ISART Day 1 Part 1
Good morning from Colorado and welcome to ISART 2020. My name is Rebecca Dorch. I serve as the Senior Spectrum Policy Analyst at the Institute for Telecommunication Sciences (ITS), the research laboratory for the National Telecommunications and Information Administration (NTIA). I've been involved with this NTIA program, the International Symposium on Advanced Radio Technologies (ISART), since I joined ITS in 2016. As is a tradition with ISART, we open with a tutorial. The topic ISART is tackling this year -- 5G spectrum and a zero trust network --
involves a tremendous amount of cross-disciplinary understanding. So, to help set a baseline of common understanding for those joining us from different disciplines, areas of expertise, and levels of knowledge, we asked our tutorial panelists to do the impossible: explain what 5G is from an engineering, architecture, standards, spectrum, and international perspective in under two hours, and then to record those presentations so that registrants could view them in advance. On behalf of NTIA and our ISART co-hosts, the National Institute for Standards and Technology and the University of Colorado at Boulder, I want to express my sincere appreciation for the outstanding presentations we are about to see. They each did a phenomenal job providing the baseline we sought. I will briefly introduce each of our five distinguished and accomplished speakers prior to showing their presentations and additional information about all of the speakers is in the ISART program and the ISART app. At the conclusion of the four presentations, we will all be here live and in person -- virtually of course -- and please feel free to ask questions online during the presentations and to vote for questions that you, too, would like to have answered during the Q&A portion of the tutorial.
Now remember of course that our panelists from government agencies are speaking based upon their knowledge and expertise and not on behalf of their respective agencies. So, first up we'll learn about engineering and architecture and underlying 5G from Professor Jeff Reed and Professor Nishith Tripathi. Professor Reed is a founder of Wireless at Virginia Tech and has a distinguished career teaching, advising, and directing programs and initiatives, and establishing companies related to wireless security and technology. Professor Nishith Tripathi is an adjunct faculty member at Virginia Tech and a research and development strategist at Samsung Research International, excuse me, Samsung Research America. He and Professor Reed co-authored a multimedia book on 5G which explains the vast potential of 5G and P5G concepts in about 55 hours, and I've asked them to cover it in about 20 minutes each.
So we're grateful to both of them for sharing their knowledge with us. So now, without further ado, we will see the very first video: 5G Fundamentals and Deployment Considerations. Hello and welcome to our tutorial: 5G Fundamentals and Deployment Considerations. My name is Professor Jeffrey Reed, and my colleague Professor Nishith Tripathi, will be presenting this tutorial. It's based upon
our ebook: 5G Cellular Communications Journey and Destination, and you can find it at the link below. First, let me tell you a few things about myself. I'm the Willis G. Worcester Professor of Electrical and Computer Engineering at Virginia Tech. I have founded a number of different organizations, such as Wireless at Virginia Tech, The Ted and Karyn Hume Center for National Security and Technology, several companies: Cognitive Radio Technologies, Federated Wireless, and PFP Cyber Security.
I've also co-authored several books, most of those books with Professor Tripathi. I'm also a winner of the International Achievement Award by the Wireless Innovations Forum. Hello, I am Nishith. I work for Samsung and Virginia Tech with Dr. Reed. I have co-authored a couple of books, including the first multimedia book on 5G, and a textbook on cellular communications.
I have contributed to organizations such as the FCC, GSMA, Scientific American, and CTIA. Let's talk about the goals of this tutorial. First, we're going to provide examples of services that 5G was targeted to support. Next, we will look at the performance goals for 5G in terms of data rates and latency, and we'll look at the construction of the overall system architecture. There's some very important features of the architecture, including network slicing, a service-based architecture, and multi-edge computing. We'll summarize the key characteristics of new radio error interface. This is the air link between
the handset and the base station. And we're going to talk about two important features of the architecture: standalone and non-standalone modes for 5G. And this is important particularly as we discuss the spectrum aspects of 5G. So first topic: let's talk about 5G fundamentals, the services that are targeted by 5G, and their respective performance goals. Let's give some context to 5G and let's take a look at the evolution of 5G. It seems like every 10 years we have a new wireless standard. These standards come from the 3GPP organization. 4G was defined in 2008, and 5G began its definition in 2018, with the release 15. Phase 2 of 5G is release 16, and that's expected to occur in July of 2020.
So what can 5G do for us? Oftentimes, you'll see 5G represented by this triangle in which we have three pivotal services: enhanced mobile broadband, ultra reliable and low latency communications, and massive machine type communications. These services allow for various applications. For instance, with enhanced mobile broadband we see gigabytes in a second, and with ultra reliable low latency we see applications such as self-driving cars, and mass and machine type communications is there to support smart city. We will be seeing the combination of these services supporting other applications such as enhanced 3D videos or our augmented reality or industrial automation, combinations of properties of massive machine type communications and ultra reliable low latency are useful for mission critical applications. And then finally, the combination of enhanced mobile broadband
with mass and machine type communications is very useful for smart home and building applications. Let's take a look at the performance of 4G vs. 5G. IMT 2020 specified the recommendations for 5G while IMT Advanced specified the recommendations for 4G. And as you can see from this diagram, 5G provides much more performance than 4G systems in many critical areas. Peak data rates of up to 20 gigabits per second, user experience data rates of 10 times the previous ones, spectral efficiencies 3 times, user mobility, much faster speeds to support things such as high speed trains, very low latency. And this I think is perhaps one of the most important
properties of 5G, this low latency, because it opens up a variety of new applications, connection densities, at an incredible amount of 100,000 devices in a square kilometer, energy efficiency of 10 times the previous, and finally the overall capacity a 100 times greater with 5G versus 4G. So how do we build 5G? Well, it's composed of a number of new components, such as new radio, new network architectures, virtualization technologies, new devices, and new applications that are supported by 5G. Let's start with the system architecture. We should get ourselves familiar with some definitions. The user equipment (UE) communicates with the access network, which could be a 5G access network, so called next generation radio access network, or a non 3GPP access network.
Then, we have 5GC or 5G core network, also called next generation core (NGC). NGC interfaces with the outside world, and some data networks such as the internet. When we combine the UE 5G access network and the 5G code network, what do we get? A 5G system. A network function (NF), is some 3GPP defined or 3GPP adopted processing function in the network. For example, the base station GNB is a network function.
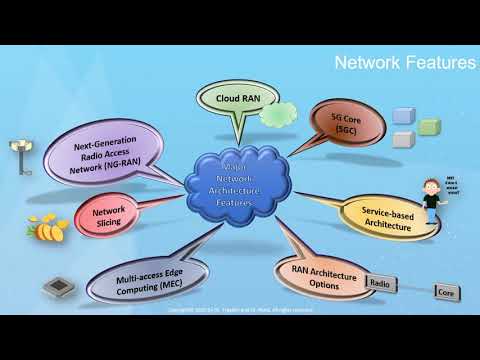
Let's talk about the major features in the 5G network. First, we have NG-RAN, the next generation radio access network that allows LTE and 5G new radio to work together. Then, there's the cloud ran aspects of 5G. The radio axis network can reside in the cloud. 5G has a new core network: 5GC. Sometimes, it goes by other names as well. That 5G core is a service-based architecture, in which the components of the core network can reside at different locations within the cloud. There's a number of different radio access network architectures, combination of 5G base stations, 4G base stations, 5G cores, 4G core. The multiple access re-edge computing network or MEC allows for
applications to reside near the edge of the network. This is one of the the neat features of 5G that allows for very low latency. And finally, perhaps one of the most significant aspects of 5G is that it was developed with network slicing in mind, so you can share a physical network but the networks can be separated under different slices. Each one of those slices provision for a different quality of service experience, or different authentication, or different security. The next generation radio access network is NG-RAN. So what do we have in the NG-RAN?
So we have 5G base stations, gNB next generation node b. So the gNB communicates with the user equipment through the new radio or NR air interface. Also, we can have some LTE base stations that have been upgraded to understand the 5G core network, so we call them ng-eNB. So
these eNBs talk to the UE using the LTE air interface. Now the standard allows the gNB to be decomposed or desegregated into two components: central unit (CU), and distributed unit (DU). So central unit allows pulling of resources, and distributed unit is closer to the cell side so it has the RF equipment. Now, what are the key benefits we can get from engineering? Well, we can benefit from high performance 5G NR air interface, we get quite a bit of flexibility in deployment, and we get cost savings when we do such disaggregation of the gNB.
5G core: so we have a variety of network functions in the 5GC. Here, we will take a look at some of those. We have access and mobility management function that exchanges non-access stratum, NAS Signaling with user equipment for example messages related to authentication. We have session management function that allocates an IP address to the UE. UPF user
plane function is a gateway to the outside world. So, the packets from the outside world, a web server, will pass through the internet routers, will arrive at the UPF, UPF to the gNB, and gNB to the UE. The important aspect is that we have modularization, so we have more than a dozen different network functions.
This architecture gives us benefits, such as scalability, flexibility of supporting network slicing, a variety of services some we may not even know today, and it gives us cost savings. One of the key features of the 5G is SBA (service based architecture). So, each network function provides a set of services. For example, AMF says that, okay I provide certain services. It will let the network repository function about that, and session management function will also contact NRF, so now NRF knows that we have this AMF alive, this SMF alive. So if somebody is looking for an AMF, they can talk to the NRF.
These kind of network functions can store data in some storage functions such as UDR and UDSF. So, they can store information as well as retrieve information. For example, information about the subscriber. What are the benefits we get from SBA? Well, it facilitates implementation. There is increased resilience, because you can have the data separated from the computing resource. So, if we lose computing resources, we still have the data intact. We can start another processor, as the AMF.
Another aspect of 5G is MEC (multi-access edge computing or edge computing). So, the idea is to bring the processing closer to where the users are. So, if we look at traditional processing, then the user traffic will go from application server through the internet routers core network radio network, and to the UE. So, this core network is highly centralized.
Now when we go to MEC processing, we bring the application close to the user, so the packet from the application server will arrive at the mobile edge host, and then we place some gateway, like UPF we talked about user plane function, and from that gateway to the radio network our gNB and gNB to the UE. So, we are not passing through a big comprehensive core network, so that will give us several benefits. For example, we will be able to reduce the latency, because now the server is close to the user. There will be less traffic in the backhaul and core networks, and we can make use of some things we couldn't do earlier.
For example, location hour and renault services, because this application server is closer to the radio network and it can talk to the coordinate the radio network and exchange some information. Network slicing: another very important feature in 5G. So, the basic idea is to provide custom quality of service for a variety of services, as well as customers, so we create different logical networks by using the same physical infrastructure.
So for example, in the standard, we have enhanced mobile broadband slice, so that has data rates with much more importance. So, we provide high data rates to the user. Then, we have ultra reliable low latency communication slice. So here, latency is very very important. Then, we have yet another slice massive machine type communication. Here, our coverage is very important. Maybe there is a vending machine in the basement of a building, so coverage is important. So, basically, we have different slices to take care of different types of services. So, we get several benefits like custom quality of service, and cost savings, so we use only those functions that are required.
We can rapidly deploy services, because we have done the customization. Now, let's take a look at the fundamentals of the new radio error interface. Let's take a look at creating the new radio error interface. First of all, 5G was developed with the ability to support a variety of spectrum shared, licensed, or unlicensed spectrum. It has the capability of supporting massive
MIMO, particularly at higher frequencies to improve the throughput and range of the system. That's a very flexible framing structure. One thing you have to say about 5G is it's the ultimate and flexibility, and it means that actually a lot of flexibility in the formation of the OFDM signal, as well, such as spacing of the subcarriers. There are advanced coding techniques that are incorporated in the air interface, and have the ability to connect to multiple radio access systems. Massive MIMO is one of the key features of the 5G physical layer. You can have hundreds of antenna elements at the base station to enhance the overall performance.
These antennas, when combined properly, provide for high gain and neural beams. They can be used to support multiple users by pointing to different users in space to separate those users, and increase the overall capacity of the network, or you can use spatial multiplexing in order to improve the overall throughput rate by using different propagation paths to convey the information. So, you get high throughput and high capacity using MIMO antennas. 5G has quite a flexible frame structure, so we have a self-contained slot where the resource allocation data transmission and even positive or negative acknowledgement can all occur in the same slot. Now the slot itself is of variable length, so we can have a longer slot or a shorter one, and that will help us adapt to the quality of service requirements.
We not only have backward compatibility but forward compatibility as well, so we have traditional 1 millisecond subframe in LTE. In 5G, that subframe has one or more slots. So, some slot could be used in future to define a new kind of air interface. We have quite flexible OFDM numerologies.
What is a numerology? It is basically a configuration with a certain subcarrier spacing. So, for example, if you look at LTE, we have 15 kilohertz spacing for a typical channel, so between two subcarriers rock solid fixed 15 kilohertz. But, now in 5G, it could be 15 times 230 could be 60, 120, and so on, so we have more options in 5G. So, that allows us to have a low complexity processor, even though we might have large channel bandwidths. It helps us meet qualitative service requirements,
and it facilitates diverse deployments. So, we can have low band, high band, and still have reasonable processing complexity. Channel coding is quite advanced in 5G. So, for example traditionally in LTE when we want to convey resource allocation for that signaling, we use convolutional coding. But, in 5G we use polar coding. So, that will give us benefits, like better error protection,
more efficient to decode. When we talk about data transmission in LTE we use a turbo code. But now we have low density parity check coding, so that has the benefits such as higher throughput, the complexity is relatively lower, and we save some power. Okay. Time to talk about some 5G deployment considerations. So Dr. Reed, let's start with network architectures. 5G has a number of candidate architectures, combinations of base stations, and core networks.
The most popular, eventually, will be option 2. We call it the standalone option with new radio, mixed with the next generation core. Option 3 is what we're seeing deployed today. Primarily the non-standalone option in which we take new radio, and we use the old core network with it. But, there are various options, some with different types of base stations mixed with next generation cores, or with the old 4G core.
And of course, there's option 1. E-UTRA with an EPC. The most common option will be the standalone architecture, option 2, that consists of the new radio connected with next generation core network. That next generation core network will connect to the 5G base station, the G node B, both with the user plane and the control plane, and of course the information will be relayed from the next generation core through the 5G base station, the G node B, to the user equipment.
It is this architecture that allows us to realize the full potential of 5G. However, it requires a new core network, as well as a new radio network. It's, this is more of the later deployments of 5G. Option 3x, quite popular, also called non-standalone NR with EPC or EN-DC E-ULTRA dual connectivity. So, basically our UE can have connectivity with both LTE eNB and 5G gNB. So, one of the things that we can do with option 3x is that data can come from core network to the 5G gNB. From 5G gNB, some data can directly go to the UE over NR interface, and some data can be forwarded to LT base station, and we use LTE air interface.
So, that is the kind of flexibility we have. So, both the base stations LTE and 5G have signaling connection, as well as traffic connection between them. LTE is the master node, because the NAS signaling passes through the LTE base station. So, the
benefits here include faster time to market, and you can still get pretty good performance from NR air interface, and we have overall coverage that is reasonably good due to widely deployed LTE. Network functions virtualization is important. So, we basically go away from physical network functions, where we have individual boxes doing the functions. They are purpose built, proprietary hardware, proprietary software, and tightly coupled hardware software. But, when we virtualize it, then we do the software implementation on generic hardware. So, for example, we can put the AMF software on some generic processor. It becomes AMF, so we can use generic hardware, often called COTS (commercial off-the-shelf) hardware.
This gives us independence of software and hardware, and the software runs on the cloud infrastructure resources, and we make use of compute storage and networking resources of the cloud infrastructure. We get the benefits like cost savings, scalability, and agility. Software defined networking is also important for deployments. So, the basic idea is that we try to rely more on software to connect different nodes or network functions. So, traditionally,
what happens is that we have an IP router, that has the functions like routing table creation, packet forwarding, and now instead of doing all these functions in the same network element, what we do is we divide the control plane and data plane. So, it is like dividing and conquering. So, control plane would centralize the intelligence to determine optimal paths, effectively routing tables, in the data plane (very simple), it simply forwards the packets. So, we separated the signaling from traffic, so now we can use very simple SDN switches or networking devices. So, what are the benefits? Well, since we have centralized the intelligence, then we can make better decisions, because we know what is happening in different parts of the network.
We minimize the manual configurations of routers, and of course we reduce the cost, because data plane devices are very simple. Spectrum, very important for 5G, so in phase 1 we have frequency range 1 that is below 6 or 7 gigahertz, and we have defined FR2 to cover approximately 24 to 53 gigahertz. In general, millimeter wave means we should have 30 gigahertz or more frequency. Right? But, in practice even if it's 24 gigahertz, we say it is millimeter wave spectrum. So, if you look at license spectrum, could be below 1 gigahertz. For example, operators have
600 megahertz deployment. Then, we have 1 to 6 gigahertz, that is mid band kind of spectrum, and then we have millimeter wave spectrum above 6 gigahertz, a variety of frequency pens. So, there are several benefits and challenges. If you have lower frequencies, we get better coverage, but channels are narrower, so throughput is low. If your millimeter will spectrum, you have so
much spectrum that your throughput is high, but because of large apartments, coverage is smaller. So, let's summarize what we've learned. 5G supports enhanced mobile broadband, ultra reliable low latency communications, and massive machine to machine communications.
5G has much better specs than 4G, and note particularly the latency is much lower than 4G. The 5G next generation RAN includes its base station G node B's, and also the core network is comprised of network functions such as AMF, SMF, and UPF. Network slicing is one of the neat features of 5G, allows custom logical networks to be created to support a variety of quality of service and customer requirements.
The new radio interface includes such features as massive MIMO, different OFDM numerologies, as well as different framing structures for the OFDM, and operates over diverse spectrum, and it has advanced channel coding. The standalone new radio architecture is the ultimate, it works with the 5G core. However, currently we're mostly deploying the non-standalone architecture, in which the new radio needs the old core network, the EPC and it needs a LTE base station to act as the master node. 5G operates over a very large frequency range. While the lower frequencies are used to provide coverage, the higher frequencies such as the millimeter wave range provide a higher throughput.
Mobile edge computing places the application closer to the users, and that's one of the key reasons why we're able to reduce the delays in 5G. The service-based architecture defines interfaces and facilitates a modularization and virtualization of the core network. SDN is very helpful in improving the routing and reducing cost. And finally, network function virtualization enables software implementation of a network function using very generic commercial off-the-shelf hardware. Thank you again Professors Reed and Tripathi for that extremely informative presentation.
Next up is Jeffrey Cichonski, who will provide us with information about 5G standards. Mr. Cichonski is an information technology specialist at the National Institute of Standards and Technology, working in the applied cyber security division of the information technology laboratory. He's an active member of the 3 GPP SA3 working group which he'll explain in his presentation, and he has been engaged in the development of 5G security. So now we will roll the second tutorial video, which is: 5G Standardization, 5G Security Enhancements, and Supporting Infrastructure Security Considerations. Good morning everyone, my name is Jeff Cichonski. I'm a researcher in the information technology lab at NIST, and this morning I'm going to talk a bit about 5G standards. Specifically, 5G security enhancements
that come with the 5G standards, and some of the supporting infrastructure security considerations. I want to say thank you to organizers for including me on this morning's tutorial session. So when we talk about 5G standards and standardization in general, it's important to understand that there's many different standards developing organizations or SDOs.
Many different SDOs are responsible for defining and specifying different pieces of the 5G system. Specific examples are the Internet Engineering Task Force. They define critical internet protocols, like TCP, TLS, things like IPSEC. A lot of their protocols are used heavily in the 5G system. There's ETSI, the European Telecommunications Standards Institute. They do a lot of work in various different technology standards, but specifically virtualization is very important, and different ICT standards as well.
Then there's the Institute of Electrical and Electronics Engineers (the IEEE), they're really critical. They've defined the 802.11 specification, or otherwise known as Wi-Fi, and they're doing other work related to 5G. But specifically for 5G, the main group that's defining how the 5G system works is the 3rd Generation Partnership Program. They defined 3G, they defined LTE or 4G, they defined the voice over LTE, that LTE brought with it and now they're working on defining 5G. So we're going to dive in a bit about 3GPP, because that's kind of the relevant standard developing organization for 5G, and really the group where the the meat of the 5G system is being defined. So 3GPP is really defined as a global initiative, and they're responsible for
mobile communication specifications, so they call themselves a global initiative because they're made up of partner organizations or regional SDOs. Examples of these SDOs are ETSI in Europe, Arab, and Japan, Addis in North America, and the makeup of all these developing organizations, these standards bodies contribute to the third generation partnership program. So in order to contribute to 3GPP, you have to be a member of one of these regional SDOs. So kind of the really short too long didn't read: 3GPP is writing the technical specification for 5G, they're defining the interoperable interoperable interfaces the protocols, and the security features which we're going to get into a bit more today. And just a little timeline, 3G was defined by 3GPP, and released 3 back in 2000. 4G or LTE defined by 3GPP, and released 8 back in 2009. The first version of 5G, known as 5G non-standalone, was released in 3GPP release 15 in 2017, and a few months ago we finally frozen the 5G phase 2 or release 16 specification.
So, to continue to talk about 3GPP and kind of the organizational structure, it's kind of important to understand they're made up of three overarching groups specifically the radio access network or otherwise known as RAN, the service and systems aspects, commonly referred to as the SA groups and the core networking terminals or referred to as the CT groups. So each of these groups kind of has a plenary group that's oversees the sub-working groups, and they're responsible for setting the priorities the timelines and the coordination that's happening within the within each of these technical working groups. So specifically for the past four years, I have been an active delegate in 3GPPs SA 3 working group, this is the groups responsible for defining the security architecture. When I started attending 3GPP meetings was when 5G security architecture was kind of a blank page, and we were just beginning to lay out how the 5G security architecture was going to work and what security features would be included. A little more to continue on about 3GPP and kind of how the group works. A little more specifics about RAN, they're really responsible for defining all things radio interface: they define the really hard technical aspects of the radio access network, they're responsible for advancing the state of technology, and how we're able to send more bits over the limited spectrum we have available.
The SA groups are really responsible for the overall architecture and services capabilities of the system from requirements to general architecture to kind of specific security architecture. The CT groups are responsible for specifying terminal interfaces kind of the logical and physical interfaces the different terminal capabilities and the core network parts of the 3GPP system. If you look at CT, they're the folks that take the high levels specifications and boil them down into the bits and the bytes and actually standardize what each message and each bit needs to look like. Another important component of 3GPP is they work using a three-stage methodology, and that's applied in within the working groups as follows kind of stage one overall service description from the user standpoint really high level coming up with requirements and what are some of the services that the the new release of 3GPP system should have included. Stage 2 is the overall description of the organization of the network functions to map service requirements into network capabilities, so a lot of the architecture stuff is happening in stage 2. In stage 3 a lot of times is where a lot of the CT groups comes in and it's the definition of switching and signaling capabilities and needed to support the services defined in stage 1 so really CT is or stage 3 is really writing the hard zeros and ones that go into making the system operate.
So, just some insight into the 3GPP process as I said, I participate in 3GPP SA3. Each working group is a little bit unique so my perspective is kind of an SA3 perspective, but the general approach is you study new features, new capabilities, new things you want to include, and then potentially the next release from a security perspective this could be studying security issues or security features that are seen as important and then kind of the outcome of those studies are made into the technical specifications in the form of normative work which is actually making it into an actual standard. So the TR really from an SA3 perspective the technical report or TR presents the different solutions for a specific problem or capability and a lot of these times we're leveraging protocols and capabilities and technologies from other standards organizations. So as we mentioned, IETF and IEEE 3GPP relies heavily on technologies defined by other standard organizations to make the system work. There are definitely roles and responsibilities for each
of these SDOs, and they try to utilize each other's technologies as much as possible. It's really the work really happens in an iterative pipeline SA3 to find solutions based on SA 1's requirements and SA 2's architecture, and also for mission critical services that are defined by SA6. There's a lot of tight timelines that require the groups to really work in parallel, and sometimes rework is required if an architecture changes from SA2 perspective. That means the security solution for that architecture might also need to change or evolve, and then SA3s security solutions are really made real by CT1 so they write they take the high level security architecture and implement it in the overall system in kind of that really detailed bits and bytes level and then a really important notion for 3GPP is it's a consensus based process. So, the idea is all individual contributing companies bring contributions. Those contributions are discussed at a very technical level. They're argued, they're disagreed with,
they're agreed with, they're promoted, and sometimes they're kind of not looked on with much seriousness if it's not a a real technical solution. So it's really hard to kind of just barge into a 3GPP meeting and try to push your solution to a specific problem, because it needs to be really informed at a technical level, and it needs to make sense within the system. So, these technical discussions resorting to a vote is really rare. It's kind of seen as a failure of the process and voting is from an SA3 perspective Really what I've seen has been reserved for electing the the leaders of the working group. Just a quick splash of the current timeline you can see release 16 has been frozen in June 2020. Release 17 is underway in many of the groups, and release 18 is beginning or already has begun in some of those stage 1 groups.
So we're going to shift a little bit and talk a little bit about network security and just the overall security capabilities that 3GPP and 5G bring to bear in this new generation of cellular network. So just the super basics. We have a device that's connected to a network of base stations that network of base stations or radio access network is then connected to a packet core of some kind and then that packet core provides connectivity out to different IP networks, whether that's the internet or some specific other IP network that needs to be connected up to. So super high level diving in to overlay some security around that. An important component of
3GPP and mobile network security is security is provided but it's provided at a hop by hop level, it's not defined to be end to end. There's no security from the 3GPP system perspective from my device all the way to the internet. The security happens at each hop of the network so from in the radio access network, I have access stratum security there's NDSIP or network domain security used which is a 3GPP term for IPSEC.
NDSIP is used between kind of the radio access network and the core network and then there's also non-access stratum security provided from my device into the core network to protect a lot of the signaling traffic that happens. So just the key point is security is provided. It's provided at a hop by hop layer. This is just a good representation of kind of where security exists. So we have user plane security we have as security or action stratum protecting the control plane from the radio network and we have non-access stratum security that's protecting the signaling of the core network traffic. There's NDSIP or IPSEC and then there's TLS provided at multiple layers of the of the system so to overlay you can see that user plane security and kind of the radio control plane security is terminating through the base station and then we have security protecting core network signaling going from the UE into the the 5G AMF or CF, and then we have NDSIP used to protect different portions of the network as well. TLS is becoming widely used within the different functions of the core network and then over top of all of that from an actual application perspective a lot of our applications and our apps and our organizations we have user plan application layer security that is providing kind of an overall layer of security from end to end taking advantage of all the baked in mobile network security and layering on top of that.
So that was kind of a high level of where security is in mobile networks that that relevant for LTE it's relevant now moving forward for 5G. So as the standards were defined there's definitely some known security issues with LTE. The technologies have been around for 10 years. It's not perfect. Just some inherent ways in the way the network was designed allowed potential attackers to do some subscriber tracking based on information that was sent over the air in the clear. An LTE based on the the key hierarchy there there was no possibility of user plane integrity protection so no way to protect user plane traffic. At that 3GPP system layer there are definitely some roaming issues. I'm sure folks are familiar with SS7 and diameter threats taking advantage of weaknesses in some of those networks and then kind of general false base station threats are definitely a real thing with any kind of RF technology. So moving forward, 5G the goal really was from a standards perspective
to build on the security provided in LTE. LTE had robust security protections just because there was some worse unknown issues doesn't mean it wasn't a robust secure system, but the engineers that were defining the the 5G security architecture in 3GBP understood some of those security weaknesses, and really aim to improve 5G security. So we like to say 5G security is really an evolution of LCE security. It's not a revolution. It's building upon some of the good stuff that was already there so some of those specific features that we have. Our user plane
traffic integrity protection as I mentioned that didn't exist in LCE it's now possible 5g there's some subscriber privacy features to prevent some of those subscriber tracking threats there's a notion of a security edge protection proxy this network function provides standard standardized security at the roaming interface there's a new authentication framework to allow different authentication network methods into the network and there's uh this notion of splitting out the radio unit in this centralized unit and distributed unit so you can put the you can do some security enhancements kind of from an architectural perspective we're going to dive into a bit of these in more detail starting with the radio network security piece so as i mentioned finally we have integrity protection for the user plane all the control plane integrity protection was available since the umts days and then as I mentioned we also have this split out of the gnode b into a central and distributed unit the CU can or centralized unit performs the security critical functions terminating confidentiality and integrity and the air interface security terminates at the CU so that allows you to locate that in a more trusted environment closer to the trusted core network. There's also some language in the specification to provide increased visibility to applications to have a better understanding of what their security connection looks like. This could be really promising moving forward as the 5g system evolves it could allow applications to query the network to understand what their security posture of their current connection is you can picture a banking app if you open it it could hit this the app could hit this api understand its security connection if it didn't meet the requirements for whatever is laid out by that application that application then could initiate some kind of over-the-top application layer security to protect against that kind of weak base station connection so there's some privacy protections within 5g as well kind of the objectives of these were really to protect the permanent identifiers cycle temporary identifiers in a more regularly scheduled way a more standards based way and kind of avoid these re-authentication that posed some threats in previous generations of 3gpp systems so the big thing that comes up when we talk about 5g and 5g security is the encryption of the subscriber identity in 5g that subscriber identity is known as the soupy in lce that subscriber identity was known as the mz and i'm sure folks are familiar with mz catching threats so now the 5g system allows you to send this subscriber identity over the air in a concealed manner so it's no longer sniffable or catchable by rogue base station or just malicious actor there's some 5g authentication framework enhancements as well so the credential storage we have storage and secure hardware whether that's a removable uicc sim card or if it's an embedded element in the device like something commonly referred to as an esim you can have the same authentication method to access both 3gpp and non 3gpp access so picture connection to wi-fi um using a 3gpp kind of security or credential there's also native eep support for 3gpp access so this could allow in the future things like iot devices to take advantage of tls to prevent them from having to have that physical sim card and allow a more scalable deployment of authenticating iot devices on the network. So one critical thing I like to talk about that's really important from a 5g security perspective is the 5g network is really comprised of many components utilizing different modern i.t
technologies. 5g is moving from a legacy kind of network functions as a physical box to a more software eyes cloud native approach to the system the packet core network functions are really being written in a in a cloud native way using things like containers and container orchestrations to to manage and operate how the system works so taking advantage of modern technologies the network functions are really one piece of that 5g system the network functions are going to operate on top of kind of general purpose i.t components things like cloud computing technologies cloud operating systems they're going to utilize virtualization and container orchestration so it's really important that you look kind of below the 3gpp network function perspective and look at that supporting infrastructure and apply and understand what the cybersecurity best practices that can be used for those various different components of the technology stack there's a lot of best practices that exist for these technologies these technologies are widely used in the i.t space so it's really important that you're turning on and enabling the capabilities from a security perspective that exist in that supporting foundational infrastructure layer and just to build on that a little bit there's many different technologies and protocols being used I mentioned cloud computing technologies but it's also important to note that internet security protocols are being widely used as well and these protocols as I mentioned are specified by other standards developing organizations things like ipsec tls josie um many other i.t security protocols are being used in these systems so it's important to understand what the best practices and the best ways to deploy those types of technology are so if you have any questions or comments feel free to reach out to me at my email address here Jeffrey.Cichonski@nist.gov. I really appreciate everyone's time today and I hope you enjoy the rest of the conference.
thank you Jeffrey Cichonski for that very informative overview of the standards process. I'm actually looking forward to asking you some questions during the QA period. We will now learn about spectrum for 5g within the United States from Dr. Monisha Ghosh, the current Chief Technology Officer of the Federal Communications Commission. Dr. Ghosh is also a research professor at the University of Chicago and prior to joining the FCC in January of 2020, Dr. Ghosh served as a program director at the National Science Foundation.
So our third tutorial video is spectrum for next generation wireless 5g and wi-fi. Good morning, everyone. First of all, I'd like to start off by thanking the organizers for providing me the opportunity to spend a few minutes discussing FCC's priorities in allocating spectrum for next generation wireless both 5g and wi-fi. My name is Monisha Ghosh. I'm in a temporary position at the FCC as the chief technology officer. I'm also a research professor
at the University of Chicago where I conduct experiments and research on 5g and wireless. So the topics I'd like to cover in the next few minutes start off with the spectrum landscape for both licensed and unlicensed. As we're all aware both of these parallel technology parts for wireless deployments have been progressing very rapidly over the last few years. Each of
them have designed and specified system designs that are increasingly higher rate lower latency providing better quality of service and in order to do this efficiently both systems need larger and larger spectrum allocations. So we'll talk a little bit about where we think the spectrum can come from. Then I will move into a discussion of the licensed regime talk about spectrum allocations in high mid and low bands. All of these three spectral regions
are very important in order for us to get a complete user experience. I will also talk about unlicensed even though one does not think about unlicensed spectrum as where licensed technologies like the g's 1 through 4 and 5g will be deployed. It is increasingly clear especially as born out by the deployment of lte laa in 5 gigahertz that cellular technologies will take advantage of the unlicensed spectrum to deploy their systems in a way that they can aggregate channel capacity to give a better end user experience. So there are two actions in this area that I would like to talk about. One is a six
gigahertz draft report and order and the second is the repurposing of the 5.9 gigahertz spectrum. No talk on spectrum is complete without this picture which many of you have probably seen in the past. This basically gives you the United States frequency allocations. While this is specific to the U.S. similar charts exist for every country in the world and they're all similarly crowded.
The bottom line is that spectrum is scarce. It is a finite resources and as you can see from all the little colors and the bars on this chart it is pretty much allocated, especially if you look at the regions that have been used the most for consumer communications which is somewhere up until 30 gigahertz. You see your familiar services; there are your AM radio and FM radio and television and then the cellular and wi-fi services. This is not a complete depiction of everything that has been allocated so far but it just gives you a general sense of how little of the spectrum that's out there is actually used for the services that all of us have come to depend on.
The other thing I should point out that a large part of this these spectrum bands are allocated for federal use and those have usually been off limits up until now but increasingly sharing with federal services or finding ways to coexist with them is becoming an important part of the spectrum strategy for not only the FCC but other regulatory bodies around the world. Now as you can see from this picture as you're going from the chart from top to bottom the scale changes it's not a linear scale and so the same area covered by a circle at the bottom of the chart actually encompasses a larger swathe of spectrum. So the 60 gigahertz wi-fi circle is actually 14 gigahertz of spectrum in that little circle there at 60 gigahertz which is more than all of the allocated spectrum saying below three gigahertz obviously. So basically what this tells you is that
if you're looking for more bandwidth more spectrum availability you need to go higher in the spectrum band but at the same time as you go higher you face the problems that physics poses in terms of propagation. The signals don't travel very far and so it has to come with a accompanying change in the way you design your cellular systems or wi-fi systems to operate at these higher frequencies. I'd like to now talk about the FCC 5g fast plan. So this is fast stands for facilitate America's superiority and 5g technology. You can either google their FCC 5g fast plan or if you go to the website there what you will see outlined there is a very comprehensive strategy of how the fcc plans to allocate spectrum in high mid and low bands as well as in the unlicensed band in the service of future 5g and advanced wireless services. In the high band which I denote is greater than 24 gigahertz this is where one expects the 5g millimeter variant to be deployed again because this is much higher in frequency propagation losses.
Propagation inherently limits the distance that you can cover with a single base station. This lends itself to small cell deployments however the bandwidths are much much higher and so you have the potential of actually getting gigabits per second throughput in these frequency ranges. In fact as part of the research that I do at the University of Chicago with my students.
We've been taking a lot of measurements on the Verizon's millimeter wave deployment in Chicago 5g deployment and we have measured download speeds of one to one and a half gigabits per second depending on where we are located. However purely focusing on the high band is not an effective way of rolling out 5g for everybody. The mid band plays a crucial role in in in getting 5g out to everyone. It is a nice balance between coverage and throughput. The frequencies lend themselves to wider deployments and there is enough bandwidth there to get reasonable throughput as well. So it is very very important for any wide-scale mobile wireless system to have mid-band mid-band allocations. I will not
spend a lot of time talking about low band which is less than one gigahertz. This frequency has been mostly allocated for a broadcast television in the past but over time more of it has transitioned over to mobile wireless especially with the transition to digital tv. The spectrum was repacked leading to some auctions of some channels and other channels which have been repurposed for 5g applications. Now do keep in mind that the bandwidths that are available at these low bands are pretty narrow so you're not going to get the height throughput that one expects when one talks about 5g. But on the flip side you will get very wide area coverage and this would be great for the next generation of iot applications for example. For example city scale iot where you need large ranges but your data rates are not that high.
I will also talk about the actions that FCC has taken an unlicensed to enable not only expansion of wi-fi which is the first technology one thinks about when you're thinking about the unlicensed spectrum. But also as we've increasingly seen in five gigahertz unlicensed spectrum is also a great place for cellular systems to deploy as long as they meet the rules of unlicensed spectrum. We've seen deployments in Chicago for example where cellular carriers are aggregating up to three channels in the unlicensed band to enhance the throughput that they deliver to their customers. We fully expect that the new unlicensed spectrum will be used by 5g and r
unlicensed in the same way as well oftentimes in industry you see these two technologies set up in a competitive manner. While it is true that they occupy different spaces we also feel that we need to allocate sufficient spectrum to both because advances in one enable advances in the other. If you're at your home with a very high speed wi-fi connection and you're used to that kind of a user experience you expect the same level of service when you step outside the home where of course wi-fi is not going to provide you that experience but cellular will. So we view both these systems as you know pulling each other up and the consumer benefits and allocating enough spectrum for both is very very important part of the FCC strategy. So let us take a little bit of a deep dive into what FCC has done on the high band. A number of auctions have been completed already. In January 2019 800 megahertz was allocated in 28
gigahertz, 750 megahertz in May of 2019 and 24 gigahertz. And just recently earlier this year 3.54 gigahertz of spectrum was allocated in the upper 37, 39, and 47 gigahertz. Now the earlier spectrum allocated was just last year and we're already seeing 5g rollouts happen in the spectrum. So the industry is just waiting for spectrum to get allocated for them to start rolling out systems. So the total of 4.95 almost five gigahertz of spectrum has
been allocated for millimeter wave based 5g. I believe the U.S. now leads the world in high band licensed allocations and this has resulted in an extremely aggressive rollout of millimeter wave 5g across the U.S. And as I mentioned before this is the band where you're going to get the gigabits of speeds that we have come to expect of 5g.
On the mid band there's a lot of actions that have been done and more that have been planned. The 2.5 gigahertz is actually an interesting band as the single largest continuous blocker spectrum below three gigahertz. It's currently allocated to educational broadcast servers in the broadband radio service. The FCC has an NPRM out to re-evaluate the spectrum and to say
what are the current needs of these two services EBS and BRS. And then any spectrum that is left over there's an anticipated auction that will begin in early next year. Again this is the mid-band spectrum which has the nice characteristics of both propagation and sufficient bandwidth. The c-band report and order which went out earlier this year will result in a public auction of 280 megahertz of spectrum in the 3.7 gigahertz band. So this 3.7 to 3.98 gigahertz is slated to start in December 2020. If you remember the chart that I showed earlier
on where you see how crowded the spectrum is most of the time going forward if we are trying to free up spectrum in the mid band in particular for 5g. We have to look at what's already in there because there really isn't any spectrum that's sitting there either. So in this band in particular you have satellite incumbents which have to be moved out of these 280 megahertz of spectrum. They will continue to operate in the upper 200 megahertz so 4 to 4.2 there will be a 20 megahertz of guard band between the 5g mobile terrestrial and satellite but that takes time. There is also a process by which the satellite incumbents are paid to move out of the spectrum and the money for that comes from the proceeds that the auction will raise.
So licensing spectrum in the mid band is usually a longer process than say the high band where there was a lot more available spectrum. And we're going to see this repeat in other bands that we pick up for 5g as well. CBRS has been in the works for many years now. This is the 3.55 to 3.65 gigahertz band where navy radars operate. The auctions were supposed to have started in June. They slipped by about a month due to Covid but they have begun. This auction will be for the priority access licenses so CBRS is a band which is not only being shared by navy radars through SAS or AFC service but is also going to have three different priority classes of service. So the incumbents, then the priority access license, and then the general access category.
So the licenses being auctioned today are for the priority access licenses. This will probably be in the U.S. the first mid-band 5g rollout that happens and the industry is very excited about it. There are a lot of different use cases being planned for this band. For example, private 5g
networks is one thing that you can see rolling out here and also just early 5g mid-band deployments. We are also investigating potential sharing in the band right below the 3.55. So this is the 3.45 to 3.55 gigahertz, a band which also has a lot of federal use right now. NTIA came up with a report on spectrum sharing earlier this year and we are in the process of refining some of the assumptions and parameters to really understand under what conditions the spectrum can be shared. So there are a lot of actions in mid-band and we hope to be able
to get a fair amount of spectrum into the hands of 5g providers fairly soon. Low band, as I said, I'm not really going to talk a lot about. There is a 600 megahertz band, there's about 70 megahertz of a license spectrum that has been allocated there and in 900 megahertz. There is some discussions about repurposing part of the band to enable broadband using LTE for beginning for start and then possibly 5g into the future.
Finally let me talk about unlicensed. We recently concluded the biggest unlicensed allocation for that is the biggest that has ever been done. It is 1.2 gigahertz of spectrum has been allocated for unlicensed use in the six gigahertz band which is basically 5.925 to 7.125. Now unlike the five gigahertz or at least most of the five gigahertz
this is not a clean band. Again as I mentioned before there's very little clean spectrum left. it will be shared with existing incumbents so there are six gigahertz fixed links and broadcast auxiliary services there which provides services like wireless wireless news gathering. However FCC has been very careful in crafting rules that will permit low power indoor wi-fi devices or unlicensed devices without any automatic frequency control to coexist with these bands.
We have
2022-09-06 23:03


