How symmetric and asymmetric encryption and digital signatures work
Hi. I'm Nicolas be the IOT, ecosystem manager. At Texas Instruments I'm, presenting, a series called understanding. Secure, connectivity, in, IOT, and embedded, systems devices. This. Module, is entitled how symmetric. And asymmetric encryption, and, digital signatures, work and. Will focus on explaining. Symmetric. Encryption. Asymmetric. Encryption and, their multiple, use cases of, asymmetric, encryption including. Key exchange. Authentication. And how asymmetric, encryption can, be combined with secure, hashing, to create digital, signatures. Before. We dive into the specifics of these different, types of encryption, I'd like to relate them to the core, security, concepts. We mentioned, earlier, confidentiality. Can, be preserved by both. Asymmetric. And symmetric encryption. Since. They encrypt the data so, it cannot be looked, at by a third party, authentication. Is, delivered by digital, signatures. Certificates. Which we'll cover in the next module, and, message, authentication, codes. Which are associated with symmetric, encryption. These. Each cover different aspects, of authentication. And we'll break those down in more detail, later in this module. Integrity. Is handled, by both, digital, signatures, and message, authentication codes, again and, finally non-repudiation. Is. Handled, by digital, signatures, which help prove, the, origin, of the message and whether sent, and received we. Won't be covering non-repudiation, any, further in this module. Before. We jump into, the specifics, of any particular, type of encryption I'd like to cover and explain, one more important. Concept, that's the difference between entity. Authentication. And message. Authentication. In. Entity. Authentication. You, have your end device, such as a sensor. Contacting. A server and the end device wants, to know it's connecting. To the, real server, it meant to connect to and not to some imposter, for, example, who's mounting, a man-in-the-middle, attack. So n steals. Education, is a one-time. Operation. Done, at the start of a communication. Session to, establish, yes I am connecting. To the, right party. Once. You've established that, you're talking to the correct party, there is still a risk at some time during the conversation. An attacker, might insert. Messages. Into, the conversation. That you would then assume, were, coming from the correct party, this, is where message, authentication, comes. In with, message, authentication, you. Are checking that, the actual message you received, came, from the party you connected, to an. Addition, message authentication or. Check the integrity of any message, to deal with issues such as corruption, due to transmission. Errors during the, sending, of the message so hopefully, this is clear entity. Authentication is. Something that's done just at the start of a communication. Session when, you validate. The party, you're connecting, with is who they say they were, message.
Authentication. Validates. That every message, in that conversation came. From the party originally. Connected, to. We're. Now going to look at some specific encryption. Technologies. Starting, with symmetric. Encryption. In. Symmetric, encryption a. Single, key is exchanged, between both, the endpoint. And the server. The. Same key is used at, both ends, to encrypt, and decrypt data, so, one, key is needed for. Data, to be encrypted, by, the endpoint, sent, to the server and decrypted, by the server, and then, that, same key is used by the server, to encrypt, its data send, it to the IOT endpoint, which again uses that same key to decrypt, it so. A single key, some. Of the ciphers, you'll encounter, they're used in symmetric. Encryption art, AES. Which is by far the most popular there's. Triple. Des and, then ChaCha. 20 des, and triple des are both being eliminated in, TLS, 1.3. So ChaCha, 20 is really, alternative. To AES. The. Main use of symmetric. Encryption is, for bulk, encryption. So the great majority of encrypted, traffic going, over the Internet, is encrypted, using symmetric. Encryption and. The reason why that is is because symmetric. Encryption is, relatively, CPU, efficient, and certainly much more so than asymmetric, encryption as, we'll discuss in subsequent slides. The. Key weakness of course a symmetric, encryption which, you may have already realized, is you have to exchange the. Secret, key between, the endpoint, and the server and the question then becomes how do you get that key from one party, to the other without, it being intercepted. By an attacker who can then decrypt all, subsequent, traffic, we'll, explain, approaches. To exchanging, this key in a safe manner later, on in this section. Symmetric. Encryption ciphers. Are typically, associated, with message. Authentication, and. If you look at common. Symmetric. Encryption, ciphers. Such as AES, they're often paired with, some, form of message, authentication so, you'll see combinations. Like AES. GCM. Or ChaCha. Xx poly 1 3 0 5. The. Purpose of message, authentication. Is, as we described, earlier to, verify, that the. Messages, have not been tampered, with and, that they are coming from the original, entity. You authenticated. Early on in the communication. So. How they work is simply this is that they generate. A message, authentication, code. And that's computed. By taking, a, hash of the message and, combining it with some. Form of sequence, or, session, number to make sure that replay. Attacks cannot, reuse packets. And also, uses, the symmetric. Encryption key. As part of the message, authentication, code. Generation, process which. Then proves that it's part of the message, stream. You're using because, obviously that message stream also uses, the symmetric. Encryption key. To summarize, symmetric. Encryption, ciphers. Are typically paired which message, authentication, techniques. And a message authentication, code. Proves, a that your message, has not been tampered with, and be it is legitimately. Part of the conversation. You've been having and it hasn't been inserted, by an unknown, third party the. Second, form of cryptography. Is. Asymmetric. Cryptography, the reason, why it's asymmetric. Is because it does not use a single key, at both ends, to decrypt, and encrypt, data, instead. It uses a key pair, to. Exchange data, in, one direction. So. Let's. Take this example here, where we have a server. That wishes, to get encrypted. Data from, the, endpoint, the. Server will send what's known as its public, key, to, the endpoint the. Endpoint, will then encrypt, the data it wishes to send with the public, key it. Sends the encrypted, data back. To the server and, then the server uses. A different, private. Key to decrypt, the data so. In asymmetric cryptography, there, is a public, and private key pair which. Is used to encrypt, and decrypt data. Now. This key pair works in just one direction so, the public, key is sent out to, the endpoint in this case so the endpoint, can send encrypted data. Back, to the server if you, wish to have the, service. And encrypted. Data to the IOT, endpoint, then the IOT, endpoint, will also, have a public/private. Key pair and, it will send its public, key to the server which are they encrypt the data send. It to the endpoint which, will then decrypt, it using its private, key so you can see here that we actually need four keys, to, do the two-way. Communication. That's. A public, and private key, pair at, each end of the, connection. Now. One. Important, thing about, asymmetric. Encryption is, the public, key is designed. Not to be a secret, so there's no problem, in sending, the public, key, out in the, open over, connection. However. The private, key must. Be kept secret but because you never need to transmit, it anywhere it's much easy to keep it secret than in the case of symmetric, encryption where, a key must be shared between the two. So. Talk a bit more about asymmetric. Cryptography, it. Has one big weakness, compared to symmetric, cryptography and that is that it's very very, compute, intensive as.
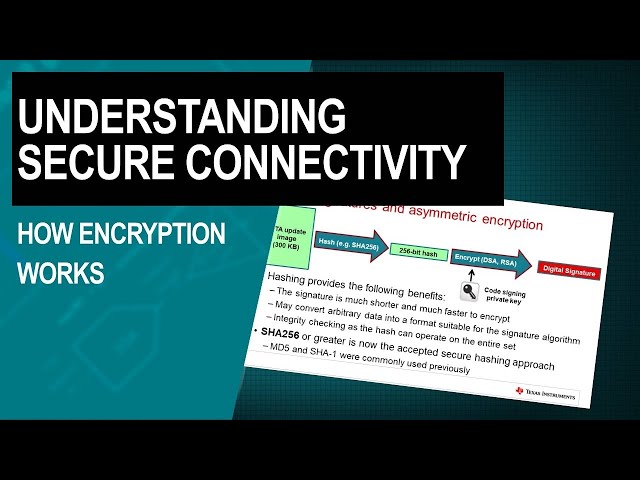
A Result, these, symmetric, cryptography is not used for bulk data encryption, its, primary used for two functions, one is key. Exchange, so you. Can exchange, a. Symmetric. Encryption key. Over. A network, connection in, a secure, manner. The. Second, use is authentication. And, asymmetric. Cryptography, techniques. Back, both, digital, signatures, and the. Public key infrastructure, and certificates, and we'll go, into both those uses. In more detail, on subsequent, slides. There. Are two common, asymmetric. Cryptography, technologies. One is RSA. And the other is ECC. Which stands for elliptical, curve cryptography will, briefly discuss, those before, we go into exactly how asymmetric. Cryptography is used for authentication and, key exchange. The. Two principle, asymmetric. Cryptography, technologies. You'll encounter, are RSA. And, ECC. RSA. Is able to perform both, authentication. And key exchange and, historically. The great majority, of. Certificates. Issued, used. RSA. Base signatures. However. TLS. 1.3. Which is the latest, release of the key, internet, security. Protocol. Is. Eliminating. The use of RSA, for key exchange and retaining, it only for. Certificate. Signing. ECC. Is a slightly, newer. Asymmetric. Cryptography, technology. ECC. On its own is simply, used for authentication. Methods. As digital signatures. But it's paired with an algorithm, called diffie-hellman, to, perform key exchange. So when you see ciphers. That start, EC. That means elliptical, curve so EC, th EC. Th e ECDSA. All. Those things are based on elliptical, curve cryptography. Elliptical. Curve cryptography is, like to see growing use in the future it has smaller, keys and better performance than RSA, and scales, better as the key size Grove. Because. TLS. 1.3. Will. Not be using RSA, fat key exchange, are examples. Of key exchange I'm, just gonna use sign cord EC, th e as this. Is now going to be the common mechanism, used going forward. One. Common. Use of asymmetric. Encryption is, digital. Signatures. Digital. Signatures, are used to, prove. That, content. Coming over and network connections, such as a software, update or, a certificate, or data, packet, of some form did, in fact originate. From, where. It said it came from and, was not tampered, on route. We're. Going to walk through and over-the-air, update, example. So you can understand, how, digital, signatures, are used to authenticate. Content. We're. Starting off with a, OTA. Update, image that say 300. Kilobytes in size to. Make that easy to encrypt, the. First thing we do is we perform, a hash operation. On it hashing. Is important, for a number of reasons but especially. That, the resulting. Signature, is much much shorter than the original data, packet, and therefore much faster, to encrypt, in addition. Since hashing. Is, performed, on the entire update, it also serves as an integrity, check to, prove there was no data transmission. Corruption, in transit. Once. We have the hash done, and the hash can vary in size depending, on the hashing algorithm, chosen, here, we've chosen. Sha-256. We then encrypt. The hash. Using, a paste. Symmetric, encryption operation. Such as ECDSA. Or, RSA. And that produces, a digital, signature, you'll. Notice here that the, encryption. Is done using the private, key of, a, key that's specifically, used for code, signing, to, make some general comments about hashing. Functions, going, forward. Sha-256. Or greater will be the generally.
Accepted Secure. Hashing, method you may well have seen accelerators. On microcontrollers. Or mica processors. For md5. Or sha-1, as, these were commonly used in the past but they are now not regarded. As secure. Once. The digital, signature has been created, the over-the-air, update. Server can now send, the OTA update, image accompanied. By the digital, signature, to the IOT, endpoint, if, you recall in our earlier discussion. Of asymmetric. Encryption it's. Based on key pairs where a public, key can. Be used to decrypt, information. Encrypted. Originally, with the private. Key of the same pair. In. This case the digital, signature, was encrypted. Using the private key held. On the OTA, update, server, each. IOT. Endpoint, has the public key and it uses it to decrypt, the signature, to reveal the hash value sent. It. Then takes, the OTA update. Image and then performs, the same hash function. On that image then. Checks. That the hash, had just calculated, for the image, that was sent matches. The hash value that. Was encrypted, in the digital signature if, these match the, IOT endpoint can be confident, that the OTA update, did in fact come from the, OTA update, server and, was not tampered, with during. Transmission. Another. Important, function performed. By a symmetric. Encryption is, key, exchange. You'll. Probably recall that, one of the challenges, of symmetric. Encryption is. That it needs to exchange a shared key between the, two, communicating. Entities, if, it passes that shared key over, an unsecured. Connection. An, attacker can get hold of that key and then can compromise, or further communication. Asymmetric. Encryption provides. A way to exchange, the. Shared key, safely. The. Main algorithm, is, used in key exchange, today as diffie-hellman, which. Is abbreviated to D H, diffie-hellman. Enables. Both, sides to derive. The, shared symmetric. Key without. Actually, passing, it over the wire this. Has the advantage of, stalling, any attempt, to intercept, it in transit, the, main variant, used today and the one will be emphasized, going, forward, in TLS, 1.3.
Is Diffie-hellman. Ephemeral. An, important. Difference between D, H E and the, earlier, diffie-hellman. Implementations. And also, the RSA. Key, exchange, implementations. Is that a new key, is, calculated. For every, communication. Session, that means it's never stored, permanently on the server this. Has a tremendous, advantage in providing st. called forward secrecy. Previous. Diffie-hellman. Implementations. And also RSA. Used, to use the public, key in the service certificate, as a basis, for calculating. The, shared. Key. This. Meant that if the server's private, key ever became known in the later date. An attacker could then derived, the shared key if he had recorded past, communications. Between the two parties, they would then be able to decrypt them. Since. DHE, does not store, the key use for any session, on the server provides. What is known as forward secrecy which. Means that compromising. The server's private, key is no use in, decrypting. Earlier communications. Between it and other parties. Let's. Briefly walk, through an example of key exchange using, EC, DHE, which is elliptical. Curve diffie-hellman. Ephemeral. The. IOT, server. The IOT, endpoint, begin, by exchanging, a, random. Value, and the, diffie-hellman, parameters. Then, each side uses. The random, the diffie-hellman parameters. They received to derive, a pre master, key and from, that they then derive the, session, key there's. A lot of complex mathematics, behind how the actual, pre, master, and session, Keys is derived which you really don't need to concern yourself with from, a embedded, security standpoint. As. I mentioned earlier since, the keys, are not actually exchanged. Over a connection. They can be computed, in parallel, speeding up the process you. May, be asking, what exactly is asymmetric, encryption contribute. To key exchange, during, the key exchange, is necessary. For each communicating. Party, to authenticate. A data its receiving, from the other and this is done by each party, signing. The data it sends with its own private key which, enables, the receiving, party, to, authenticate. That is indeed getting the data from, the party, believes. It's communicating. With. Final. Common, use of asymmetric, encryption I, want to discuss is entity, authentication, this. Is typically done by exchanging. Certificates. And we're going to cover digital, certificates, in a lot of detail in the next section, I just wanted to show the relationship, to asymmetric encryption here. And how it gets used, if. The, IOT. Endpoint, device for, example wishes. To authenticate. It really as connecting, to the server it thinks it is the server will send, its certificate. To the IOT endpoint, and this certificate contains. A, public. Key. At. This point the IOT endpoint, verifies. The service certificate, via sign called a change of trust which we'll discuss later. It. Now needs to prove, that the server, also. Possesses, the private, key associated. With the public key that was sent in the certificate, once. The IOT endpoint, proves, this it, can be confident. It is indeed. Communicating. With the correct server in, this, module we discussed symmetric. And asymmetric encryption. In, some detail, along, with digital, signatures, which involves, secure hashing. We. Showed how these encryption. Technologies, related to the core security, concepts. Of authenticity. Integrity. And. Confidentiality. We. Also explained, the differences, between entity, authentication, and message authentication. Asymmetric. Encryption for, use in a number of ways and, we walk through examples, of digital, signatures, entity. Authentication and, key exchange. The. Next module in this series is entitled and, introduction, to digital certificates. And a number of the things, you have learned in this presentation, will be applicable there. At. Some point is likely you'll want to do some actual, software development. Of a secure. Connected, application. I've. Put a few links here to enable you to get the appropriate, software. And. Evaluation. Modules, to develop, secure. Connected, applications.
On A TI simple. Link Wi-Fi, device. We. Have an extensive, set of hands-on, training modules, called, simple, link Academy, as you, go there and select you'll, see a number of examples that, deal with secure connectivity secure. Storage and cryptography. You.
2020-01-30