that we, always give is that the biggest services, on the Tor network is, actually Facebook, and it's used by people that couldn't, reach Facebook, otherwise. There. Are about six. Six, thousand relays and two, thousand bridges. Relays. Are actually node in the network and, bridges are actually unload that, allows you to get, into the network in case there is censorship. In your country or things like this. This. Is actually interesting the lower graph is the. Bandwidth use in the. Upper graph is the pend wife advertised, so, this shows the capacity of the network it's, about 200, Giga bits per. Second bandwidth, advertised, a little, bit more actually. So. We. Said tour provides privacy. For. Its users provides, anonymity. We, can also say and it's always the same thing it's also provides communication, security, and, if. You want to look at in a more technical way it provides a traffic analysis, resistant, communication, network that's. The. Long. Definition. In a way, but. For many people that you store especially, in difficult part of the world just. Which ability, or it's the possibility, to read the news so. Our, daughter. Provides. Privacy, and anonymity. So. We. Talk about privacy by design. Third. Provides privacy by distributing, trust when, you use a VPN. You. Have a certain some, privacy, properties, but you have to trust the VPN provider you have to trust that the people you pay of you're, asked to provide the services, will not. Sell. Or give. Access to do your metadata or even your actual communication, with. Or you don't have to do this you, just have to. Use the protocol. So. How does it work exactly the. Way. Hollis and every. Cryptographic talk, the rizal is involved and. The one to talk to each other in this case Ollie's can be some user. That has opened the tor browser and he wants to access a website like, the BBC CNN, or any. Website so. Ali's, open, the browser the browser are, some software in it and receive. The list of, nodes. That she. Can connect to in order to reach Bob. Giving. These notes, Alice. Builds a circuit over. The Tor network and, is able to talked. About. The. Green. Connections. Are encrypted, and are within the Tor network. The, last op is, actually, unencrypted, so, although. Someone. Looking, at the traffic of. That, is reaching would know that this. Communication, is coming from alleys they. Will still be able to read what the communication is about if they're not using like a safe. Protocol, for example HTTP. So. For. Example passwords, and so on will be in the clear in, that case so. That's why it's important, to use still. Encryption, or encrypted, protocols, and so on. And. Then if at, a later time, Alice. Wants with another website that's, called chain. There. Will be another Secretary's. Built so that it, wouldn't be possible to link the two activities among, the website and it is particularly important, for tracking across different, website, so. The. Property that the Tor network provides. Is that Alice. Can, in a way communicate. Safely, meaning, that someone. That. Is observing, the traffic doesn't know where Alice is going and someone. That is observing, the traffic from Bob doesn't know who.
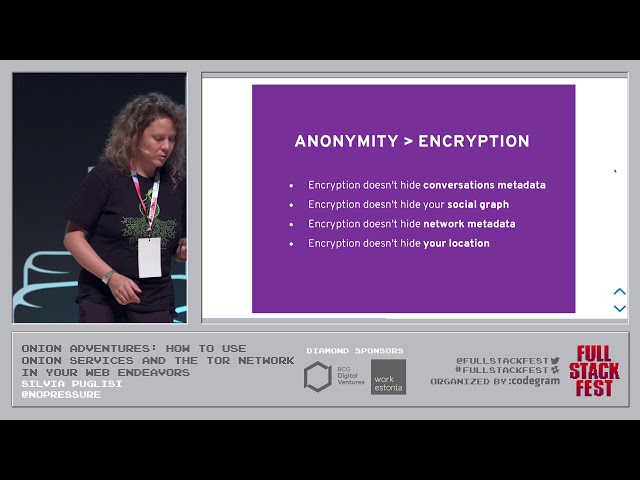
Is Coming from this traffic so. And. Also the other thing that is actually important, is Holly's doesn't need to trust any service provider or network provider in, order to think that, the. Communication, is happening safely, because it's encrypted. And. It's. Not just encrypted, the communication, is anonymous, and anonymity, is more than encryption. There. Are a lot of things that encryption just doesn't do I made, the VPN example. That. You need in in a VPN or in a proxy you, have one cable coming in or 1/3, more traffic and there, is a stream of traffic coming out, someone observing the traffic would be able to. Understand. For example who, is talking to were the people that are talking together and. This. Actually called metadata and was, serving metadata you will be able to for example understand. The Friends of a person of the people that, are connected, somehow and. The. Tor network protects, against this because, there is not one single point of failure everything. Is distributed, on the network. The. Application, layer of the Tor network is, the tor browser. So. The. Term browser basically, it's, Firefox. Des. Modified, a package, with, some. Software. The, starter, and provides. Some. Privacy, and security properties. This. Software is exactly, tor tor launcher to bottom but also no script and HTTPS, Everywhere, so. No. Script is action and extension, that's blocked some kind of JavaScript. In certain situation. So. Why, do we have a browser. First. To, ensure the safe use of tor and, also. Because, we, believe that people. Should be able to surf the web without, being linked. Across. Different, website visits. And. That. Protects against, rough traffic. Analysis, for example and even through tracking on websites. So. Now, we talk about onion, services. Onion. Service is basically. Let's. Go back one second are a way to provide bi-directional. Anonymity, what. Does this mean it means that I can connect our website or I. Can talk to someone and they. Don't know that it's me that is talking to them while at the same time I protect. Also the server location. Next. Generation onion services, were launched. And, they, had some other, features, that were introduced. For. Example, one of these feature was better, cryptography. We use sha-3 now. The. Service address is. Now the public, key of the, service directly. And. It's one very. Good property is that you, can create sub keys from the main key so that you can share different. Keys with, different for different purposes. Of different, people for example so. That the, main key can stay hidden and. Ensure. That they dentally of the of. The. Service and remains. Secret. In a way. There's. Also render for single onion services. I'm. Going to explain a little bit this later but the idea is that when, you use an onion services. You. Connect to tor network and, to. The store network either. The server and the user connected, to the server they have a three opps each. So. It makes three. Ops one side the, render vu node and three ops so just sometimes, it's. A lot of ups and some, people say for example, that there, are situation in which the server doesn't want to protect their identity, or location. Like. For example if you're connected, to the BBC or Debian dot-org so. You just dis, in this case the server connects, directly to, the node and the, user has, a tor network, using. The Tor network out of three hops to, this node we. See this a little bit later. And. Then, there are some other features, for example that. Were added to, avoid. Some, some. Attacks that, we're doing to discover, who. Do service, to and who was talking to them. And. Also some other things. About for, example the description I did there is some information that is shared with the network when the service connects. So. Let's, say how actually an onion service work. So. Let's. Say that Bob, this time is a web page again. And the result is alice. Is using, the tor browser so.
Bob. Wants to say I'm. A new service on the onion network so. What, it does is it picks three point three nodes on the network these are three relays, and just. Build a circuit. Building. These secrets. He puts. Everything into files they did the descriptor, and he sends it to the directory, the directory is, called hidden service, directory, because in the past onion services were called hidden services, and then the name was changed, for. Press reason, actually. So. The. Directories, like a database of the, services and. Later. On, when. Alice wants, to connect, to Bob and knows that the onion service exists. Alice. Can fetch the descriptor, from the directory, and learn how to reach Bob because she. Will know that there are three nodes in the network that allows. Her. To connect about so. Also. What what, Alice does it, picks another node that is called render vu point. So. Using. The the, first, node. In, the, circuit Alice. Tells to Bob hey Bob meet, me at the rendezvous point. So. What. Actually happened, is that. The. Previous circuit that, Bob created. Is destroyed, is basically discard, and, both. Alice, and Bob connects. The render point, using. Our own on tour. Circuit, so it's Riyadh's, and they. Share a secret to, enable end-to-end encryption. And. They. Just use the, letter circuit, like normal. So. There are interesting property. Of the onion services, sorry. The. First property is that this communication, option, opens, entirely on the Tor network it doesn't go out and. When. So. You don't have to worry about HTTP. Other protocols, for example because it stays within it or what. This means is that if, you want to. To. Connect to Bob in. Theory and Bob was a service, that you're using you wouldn't need to expose. This. Service to the outside Internet you, could just expose it on the Tor network so. This limits, the attack surface in, a way, let's. Say that Bob were just providing SSH. Access or, something else he wouldn't need to expose, anything. Outside, of the Tor network it just could. Be, inside. And this is actually interesting for example for. Some. Some. Situation, in which you would like to, to. Protect. Your. Infrastructure, or you would like to share a service, privately, with other people, and we will show this work. Ok, so. This. Is the idea of saline what if you could use, the. Tor network. With. Another application through, onion services, and this. Is the thing that I would like that you take out of this or you like to see, that it's possible that, is not complicated and that, it's. Actually useful and you could experiment with this. So. There, is this idea about on your micro services, maybe. I've. Been thinking, about a. Web architecture for, example you have a web server you, have an observer, and, your. Usual communication, come to the web server and the web server for example is exposed, but, you need to expose the observer, so. Of, course you can use not for example but what if it's not on the same network and so on you're gonna connect just through onion services, and, you. Wouldn't need to. To. Worry about certain, kind of attacks for example you will need about what, about others but not all of them. So. I made an example and to, show that.
It's. Not a complicated, to. Expose. An onion services, on the Internet and, this. Is just a minimal configuration that, you could do. By setting up a docker container. So. I used Tokyo compose in this case and, I. Just, set up the. The. SSH, server and nothing more basically, if. You see the thing that I ever stole, it just OpenSSH. Server tour, and VM to edit some files and, that's. Everything. You need to do to expose, an onion service basically. So. The. What. We provide is, a configuration, file, that you. Can edit and the, configuration, file may be a little bit complicated at the beginning because it's used for everything it's. Used if you have to run a relay if you have to run a breaker if you just using. Tor, but. In this case if you need to you just expose, a service, you would have to to. Say the Indian service directory, where Tora saves a few, information, for example like tea on Dicky and the, onion address and just. Says the port and the. Port that is exposed, and that's it it's, two lines that you would need to edit in this file and. Then. One, store started. And, in. This case for example the, idea, was that there. Is a user called tor and an, onion sha, servers for the is created, in. The home or. Anywhere. You wanted and that's it and if. You wanted to expose more services, you just added, to, the configuration, files with the folder at the port and and, everything. So. In this case if you the, idea is that you just could. Start. Docker. Container from your machine and then. When you would ssize you, willed ssh to the onion address. But. Using to our socks. This. Is another thing. The. Socks is a ruptor there is provider when you download, or install tor, and. Basically. What it does is routing, your traffic through. A socks5. And. Using. Tor so. Basically. You. You, could run a card, you could run any other protocol. Through, tor. Sox and it's using the Tor network and, in. In, the past we. Used to call it our Sox 35, because it's a way to make application. Work on door. And. We actually provide a no - it's, a little bit of a working process, because. It contains, a lot of information. About, when, and how you should terrify an application, in, order to know that. When. You expose a service, through. The Tor network you have to make sure that are also not leaking, other information. But it's. Actually for. Example a. Cool. Feature you can use just to know I have want to try this API, how, can. I reach it through the Tor network it does your work does enough work, what. It does, always. From. The I way around it's a way that you can you can expose a service, only on the Tor network. So. This, is another example and, it's, a few, line of code in Python that, allows you to use, the. Sox 5. Proxy. There, is provided, by tor and it's what tour. Sox use. So. I. Didn't. Install anything specifically, I think request. Comes with Python if not. It. Might not come with Python but you you might have to fetch request which, is a library and the. Thing is that you need a library support, communication. Of a Sox 5 for Sox in general on some, programming languages unfortunately, do not support that I tried, to have also really example but I heard that in Ruby support for talk Sox fire is not that good, which. Is a shame cause I really love Ruby and. Then. All you have to do is to a get and tell. To use the proxies, and, in. This case even, the. DNS requests, go through tor, so you wouldn't you wouldn't have the DNS request go outside, of tor everything will be within tor and you will be able to fetch for example unknown, address or, in, this case the.
Union. Address is the address for T archives, or project at work. So. The. Other idea is that what. If. You. Can use tor, for. Peer-to-peer. Application. And, there. Are lots of. Example. That you could do ssh, was one example here. On ssh, server and, you address it only fruit or the, touch surface is smaller, you. Make, advantage. Of not pod, so. You. Make advantage, of the. Sense. Of super system property, of it, but. There is also. Another. Example is using secure drop for, example a use, an onion services, and, but. Also there is this, small. App its colonial, share and it's used to share webs files. You. Basically, when you use it you select, a folder the. Folder is zipped, the. App start an onion services, and you also start a flux flask. Web server and provides. You with an onion address that you can share with people as long as the app we're running on your computer so. People download. The files you, get actually, a counter, of how many people have downloaded the, file that you shared so that in, case someone learned you an onion services, ye, you. Wouldn't be able. You. Will know that lots. Of people that download the files and. And. That's it you closed, yeah and it's, basically done. It's. Shared. Safely. And it's. Shared. Peer-to-peer. Because, it doesn't even go in the network its shared over the Tor network and that's, it, so. The, other idea, was. Like what if we use this property, of. Onion. Services, and, buy. We. Start building application. There are peer-to-peer for, example, or we, start using onion services because we want to share. The prototype, of application. That I've been working on my computer and I, just want to share it with a co-worker for, example or just, say ok I want to. To. Work on something quickly and, I'm. Going to provide an. Onion, link people, had to access the onion link while, they need it and then I shut it down and that's it so, tell us what. Do we start a container, and the. Container is, some some, image that I want to share because for example I have a web server or I, have an application server and so on and. After. Wrapping. A simple example I mean this is probably minimalistic. There are other things that go into it but the, idea is that you'd annoying you don't need a lot of line of codes, to. Start experimenting with the tor network and, start building secure, application. It's. Actually, there. Is for example in this case I'm using docker, because he was convenient, and there. Is a docker. Library. For Python, so. You. Import. You. Install at the library you import it and then. You just say I connected, the docker socks and that's it and then. What you do is you, provide a docker file and you. Start the container and then, on that container you decide which services, you want to use and. Let. Me put the dock before I love. I'm. Lost with. Ok. No. I didn't, want to do this okay, but. Basically. I'm the dockerfile, I'll try to narrate it. What. Happens is you just stole the. Container what you need installed so you need engine action you can use the nginx, image that is provided by doctor and you, just add that you want or installed, once. You are touring solid just provided, to our C files with the service that you want exposed, in this. Case the nginx or whatever and you, just launch change in X P. And you make sure that toy is launched as well that's it and once. So. Basically. So. Once, you have something, and you have an address you just share it through. The, tor browser like, this and. If. It was not just an engine X Server it could, be an application that you wanted to share it we have to peer and. If. You have or if you, if you have issues with censorship, or if you live in a country where some.
You. Don't want to. You. Don't want people to know that you're sharing something online you cannot. Afford hosting, this runs directly from your computer and it's a quick way to. To. Build up basically, an application and share it with whoever you want. So. This, is basically. The end of my talk I don't, know if you would like to send. Some more, questions through, Twitter or. Tori's. Traffic. And analysis, resistant, you said that you don't usually, know, what people are using it for you. Also said it is commonly, used for Facebook access, so. How. When, and why is some. Traffic monitored. So. We, know, that information because, it's we, have some metrics and that information, is provided by Facebook also, okay. So they know how many access they have through. Tor for example, and. We. Garni the first question, basically, you don't have to trust the network it's the first thing because, you, trust the protocol, the, protocol is open source there is a design document and if you want to contribute to the code or to the design document, look a look at it and another, thing is also that. You. Know the people that are working on tour so basically. Many. Tour developers, many people that work on tour around the give talks they say hey I do this so, that you are publicly, publicly, identifiable. And, people. Know that actually there is no some. Hidden. Service. Behind. It and then, another thing is yes, if the communication, is not encrypted there could be analysis. On the exit node or, also. There could be analysis, on the axis nodes of, the traffic that is coming from but the. Axis node only. Knows that there is a middle node that is sending traffic it. Doesn't know the. Person that initiated, the communication so. The Tor network provides, this, property, that I, used, at our network and when. I visit a website the, website doesn't know where. The traffic is coming from but people also they're observing my, traffic, they don't know basically. Where I'm going which, is which, websites, I'm actually I do want to be sitting I'm visiting ok. Ok. I will, I, will, ask, more questions later, because, there's. So many I apologize, for the people that I want, cite, here, so. There. Are two questions about. Reliability. From. David. On Twitter, did, you ever detect, any attack on Tor network aiming. To bridge its. Security, and the. Other one, is if. Eventually. On, your service you start to be used as a way to protect services, from attacks. Wouldn't. That heavily increase traffic and so penalize, traffic. Of the users, that actually, need tor, to access information. Ok. Can. You repeat the first fraction it's basically, about the. Resistance the resistance and, the first one did, you ever do, one. Of the most gonna talk on tour is. Music. Building, a relay anyone. Can build a relay and the. Four properties of the networks when real I spend more time on the network they they get, promoted in, a way for, example that relay can become.
Hidden. Service directory, and, so. What, people that. There is some mitigation. To this in which we run, some. Analysis. On the network to find bad, relays. And. Actually. The. The. Algorithm that does this is the only thing that is secret because. We don't want people to have an advantage on this. But. The, thing is that. When. When. When. A relay is in the directory, there are some attacks they can do to, find out who. Is the hidden services, and who is trying to talk to the hidden services but, just observing, the traffic, and there. Are actually. A few class, of attacks one is timing attacks trying. To understand if, this, person. Is making up the connection, and if these, hidden. Service is replying, try to match things for example it's a little bit more complicated, but. It goes around these lines and, the. Other question is about resistance. If. Eventually on your service stuff to. Be used as a way to protect services, from attacks. Property. Of the. Tor network there, is the diversity and, this, means diversity, of traffic, of relays. Means, small, relays big, relays, realized. On. The same network relays there are different network I'm going to explain this because it's a little bit. May. Be difficult, to understand but, it. Goes with the idea of. Population. Or people, that are similar if. All. The people the like sports only, used it or network people will know that it's, only. People the like sports and the, traffic is about sports if there, are people that likes lots of different things like sports music or. Business. Whatever. It. Done will be more difficult to identify single. People so the diversity, of the traffic, news so, let's say web. Surfing. Protecting. Infrastructure. Or other uses chatting and so on. Gives. The possibility to, mitigate. For example on traffic, analysis, but. Also the the difference in relays meaning, that if all the relays that people run are, on the same network for, example digital, ocean, then. Digital. Ocean will have a lot of traffic, that they can analyze or. Amazon. For, example or other thing so this, property, of diversity, of people using tor for different, things such, a good thing for tor yes.
But I think that the question was more about the. Resiliency. To, heavy. Traffic like, woody, where, you get very, slow. So there I I, need. Be. Able to add more relays, and be, able to support more traffic ok if, we have people. That use it more for example. One thing that is I. Think. The, beta or alpha version. Of brave when. You run a private, tub you can run it within tour so that it's a little bit more private that. Just an incognito top because it's not only blocks. JavaScript. It'll only blocks, tracking, they also send, this traffic in this browser tab through the Tor network. Ok, I, think. That I have. Some time for a last question. Peter, on slack asks, are these, relay nodes. These. Really, knows you would route over verified, parties, and safe to use or can anyone have or create a relay node, anyone, can create a new rail a relay node, even if you have raspberry. Pi for example. It. Would be just a little bit more. Flocking, in terms of the network bandwidth. That you provide so for example you won't get promoted. But. The idea is this that the network is owned by the everybody nobody at the same time, and. I, think there was another question about running, bridges. So. It's the same people that run realize they, can say I've run a bridge and. So. When, it's. Basically, a choice that you, allow people, to use your bridge to enter the Tor network. Okay. Okay. There's, plenty more questions, on slacking, on Twitter enough time I. Think. We. Can. Let. You some time to answer. Them one. By one. Calmly. Okay, thanks. A lot thank you.
2018-10-12