Modernize your SIEM in the cloud with Azure Sentinel SECI50
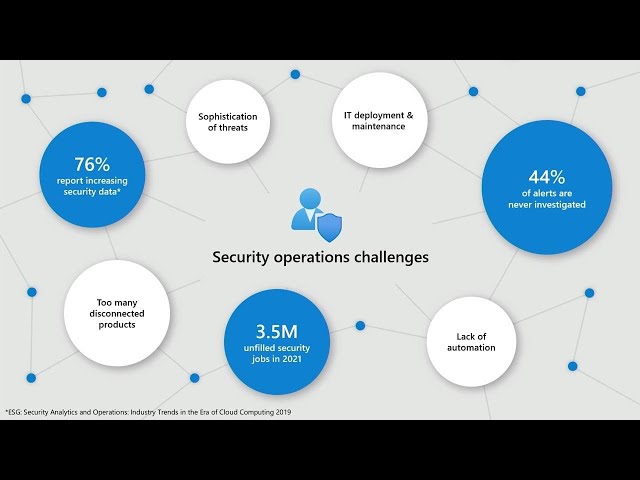
Good. Afternoon welcome everyone. Today. We're going to be discussing how you can modernize your sim in the cloud with Azure sentinel, I'm, kind of excited it looks like they bumped us up to a bigger room which, is very very cool I certainly, think that Azure Sentinel, is going to be transformative. And I've been really excited at the level of enthusiasm and. The response that I've gotten over the last couple of days here at Microsoft ignite it seems that many of you feel. Similarly, so with. That we'll go ahead and jump right in, we've only got 45, minutes I'll, try not to move too fast but we do have a fair amount of stuff that I want to want, to get through today so. So. Today organizations, like, yours are faced with this incredibly. Difficult task, of trying, to protect your expanding, digital estate, from increasing, cyber threats the. Move to the cloud and the mobile workforce have, pushed the border of your, estate, beyond. The physical Network boundary, your, data and your systems, and your infrastructure, are everywhere. And. Of course that's creates some pretty significant, challenges, for your security operations, teams who, are tasked with trying to protect that expanded, digital, estate as, your. State grows so does the volume of security, data in fact, 76%, of organizations, for port an increase in security data over, previous years and much. Of this is coming from the cloud which changes the dynamic, a bit in terms of how you collect, and analyze that data. Pumping. It into on-premise, systems with all of the deployment, and maintenance overhead, that comes along with that often. Doesn't make sense and I. Believe that that volume of security data is just going to continue to grow and grow and grow not. Only do we have this extended, estate, all, of which is emitting. Security signals that we need to collect and analyze but. What is the one thing that's going to fuel m/l its, data and not only do we need more data to inform, those models, but we need a greater, variety of data so, we need more signals, and we need more diverse signals and I expect that that's going to not only continue. To increase the. The volume of security data but perhaps even you know hockey stick that in the relatively near future. So. Our are trying to shore up their defenses. And. As a result they are deploying, literally, dozens, of different security, products and services, within their organizations, these. Are producing a lot of alerts. But. Unfortunately in isolation, these products, are generating, relatively, high false positives, rates or at least they can, and. There's not a lot of guidance across, these various alerts to help you figure out which of them require your immediate attention which, ones do you invest time in, investigating. And researching and, which, are not as high. Severity, are not as likely to be the result of a of a, real attack and as.
A Result we see here 44, percent this number really just staggering. To me 44, percent of alerts are never investigated. 44. Percent so, just imagine what is falling through the cracks as, a result of that and. The. Final thing I'll point out is of course as you guys know there's a global shortage of security analysts that's why in many cases anyway those alerts are not getting responded, to. The. Recent study says that there'll, be 3.5. Million. Unfilled, security, jobs by 2021. That's, a massive number creates, huge challenges, for security operation centers. So. With the introduction of azure Sentinel which g8 just, a couple of weeks ago we. Really believe that we can change the equation for security operations teams, by delivering an intelligent, cloud, native sim. It's. One of the main things that the Security Center or secure, Sentinel. Should say it's. Designed to do is to really meet your defenders where they are and deliver, instant value to them and as, a result it's got hundreds, of built-in, dashboards. Or workbooks, and detections, and hunting queries and analytics, and playbooks things, that they can use off-the-shelf on day one to, improve the effectiveness of their teams, we. Also provide, gun it guided hunting, and investigation. Experiences, we'll look at those in, a few minutes that help your security analyst, regardless. Of their skill level to get their work done now of, course a sure Sentinel offers all of the extensibility, that, your teams need as well the, ability to customize, and create your own analytics, and workbooks, and it, even integrates with professional, grade tools like jupiter notebooks, for the truly advanced security analysts inside your team and. It's easy to get started you can do that with a single workload, or. Perhaps. All of your cloud workloads, but certainly can extend beyond that as well. Secondly. We talked about this couldn't. Have said it probably more strongly the the, growing, volume of security data that exists out there today and as. Your sentinel enables you to collect, and store and analyze. That security, data at cloud scale so. It's going to scale automatically. As your security data volume and compute needs grow whether, that's incremental, growth or if you've got a burst you need to ingest more data as part of a particular incident response, and there. Are no infrastructure, costs or upfront commitments. You don't have to buy servers, and put them in, your. On-premise, environment, every time you add a new data source or multiple, data sources and you only pay for what you use so. This really changes, dramatically, the equation that many of you are facing with traditional on-premise system, technologies. And. Finally. As your sentinel uses ai and Mott and automation. As the force multiplier, for your sock and enables. You to detect, threats that may have been missed otherwise, enables. You to fuse, alerts into. Actionable, actionable. Prioritized, incidents, to. Help reduce the alert fatigue so instead of going for those 44. Alerts. That aren't investigated, you get just a manageable, handful, of them that, are really actionable and, we provide guided experiences, around to. Help you quickly understand. The scope and take action and AI really applies across the spectrum there not only in detection but how we think about you know creating incidents, and building incident investigation. Experiences. For you really baked into lots of places within as your Sentinel and then. The final piece is automation which lots of folks talk about but. We don't see it in practice being. Implemented or. Implemented. In. Meaningful ways that a lot of enterprise Sox, and here automation, is really built in to Azure sentinel in the way that we really think will enable you to apply it to, manual processes, and to speed response.
So. As your sentinel does this all by delivering an intense solution, for your security operations, team, and that, starts of course with collecting, all of your data but. Not just collecting that data beginning, instant insights into that data and we do that through workbooks, which you'll see in a few minutes and, the ability to easily query that data. You. Can begin applying Analects analytics, to that data to find threats that require your attention you. Can hunt through all of that data using built in exploratory, queries and, we even have tools like books marks and livestream which, will help you to track notable, events and monitor, for new activities. You. Can manage and investigate, incidents using. Graphs and, Timeline views again we'll spend a few minutes walking through some of those in a minute and finally. Automate. Investigation. And remediation playbooks. And. I want to highlight there that we're not just talking about using, play, books for remediation, we really need to think about kind of across the set of work that you're doing in your sock how, can I we apply automation, to that and, all. Of this is being powered by a community of security, analysts and it's, backed by Microsoft. Security, researchers. Who, are leveraging, their vast experience. Protecting. Microsoft, services at massive, scale they. Contribute, analytics, and queries and workbooks, and play books and much more which you'll see are kind of built into the azure Sentinel experiences. I'm. Going to take you through ten steps today to modernize, your sim using, Azure Sentinel, for a little bit of structure to to our discussion, hopefully. These will be pretty actionable, for you so you can use this it's a bit of a guide when you get back to your office and you're ready to go implement as your Sentinel this, will be a sort, of guidebook for you to achieve that and as, we're stepping through these just a little bit of a preview I'm shamelessly, giving away prizes along, the way to keep you engaged, so. You'll see some of those pop up along the way and so. Don't leave hang in there it'll. Be worth it I hope. We're. In a storage with visibility, and again, number, one thing there is to be able to collect all of your security data at scale, from, any source super, super, super important, and that, starts by collecting data from not only your on-premises, environments, but all of your cloud environments. Not just your Microsoft, clouds but your other clouds as well and so. We offer a number of ways to do that for. Our and Microsoft, 365, so, being able to get your security, alerts, and activity, data from those sources you, can enable them and literally, one-click, I'll, show you how to do that in a minute so those, are just built in as you might expect baked. In to. Azure sentinel, super super easy to turn those on, we. Also offer a series, of collectors. For, both Windows and Linux and, these can collect a variety of different kinds of logs. And we. Prefer her often those. Are you leveraging the common event format Steph if you're familiar with that that's, sort of a standard way that lots, of security technologies. Sort, of format their data, for. Ingestion and sim and other kinds of technologies that's. A pretty common way to, ingest your data and to Azure sentinel, is using, collectors, and the Ceph format, we. Also have a couple of specialized, connectors, that are available for, your threat intelligence data. One. Of those is, through, the Microsoft graph security, API, and. You can do that you can call the API directly to, send indicators, into as. Your sentinel we also have native, integrations, with a number of threat intelligence platforms. Threat, connect mis, which is the open source solution, and many others so, if you're already using one, of those tools they're already integrated turn, on the connector and you can you can send your threat intelligence data, through that and then we just announced, this. Week support, for a new taxi, data. Collector, which enables you to, send. Data into. Our taxi. Client. In, the sticks format, so, if you guys are familiar six taxi kind of a standard.
Protocol. And an. Schema for threat intelligence data, and we now support that as well and. Then, finally you can send data into our REST API is those, going to custom, log tables and master. Sentinel so think about just the the wide wide, variety, of different security data that exists out there those. Certainly. Can we can ingest those logs via the API if the other methods don't. Support them already so. That data is coming in through those those, for data connectors, and. Is going into Azure monitor, log analytics, so, we leverage log analytics, since our underlying data, store. It's a. Amazing. Platform, processes, 2 petabytes, I think of data a day something like that so, high scale log. Analytics, platform sort of operates, as the basis, for Azure Sentinel and when Sentinel, adds all of the security analytics, that run on top of that the experiences, that we're gonna look at today. So. Once you have your data flowing in I mentioned earlier the ability to get instant insights, from that data and workbooks, are one way to do them so, most, data, connectors, come with, workbooks, and, there's a gallery of those that you can leverage that. Are. Built sometimes by the, folks that built the data connectors, or just, contributed, by other community, experts. So. You can choose from this gallery of workbooks, you, can also customize or, create your own you. Can take advantage of rich, visualization. Options this. Can even include I saw. Today I wasn't aware of this that, you can create. Graph visualizations. You, can also do maps there's a really cool blog post that got, published recently about how to do graphs. Inside. Of as your sentinel using workbooks, and so, lots of different interesting, ways to do visualizations. Using. Workbooks. And they're all interactive, so you can quickly filter, your data and pivot your views so. A great tool for your your security analyst. And. Of course you can use those to gain insight not only into one a data source but where they really become more powerful is when you mash up data from multiple data sources that's where you begin to get probably the most interesting insights. In, your workbooks is when you do that. And. Then. We did announce a number of new data connectors, most of those have workbooks associated. With them as well this, week there's barracuda, and Citrix, and a new. A, data connector for f5 and, turn micro and others and of course that taxi connector. That I mentioned a few minutes ago so. With. That we're going to pop over and take a look at this in the demo. Okay. Welcome to as your sentinel this, is the overview dashboard. We're. Going to move directly though from the overview into, data.
Connectors. So. As I mentioned earlier they're data connectors, for, virtually. All of the Microsoft security, cloud. Services, I should say including the security services, also other clouds so we can see here that Amazon, Web Services, there's, a connector available, for that and the, at. A glance you can sort of see what is connected, those are the green, connectors. Versus, the grey ones that haven't yet been enabled, you, can also get a sense of of the, data volume that's flowing through that connector, when, was the last data received. And any related content, in this cake was workbooks, or queries. That's. Sort of the structure of the data connectors, again that's other. Cloud services Microsoft. Cloud services, Microsoft. Security technologies. Here's. The new Barracuda cloud gen firewall that I mentioned earlier I also. Wanted to point out we talked a moment ago about the comet event format this F and so, if you don't see your product or service on this list there's, a decent chance that. They can be enabled using this kind of generics F connector a, lot. Of security technologies, support this already and and, so it's available as. Well for those services that don't yet have direct, connectors. And. I wanted to point out the new threat intelligence connector. That's. This guy here. And. As I mentioned this enables you to configure. Your taxi server, to. Send indicators, in the 62o, format, into Azure Sentinel, once, you get your threat intelligence and you can use it to. Do detections to match that up against your event data you, can integrate it into your hunting queries and that sort of thing so we'll look at some examples of how you can leverage that earlier, and so. You can connect and easily configure all of your taxi. Connections, here in the new taxi data. Connector, and. Then. Finally, I wanted to click in and show you a workbook. What. I think is kind of good the Microsoft, cloud app security has. An interesting view so if we click over already. Got this loaded here for us. So. Here we can see lots of different ways to sort of visualize the data right we can see the. Latest. Discovery. Alerts we can see different, alerts from the Microsoft, cloud apps security.
Solution By alert. Name we get metrics, views one. Just kind of quick thing I wanted to show you that I thought sort, of demonstrated, the ability to easily do this filtering is here, we see, users. Sorted. By the volume, of. Downloads. That they're doing so, certainly it looks like Megan has. A significant. Amount of downloads. Certainly more than than, her peers and so, we can click on her in the in the graph or, in the chart I should say. And. You didn't see because my screen is kind of blown up but the rest of the of the workbook sort of pivoted to show me specific, information about, Megan's. Activities. As, opposed to early we're kind of looking across all of our customers. So. Just one really really simple example again, I encourage you to check out the, blog that talks about mapping. There's, some really cool things that you can do, with. Map visualizations, here as well. And. The. Final thing I wanted to show you is once, you've got all of this data, flowing into Azure Sentinel it's all there for you to query using. Kql, and so, we'll just take, a quick look at that we. Can see all of the data tables, that are available. We. Can see our common security log, for example, Security Alert data that's flowing in. I'm. Going to run a very very simple saved query here just to give you a quick idea of what that looks like. Just, gonna look at sign-in logs. So. Very very quickly it's it's returning a set of results to me and I can see this in the table format and I can click into view additional information, a. Little. Bigger for you additional. Information there, what I thought was interesting is if I pivot to look at the chart view smart. Diagnostics. Has identified, an, anomaly, for me so, just, by clicking in here I get the benefit of I, mean yes I can look at it and sort of see that something unique is going on but. If I click in even further I get a detailed, information, about the. Specific patterns, that. Are that are unique here I. Tried. To make this big so you could see it but it's not not. Great from a visualizations, perspective. Okay so. So. I can see you. Know kind of specifically, where we've, got a deviation from the pattern and I can run to get additional information and, then I can see the actual results again back here in my table view.
So. I mentioned earlier the ability to do hunting and one of the things that you can leverage to help you with hunting an investigation, is bookmarks, so when you find an interesting or a notable event you, can add it as a hunting bookmark. So. You can sort of save this event for. Later, investigation. And I'll show you some things that you can do with it here in a few minutes. So. You can very, very quickly search over all of this data using. Kql, you. Can bookmark interesting. Things. Once. All of that data is flowing through. Okay. First prize opportunity. There. Is a $50. Microsoft. Store, gift. Card on the line one. Disclaimer and most. Of our government. Attendees are not able to accept gifts so if. That is you my. Desk that you please. Decline. But. I would love to hear if anyone knows step up to their several mics around feel free to pop up to a mic and let me know if you know the answer to this what data can you ingest an azure sentinel at no, cost to 65. Office. 365, activity, logs your winner step, back escameca, the end of the presentation, and we will give. You your your, gift card and thank, you sir there'll be many other opportunities throughout, so we'll hope to catch you on the next one so, yes as your activity, logs office, 365, activity, logs and alerts, from Microsoft drop protection are available, in Azure, sentinel at no cost so you have no reason not to stand up Sentinel instance and connect this data to get that instant value that we just talked about so. Moving, on to analytics. So. We've got our data flying flowing, through we, got some instant, insights from our workbooks, and, now we want we. Want to do something more, meaningful we want to get some detections, operating. On top of this data and you do that in analytics, so, again. Here there are hundreds of built-in analytics rules, that you can choose from you, can also customize and, create your own rules, using kql, queries and there's a nice little wizard process, that we'll look at here in a minute that could have steps you through that experience so these. Can be kind of simple rule, based analytics. But they can also be much more complex, you, can do correlation, of your event data and there are dozens of, built-in rules that will help you to correlate, your event data with the threat intelligence so, again you can now get all of that threat intelligence data into Azure sentinel and out of the box they're a set of detection rules that you can run on top of that so, if there's network traffic going, to or from an IP address that is part of your threat intelligence and, data you. Can you can use that to fire a detection, and, then. Also this week we announced a new opportunity. To, do matching of your of data with Microsoft, threat intelligence we're. Starting with a scenario. That enables you to match URL, data with. Network. Event data and. Again that's kind of leveraging, this vast. Set of intelligence, that we have here at Microsoft we think is part, of the secret sauce that enables, us to protect, ourselves and, help protect you and now you can leverage that for the first time in Azure sentinel as well one. Other thing I wanted to point out because automation, is a theme that sort of is, pervasive, throughout sentinel. Is you, can use these detection x' to automatically, trigger playbooks, so, if a particular kind, of detection fires you may want to automatically, take action, to, remediate or, maybe, to gather additional information that, might be helpful for investigation.
And So you can just have those triggered automatically, based on the detections and we'll look at again how you kind of build those. One. Of the kinds, of detections and they're available in Azure sentinel. Leverage. Ml and. They do that with, the goal of increasing the catch rate without, increasing. The noise so. There are built. In ml. Models, and you can turn these on no experience is required you don't have to know anything about ml, once, your data is flowing through those models, are going to begin to learn and, and. Detect things inside, your environment, and, there's, a couple of these in particular that I wanted to call, out one. That leverages off-the-shelf, machine, learning models for identifying, suspicious, logins, across Microsoft, identity, services, so, we've taken this. This. Model we've used transferred, learning, from. That existing, model to detect an anomalous SSH, access within, your environment so, that's why we're looking at a single source of data. But we're applying, ml. Learning to, detect, real. Threats out of that data, the. Other example that I wanted to highlight is, using, machine learning and to. Do fusion the. Term. We sort of coined to describe this, which, is to take distinct. Data sets and. To. Use. Ml, to fuse, those together in meaningful, ways and you. Can see from the chart on the right hand side here kind of the. Impact. That fusion can have for you so, in this example we started out with literally, billions of different events identity. Based events, office, Asscher events billions, of events and from, that each of these solutions looked, for anomalies, likely. Fired a detection or alert based on that and. That's. Great but we still see millions, of those which are way way way too many for your sock team to to analyze and, respond, to it's definitely these are going in the forty four percent bucket. Right but. We've applied, graph. Powered ml and probabilistic. Probabilistic. Kill. Chain to. Help detect threats so basically we're fusing these together but, we're trying to figure out what is it and what. Are important patterns in terms of ordering, sequencing, right and so, thinking about how these different things relate to the kill chain and fusing, them together based on that. Machine learning, into, a single incident and. Then we will have the ability to bring your own ml models in the near future for those of you who are further along in your ml journey and. With. That we're gonna pop over for a quick demo. All. Right so we're gonna start an analytics, that's where we configure the rules. And. We've. Got many of them already running. Yeah. Bingo okay thank you okay. Back in analytics, we see a list of alert. Rules here that we can enable, and. A. Blown-up. View is squished it everything together a little bit but we, can see that there are different types of rules there are scheduled, rules we'll look at those in a moment there, are some that come out of the box with Microsoft, these enable you to do things like you may want to automatically, promote. All high. Severity detections, from. Microsoft. Defender advanced threat protection for, example in two incidents you can do that there, are fusion, based rules here we just talked about Fusion and its ability to help, you detect. From. Those millions of signals. Real, threats that require a response I, want. To kind. Of a more. Of a straight forward, one here. Just. Show. You how easy it is to, enable these ok so. Here I'm looking at, a. Template. I've already got this in use but because I can constantly. I can create new detection. So I can customize the, query. As. I'm doing that is still exist in my template library there are other kinds of detections, that I can only turn on or off like the ML detections I can't really customize those, detection, so once I've turned that template on it moves out of my template library, and into my active list. So. I mentioned earlier the ability to use, the the wizard and azure Sentinel to create these detections, and. So that starts with very basic information what, is the alert name. Of the alert a short description. All. The detections, can be tagged. According. To the mitre attack, framework, so, you can define one or multiple, stages. Here, you can set the severity turn. It on or off. And. Here. You get into the underlying query that's really powering this detection. And. We can see here that that's looking at threat intelligence data, it's, making sure that that threat intelligence is, recent, it hasn't expired yet that.
It's Active. It's. Looking for only IO, C's that have the entities that we want in this case we're looking for URLs to match against. It's. Joining that with syslog data and it's extracting, out the URL from the syslog message. And. When, it finds a match with the URL. Threat. Intelligence type its generating, an alert so. Want to talk just a moment about this next stage which is mapping those two entities so. Entities, are very important, for investigation, and you'll see that in a minute when we get into the investigation graph, they, enable us to create, relationships. And to link together these. Different alerts and, events that are firing across your organization, so as. Much if, the, data that we're looking at here contains those entities it's really important to map them so. We'll see here that for example I don't have the URL. In 2d maps it's a brand new entity, we just launched, but. I'm gonna do that here. And. I'll show you the power of that in a moment some. Other things we can do or service. Determine. If frequency by which we want this to run we. Can set a threshold we only want this alert, to fire if we've got multiple instances, that are batching that sort of thing and, here's. What we can tie a, playbook. To that so. Here we're looking for Ti that matches, malicious. URL data that we have in our threat intelligence datastore, and so, maybe we want to run a playbook, that's. Gonna block that IP address if an alert fires. Your. Block the URL so I can choose this block URL playbook as, part of my. Analytics. Process. It's, gonna automatically, validate, that my. Query is valid, and and then, I can go ahead and create that so. Then as matches. Occur, I will. See those represented. As incidents, which, we'll look at here, in a moment. And. Time, for another prize. Who. Could tell me the what the Microsoft, threat intelligence center names, activity, groups after. This. One's a hard one and I was going to give you a clue when we were looking at analytics but I forgot. Anyone. Gonna give me a guess. Any, guess gets you a gift card step on up to the mic. Over. Here, elem. Know okay, what, inch elements. You are correct, very good elements, of the periodic table are. Used to name activity, groups and. A recent blog post highlighted, activity, by phosphorus, to target users that relate to the u.s. presidential campaign, what I forgot to show you though was, that the. Microsoft strata intelligence, team contributed. Analytics. Rules to, Sentinel and so we all we have rules baked into Sentinel, now to detect for, phosphorus. Activity, so, they, take the learning that, they got and they build that into Azure, Sentinel, to benefit you. Okay. Moving on to hunting so. I, mentioned earlier that that. You can also hunt over this data and we built a guided, experience to help you through that process and. So there. Is a the, ability to run, these built-in threat hunting queries, and again, you can do that without any prior knowledge now of course you can customize these queries, as well you can create your own using, kql, so, it has all the extensibility, you want but you can just run them out of the box again, these things were developed, by our Microsoft, security, experts and contributed, by. Community, members. And. They help you to identify, suspicious. Activities. Over. You know by by sort of querying over this massive amount of data that you have and when you find interesting things, you can integrate them into. Your investigation. Experiences. I'll show you that in a minute I, also. Mentioned bookmarks. Live stream so let's. Say you're hunting you run a query you find something interesting and, you want to flag it for.
Later. You. Can do that by creating a bookmark, from, that event and then you can take that bookmark, and use it to start an incident, investigation. So you can create a new incident, based on this interesting, or suspect, event that you uncovered, or, you can add it to an existing investigation. So, what starts first, detection. And then investigation, or inserting, a detection and then hunting or hunting. And then an investigate, it's all kind of woven together and the two things work nicely together so regardless of where you're starting your experience, from, investigating. An incident or from hunting, directly, over data the two things can be wedged together. And. Then we also have the ANU ability to monitor a live stream of new threat related, activity, so you need to find a query and anytime new matches, are found for the query you can see those available in a live stream so if you've got something in particular that you want to keep an eye on live. Stream is a way to do that. And. Then. Jupiter notebook so I mentioned these earlier so. Jupiter. Notebooks, can now be launched directly from Azure Sentinel, that's relatively, new and they make it easy to that, makes it easy to create and execute, Jupiter, notebooks to analyze your data so. Notebooks, Jupiter, notebooks combined live data and graphics, and visualizations. And, text which, should make them a pretty valuable tool for a lot of threat. Hunters so, you can choose from a gallery of built-in notebooks, again, developed, by Microsoft. Security experts and community members. Or. You can import others from github to get started these. Are really professional strength hunting solutions, and we use them ourselves, within. Our own threat, hunting teams. Time. For another quick. Quick. Demo. Don't. Look up that question while I'm demoing here. It's. Again we're seeing a bit of a mashed up view of this just because I wanted you to be able to maybe see, it from the back of the room but, we've got here when we launched the hunting experience it's that sound of built-in queries that I mentioned earlier and.
You. Can see. What. Data source that's hunting over you can see which tactics. They're. Related to you can, come in here and just run all of the aquarias if you want or we can sis twos to run just a specific query. So. This one is looking for suspicious network, traffic. Patterns. Using. A time, delta, analysis. And so we run that and we see some interesting events, firing. And. I showed you a bit of a preview of this earlier but from here we can add a hunting bookmark. For this and again, we want to as much as possible map, that to related, entities, and so, that we'll get the benefit of those in the investigation, graph later for. Dozens, of time I'm just gonna go ahead and click Save on this and move on so, now, that that bookmark is saved for, me I. Can. Take action on it so I can create a new incident on that and begin further investigation. I can add it to an existing incident. As well. Okay. Where. Can you find and, share hunting, queries for Azure Sentinel there's someone in the back of the room earlier if, you, know the answer I'm happy does don't. Ignore you over there okay. Github. Github, is the answer you are correct, hundreds. Of contributions, including, data connectors, workbooks, analytics, rules queries, parsers, functions, all of this are. Available on, our github repo, and we strongly encourage you to share your expertise. And knowledge by contributing there as well. Incidents. So. I talked earlier we did it again. Okay. So. We talked earlier about and, detections. Detections. Either a single detection, or multiple detections can be fused together into incidents. And. From the incident we can begin an investigation experience. So. I mentioned earlier the ability to do this in a graph and that's what we're looking at here so, we've got an anonymous login, attempt and we see a couple of related entities, a user who. Was the one that the user account that signed in and the machine that they were signing into and. So we can begin our investigation for. Looking for additional information are there any other, alerts firing, related. To this machine and in fact we see that there there are and we, can click in on those to learn more. Here. We can see that there was a connection, to a malicious URL. Looks. Like we also see a suspicious powershell. I'm. Going to go back to this suspicious. URL, and to do. Yeah. I'm. Gonna birdie I want to view related entities. What's. Interesting here is we talked about earlier that new URL, entity, and we see that this particular alert, is mapped to a URL entity, and when we click in on that URL we, see the results, of automated. Built-in, detonation. So, when you create an, analytic. Rule that, maps to a URL as your.
Sentinel Will automatically, detonate that URL and share. The results with you here this, is incredibly, powerful so, here we can see. We. Can see the destination, URL. Looks. A bit suspect. And. We. Can see this is actually the URL that showed up in the alert. But. This is where it took us and. This. Is what that looked like. So. Very very quickly we know that, this is a malicious URL, and we can take action. We. Can also trigger automated, playbooks from the same experience. Running. A little bit tight on time so I'm not going to show you that but similar. Kind of experience that we saw earlier we can click in view. Our list of playbooks, and sort of go from there and. We're actually going to have, it over and talk about those here next. But. Before we do that we have another. And this is our big grand finale hundred. Dollar prize here. There's. A big hint in what we just looked at so hopefully someone will get this defenders think in and, attackers. Think in. Lists. And graphs yes, who was that yes, that is correct. Infamous, John Lambert of the Microsoft. Security. And to the, Microsoft threat intelligence center, said. That defenders think unless an attackers, think in graphs and that's why we built our investigation, experience, around graphs. Automation. Is the last piece of the puzzle we've talked a fair amount about that already. I'm. Incapable, of clicking the right screen button today. Okay. I'm. Automation. And orchestration done, using integrated Azure logic, apps hopefully. You guys are familiar with those, with. A sure logic apps they're, pretty cool and they enabled you to create, these orchestrated. Play, Books that, can execute a series of steps there, are 200, connectors, that are available for a wide variety of third. Parties Microsoft. And third-party solutions, they, believe to build out these these automated workflows, there, are samples. Available in our github that you, can use to quickly create, your, own playbooks and, as. We mentioned earlier you can trigger those from an alert or an, investigation. And. I just want to encourage you to think about automation, and Play Books a bit more broadly than just remediation. I mentioned that earlier but, we're seeing lots of different use cases for play books and that starts with and starts, with incident management, so. The ability to assign an incident to an analyst to open a ticket and ServiceNow or JIRA, to keep that to incident, on status, and sync to, post it in a teams or a slack Channel, another. Important, area for our automation is enrichment, and investigation. So being able to look up a geo for an IP address for, example or, to trigger an automated. Investigation. And Microsoft Defender ATP, or to send a verification email. To a user so, if you see a suspicious login you can send that you in notification, and say hey was this you and if they say no that wasn't me you can get that assigned, to. An analyst you can reset that user's password, or apply conditional, access and, then. Finally of course remediation. Which is also super important, so you can do things like blocking an IP address maybe. In your on-prem, firewall, and. In. Your endpoints, using the, graph security API. Triggering. Conditional access isolating. A means machine those sorts of things.
And. Since. We saw that earlier not gonna spend very much time on, the demo. 45. Minutes is just not much time and. I hit the wrong button again. Okay. So, it's just a quick, quick view of a play but for those of you who haven't seen it before so, again it's going to orchestrate, a series of steps that's, gonna start with an azure sentinel trigger in this case based I'm gonna lurk and you can see how the sequence sort of flows you can open an incident and ServiceNow you can, post in a. Team's. Channel here's the Notah for the approval email that you can send to the user so, you can see that that can be populated, with different details, pulled. From the azure Sentinel alert. You. Can in apply conditions, so if that user says in that email yes it was me you can decide to take different action based on that if, it was if. It was not to them you, could block. That user in Active Directory. If, it was them you could just close the incident out nothing, nothing more to do there. Lots. Of powerful capabilities, and Azure logic, apps and they're built in to, Azure sentinel. So. We need you to give you just a quick glimpse of the roadmap as we get ready to close we have delivered, a ton of stuff, since. We launched public, preview at RSA, last year lots, and lots and lots of new connectors. Lots. Of new detections the. Investigation, graph and entities we're constantly adding more entities, workbooks. Which. Provide a much richer set of dashboarding. And visualization capabilities. And much. Much more you can sort of read down the list you might be asking what's coming next, and that is more. Data connectors, with. More Microsoft services more third-party. Security technologies. Logs. -. More. Built-in detections both, rule-based and m/l you'll continue, to see innovation there just like when Mystik detected. You know activity, for the phosphorus group they you, know instantly built into as your sentinel new rules to help address that threat so you can just expect that to continue to happen on an ongoing basis, I mentioned. The first use. Cases, for leveraging, Microsoft, threat intelligence inside, of Sentinel, and you'll see more scenarios, around that light up the, ability to bring your own ml models. We're. Gonna support much much richer level. Of threat intelligence data, the full sticks object, more, user entities, and much, much more so. Lots of stuff coming. Down the pipe. Finally. I'm going to encourage you to check out some of the other Azure Sentinel, sessions we didn't go very deep today and to Jupiter notebooks in particular, and we have some really smart people here, from. Our mystic team that are doing sessions we have some partners that are they're, really invested here as well so I wanted to call out the threat hunting sessions, that leverage stupider notebooks and then the other one if you're interested, in learning more about Sentinel, that I'd just strongly strongly encourage you to attend is Nicholas, this session on Thursday. They get to instant value from your sim and he. Has been working with many many, customers, on real deployments, and I think has some really valuable real-world. Advice, that. You can apply to. Your own as your Sentinel deployment so encourage. You if there's interest in either of those two invest, some time in that. Lots. Of resources to help you get started and, I'll. Leave you with the evaluation slide, in just a couple of words, which. Is to say thank you so much for investing, your time here again the level of energy and enthusiasm around. Azure Sentinel has just been overwhelming. And we're. Really excited about where this is going and hope to continue that journey together thank, you so much.
2020-01-25