Hands on Windows Auditing on-Premise and in the Cloud
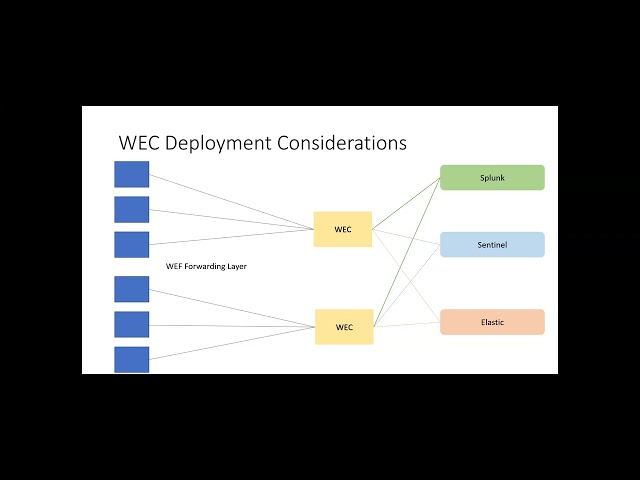
if you're talking larry we can't hear you sorry i was on mute yeah can you see my screen now yes and hear you all right all right all right so um yeah so this is a presentation on windows event logging um a little bit of cloud cloud event monitoring the kind of focus on this is to it's kind of has a windows focus and then the cloud has a bit of an azure focus then it's really it's sort of the way the way you can get up and running when to get your windows logging in order in a scalable way that can actually get get it up and running quickly do really good at log aggregation to um to certain control points and then either you know whatever to and then it's like sim and tooling independent on the analytics side so so so yeah so that's where that's what we're going to do here all right [Music] okay okay you just have to do with the clicker all right so um so for people are not aware um windows actually has a very nice integrated um centralized logging and the reason um i'm taking this approach is because in the past um people have uh you know installed collector agents um log collector agents sim agents you know for splunk elastic or whatever all on like on on each individual end point like you know people aware of this thing called file you know win win file beat all kinds of you know the different force splunk forwarders and you know when if you have thousands of systems getting agents deployed out to those thousand systems is kind of cumbersome difficult to manage um especially when you do updates the introduces also can these these third-party agents can introduce security vulnerabilities to your endpoints um especially on things like domain controllers you don't really want you want is limit limit your you know non-native software on on endpoints like as much as possible so so we're going to talk about uh how how we set this up in a quick and efficient way and then and also in such a way that even if you set it up just to get started on a few endpoints that you can really quickly scale it up um to thousands of endpoints and also manage manage the policies um the law audit policies on these thousands of systems in a in an efficient and an efficient scalable way so that that being said um i'm going to talk a little bit uh this is this presentation i can be focused on like what what exactly you should be uh monitoring um as far as the specific log events that would be another presentation itself this is just a way for you this presentation is more for a way for you to quickly get up and running and also to talk a little bit about what you can do once you're up and running and what options you have in the cloud so but it just just to go over quickly as a kind of a baseline these are these are the must monitor events um so any anything related to security event logs being cleared um any changes to high value groups like domain admins local administrator groups being changed local users being created deleted on member systems and any new services being involved so these these are like must monitor events so keep that in mind as you build out um your logging infrastructure and as as just just some guidance um some of the stuff that in this presentation that references third-party templates and um also some of our expertise in in deploying um working with uh monitor log and point logging systems as well i'll you know i'll talk about references to that um so um so what is this uh what is this that's in in a built-in um log management server in windows it's called the windows event forwarding windows event collector um left leg for short so the forwarding forwarding element of this is uh is sends the forwarder sends logs from windows event viewer so you you you configure the endpoint um and uh um and then use that endpoint one is integrated with a remote collector server uh with using a policy and then it forwards the events whatever events are in that policy configured to the collector and the collector aggregates it aggregates all the data from all the endpoints in it that are sending it logs and then you can either then it's up to you how you want to consume that so this is why this is a great sim agnostic methodology for collecting your logs and managing them um one one note is it does require a win rm to be configured on each endpoint um and so yeah let's just keep that in mind okay so deployment left deployment considerations okay so um with for winrm because you absolutely need that it's enabled on servers 2012 r2 plus and uh and then workstations are not enabled so for for for windows 10 windows 11 endpoints you have to have to enable it but the good thing is um is is we just use group policy to do that and policy is a very very nice way to to handle all this integrates really well with the uh the whole web model um you just you use a create group policy and we'll actually go into the details of product creative school policy so and that's part of what that's part of the hands-on part of this talk so you you take the group policy applied to target endpoints and then um the group policy itself contains the uh address so that knows where to send the log so very nicely you can enroll thousands and thousands of endpoints um into a collection and uh without even having to go and configure and manually configure each endpoint you can manage all the uh all the um the the logs that you're collecting as well from this from this uh um f model so um so how so how does this work so so there's this thing called subscription and this is actually the link between the forwarder and the collector um and what a collector is the wac is this is basically a subscription manager it accepts the events from the endpoint and allows you to specify which event log alerts to collect from endpoints so you actually configure everything um by this group policy and and web infrastructure so you're not there you know on thousands of endpoints like you know trying to figure out to figure stuff out you don't have to install agents on these thousands of end points um it makes it really nice and it doesn't stop you from participating in what you know whatever sim infrastructure you have um regard whether it's cloud-based sim splunk you know it's not not doesn't really matter so subscriptions to find the hosts in the collection group so yeah so basically the subscription um you can find a subscription and um and um in on the whack and it'll it'll set up um basically which which uh uh hosts are allowed to collect and then this is also important for some scalability reasons so you you create subscription and then you enroll the endpoints that are going to come to that particular web in the subscription and then all subscriptions determines um you could configure the the and the the events that are coming from these endpoints through the subscription itself and just to diverge a little bit um another another nice thing about about uh about um this works is not as now you can actually um if the end point if you've distributed cis monitors out to the end points um you can now use the w to collect um um events um and uh from from these endpoints the cis one has its own log each each log type in uh in windows is like a channel so this one has its own own log and uh you can collect that as well so it's very very nice you get the extra granularity and um from sysmond you can also you could by fill by by filtering which we'll get into as well you can actually tune the types of logs that are coming out of each each log type channel on the endpoint so you can get very granular um with this log management scalable and then you can also manage manage it um from a limited set of endpoints and group policy which is actually quite nice so yeah so six months you can add all this extra granular logging um targeted logging and then uh you can manage it all all with the wekweft and then um and then that doesn't doesn't take away from anything else that we've been talking before with splunk with the uh with the you know whatever other uh because you could still he's basically you you could still put we'll have a diagram on this we can still put the heavy forwarder on on the wex and so you can get thousands of end points with with with finely tuned um uh granular logging coming into the wax and then you just if in case of splunk you just put a heavy forwarder on the wax and then boom you got full integrated um sim and logging and without you know having to deal with like you know collecting and managing data from endpoints okay this is a little bit uh just threw it in here this is a little bit for people not aware system on all the extra granularity um that you can get now i'm i mean i know i know you uh we we're talking about a lot about defender um as well um in this in this today and then but but i think cis1 does provide you know targeted act system activity logging and i think i think defender is more looking for malicious activity uh rather than just looking looking at uh everything so um so this is this is for stuff system i could like to find stuff that uh that you know maybe defender missed um so it's a it's a more more comprehensive solution okay so yeah these are just some sysmonkey things i want to include that in so uh so people if people are out out there or actually working on some of this stuff um you know this is not modular is a way you can create a custom system config um we built uh we built some custom system things here at the tech center as well um i really like this one modular because it um it has you can build your own sysmon config file from it very straightforward way but yeah so these are the uh these are the uh the black hills that black hills um one is very nice as well and it's based on sysmon module it gives you a good starting point okay yeah it's just installing sysmon um it's an interestingly enough um so that's the manual way of installing sysmond then we got a gpo way of installing suspended velociraptor which is i talked about in the previously which is a you know an incident response um um forensics tool um which is also well integrated well with sysmon as well okay so this is the workflow so basically uh sysmon if you want to install be there then everything goes to windows event logs and then everything goes to wek wef and then this is what i talked about earlier this is the actual you know reason why this is great architecture because it lets you take the end points on the left and then group those end points um because the wax have have some scalability um concerns so like you know it's like usually the sweet spot is two two to five thousand endpoints per wack um and so you can um yeah so you'd want you want to allocate the different endpoints and then with the uh with the group policy um that's that's that's fairly easily easily done and then the nice thing about this architecture is as well is now now that you've got you know these few of these wax out there you've got pretty much can target the auditing in a very scalable way and then you know depending on what what uh sim you use you just drop the as you can see on the right the doors are the sims and um i thought i'll be talking a little bit about sentinel on towards the end of the presentation but uh but as you can see you can now get all that data a lot of data up into the into the sim um uh and only have to manage a few agents which is quite quite nice okay so yeah as we talked about it when rm has to be present um those are just i just threw up these few there's a powershell command and that's a that's a command line and that'll that'll uh quickly get winrm installed if it's not or tell you if it's installed okay and then this is the group policy object which we'll get into this is the uh basically um basically these are some of the the elements of the policy that needs to be configured so you got you got to make sure that the winrm is is set up and then event forwarding is enabled and these these go these go out to the endpoints that this is the weft layer and then yeah it'll yeah it'll specify the collector location and enablement of the forwarding so this is just a little bit of a summary of what needs to be done and then we'll get into the details of it uh yeah so the whack the whack once you set up a whack um there's a couple you know i've as i said before two two thousand four thousand endpoints per wack um that's just a quick little command to config could set up the wac on it what can be set up on any domain domain joint server so yeah it's just that's all the only requirements is a windows server and then um you can also set it up just by going on in the wac um you're going to event viewer and you click on um subscriptions and event viewer automatically basically asks you to set up the wax so it's pretty pretty straightforward actually oops sorry so yeah so that's good so there it is yeah so this is this is uh i'm in the wac on a windows server in the web and then um you know i go into event viewer on the wax and then i just basically click on subscriptions and boom little window pops up and um you click yes and now you got your web installed so it's very simple well not not too big of a deal and then you configure forwarded events right right yeah so this is configuring forwarded events um you'll want to you'll want to increase the size of the that's the log size i saw basically the log size on the wac and that's kind of the very basic um very small so i would i would i would crank that up to you know maybe a maybe a gig or two yeah depending on your log volume but yeah this is going to be the size of the log file and it's going to it's a it's a it's a rotating log file a little it'll you know once it's full it'll just rewrite to the beginning of the log so it's a rotating log file yeah and then uh okay so there's that um yeah so so this is this is one one um basically so when you're setting up the whack uh you're gonna it needs to be a bunch of commands need to be set set up uh needs to be run on the web the wek endpoints to get it to work uh and then someone needs to be run powershell some need to be run in command.exe this presentation has everything you need to put in there and this is these are the commands that need to go into white power shell and then this is basically the three these three commands need to be run on each whack um the winrm will tell you whether um you know remote manager is installed or not set service setup setup set setting the winrm service on the wacom yeah and then the web util for forwarded events and then this is this is reason these commands uh now if the if the wek is server 2019 or greater than so it gets these commands and this is every this is everything you need to do these commands actually have to be set up on the uh you know the wek to allow the communication from the from the endpoints um so yeah so so this is this is necessary uh and then at the end i'll give you a reference to a video that goes into the hands-on of how to act actually set all this up with with with uh with the dialogue but uh this is this is it for the command so these these need to go on each way and this is command.exe so yeah okay so once once once you've got all that set up and you've got the the wek install let's run all those commands and and then you basically set up a subscription this is a subscription dialogue and which is in on you know in the in the uh in the subscription um section of the uh event viewer on whack and you actually um if you look at this dialogue uh you wanna uh make sure that the uh the uh subscriptions are source computer initiated um yeah you can name it uh not not collector initiated so very important source computer initiated the subscription just whatever it needs to be but yeah so this is the basics of creating a subscription and this is basically the it's going to aggregate like the what law what what endpoints and what logs are going to um are gonna be coming into the uh into the wac now um for uh versus select computers that's where you that's where you uh that's where you uh enroll the computer so basically you click on select computers and then in there you can choose which which endpoints are going to be communicating with this whack and now you can you can also you know you could choose endpoints you could choose groups and then we'll talk a little bit about some scalability you know techniques for grouping grouping computers so that only they only they only connect to certain wax all right so yeah here we go we're adding we're adding end point left end points to the wack that was what i was talking about so this is just uh this is just what you see when you click on that you know adding computers now um to so there's a this is this is a kind of an interesting one so this is a this is a starter event filter so so so this is going to specify for the particular wac it endpoints what it's going to collect from the endpoint and it's a it's an xml file um and then uh yeah and then basically uh here you could tune and you can add you can add channels to the subscription you can you can modify the way the events be collected from each particular channel and i could sure i could show you this we'll break out of here for one sec you can see this real quick here i have it let's click on it here i just wanted to show everyone this hey mirror yes well how much time do i have respond uh you have plenty of time so yeah okay i want to be cognizant over the time okay cool all right so let's take a look at this here all right so this is the this is the filter and this goes into um we'll go into the uh the subscription uh when you event specific okay so yeah as you can see um this is basically uh this this goes into into the uh what you're what you're gonna collect at the end point you can see in here there's it's collecting application log system logs windows sysmon uh powershell logs so you can specify all the logs that you're going to collect this is a good template um and you can you can tune this you can add add add events to it but uh yeah so so this template getting get started gets you most of the most important this one has this one in it as well um you can always room if you're not in the running system you can remove it but uh yeah so there it is this is got pretty pretty good pretty good uh basic uh you know logging um and this will this will get distributed to each one of the endpoints that's subscribed to this whack so yeah basically that's that okay all right so there we go and then this is just something about the subscription configuration dialogue advanced stuff you want to minimize bandwidth latency we'll send the data quickly another thing is is this it's going to have http or https um you can select http because the actual payload of the of the packets is is encrypted already so https would be double encryption https is is is useful if you're if you're pushing to offs onto a server off site or into into a cloud endpoint so because um that requires an http https connection for authentication so so but that's that's available too if you want let's say you want to send the you have a whack in the cloud and you want to send the uh the data directly to the to the wek in the cloud so you could you can do https here as well yeah so there's the query filter this is this is actually uh let me show this song i'm gonna break out here real quick just to kind of show you what this is all this business looks like okay all right so here we go here we are in in the in the wac right an event viewer in the whack for events subscriptions so we go to subscriptions new subscription all right yeah so there we go so this is what i showed you before so this is this is a this is that my one subscription on this server this is this is the other server which is the domain controller connected in here um and uh these are this is the subscription i have set up here um that's the subscription name and then if you go to select events you can see that's where you just literally yeah sorry you literally just paste that xml file into this tab and then um you're good to go basically and then the great thing about it is that um this is that every time you every time you update this you change the log configuration on on on that your web group it ought to on any endpoint subscribe automatically when it connects it's going to update its filter and it's going to change you could tune the actual logging on the endpoint just just from this this location here so it's quite nice for for distributed scalable management yeah so okay there we go that's that's your wac event query filter there we go right so we talked about that minimize latency all right so now so now uh now we're gonna we're gonna create a group policy for the web for the web endpoint um so this is basically uh just to sort of give you uh sort of a background we're going to go through these next few slides so you kind of give you show you what it is so this is the policy here i have this this is my domain this is my web policy this is what the policy looks like these are these are the elements of the group policy that we're gonna we're gonna we're gonna modify and uh yeah so you can see this is the first slide it's going to be where we're going to create in in restricted groups of the policy we're going to have to give the event log readers group this this cape network service capability so we're going to do that right so you go in go into restricted groups in the group policy and then you add for the event you add the event log readers group and then you add give it the the network service membership so that basically the event log readers groups have the net is able to read read uh events this is needed this is needed for it to re for the uh end point to read the law the web endpoint read the logs and send it to uh the wac so this is required in the group policies this is the group as i said this is the group policy we're going to push out to the web endpoint so this is the beginnings of it um and so this is the first first modification you need to make as you create this group policy in restricted groups you know adding network service into your authority network source event log readers group all right second thing you need to do we need to do is in system services we need to uh under windows remote management um we need to you know make this startup automatically so we have a winrm starting up our max on each endpoint it's another important thing uh all right and then you know this is the uh other event forwarding when you enable event forwarding um you know you can bump up bump up the forwarding rate you know 100 200 is probably good uh bump up the forwarding rate a bit so that's the event forwarding resource use you need something to add that and um sorry all right and then then i think that's it oh okay we got that okay yeah okay sorry about that i missed stuff i missed one thing here yeah so then after you you set up the event forwarding um you basically uh you configure uh you configure uh subscription manager and then you put in this this uh string is basically the uh the the uh fqdn of your uh of your web server and then the rest of it is basically you know standards ws man subscription manager and then the left like refresh rate so that these piece needs to be added and then um under uh yeah so so under uh the event log service of the policy uh you wanna make sure that um you add this weird log access string which i put up there this is kind of this is this is a kind of a weird thing um kind of one of those uh sort of hard to kind of it's not well documented um and it's especially for domain controllers but in the uh the you know the security sect uh section of the event log service in the in the in the policy group policy um you have to add this string in the log access um so that's important that's why i put this in here um that string up there okay and then there we go once once you get all that configured um yeah there's the wet the wac subscription source computer is checked in it'll tell you per per subscription which which source computers have checked into that subscription yeah and then there you go um okay all right so uh pitfalls um deployment so the network service account needs to have access to log readers group we talked about that how to configure that in the policy when rm um is required we talked about that scale wax adequately we talked about that so each each one of these wax should have two thousand four thousand endpoints um and then um just a little bit is you know when if you when you're first getting started you know start start with like targeted area so that you can you know debug everything and make sure everything's working nicely and then this is a this is uh another uh another uh interesting thing here so it's so so as you as you scale up uh these end points now what's going to happen is each each wack then there's actual each each um event uh as each each endpoint has a registry entry um in the uh in the wac um and and so so as you as thousands of endpoints come in they're gonna this this registry key is gonna have some as have these endpoints added to it for as an event source um now as you decommission endpoints um you're going to have to prune the registry um so this is this this url has a nice set of tools that that basically has a scripts that basically just run it on the wek and it automatically as it is running as a as a scheduled task and automatically will prune the registry for you so periodically run that task and if endpoints have been decommissioned from the wac it'll automatically prune that prune those out um another another script on here is uh is is basically a script for auto basically what it lets you do is it creates multiple groups um and then um you you you know it'll auto assign um uh left end points to those groups and then those groups are actually managed by the wax this way you will automatically get the right server to the right whack um you could take a quick peek at that script sorry about that yeah so this is this is for more like when you're when you're like you have multiple wax and then you need to auto assign um left end points to different groups and then have those groups as as enrolled in that in each for that particular set of endpoints and this way you can scale it to quite a large large amount okay let's see here okay so yeah so here it is it's the uh maintain computer group script and then this this this script here will actually basically it auto it auto subscribes the the end points to uh to the uh different um groups and then to and then as of those groups you just add add a group just add then instead of adding into those computers you add just add the groups to the to you know that each wax is is is enrolling and then this script will automatically assign your endpoints to those groups and then um yeah so in this way you can you can as as you know get a very very scalable environment going so there's that okay so let's get back on track so let's recognize deployment and then there's another nice little project here which it's got uh it's got some really nice scripts just for setting up logging and this has got some some very nice uh defcon 3 is actually quite nice it's got a bunch of scripts so setting up sysmon configuring edrs network device logging and things like that so yeah this is worth taking a look at it's also in that black hills thing okay so now um i'm going to go step into a little bit of a cloud the cloud stuff here talk a little bit about engineer monitor um so azure monitor what is azure monitor basically it's kind of debate the in in in azure it's kind of the baseline um log analytics um so basically it can take it can take um it works both from fl logs and native azure as well as logs from on-prem um you can bring all those in so that's that's so in the case of what we just talked about so if you you would just put the on-prem azure on-prem the log log agent on on those wax and then you bring you can bring all this data into is your monitor um and to do a analytic analysis in our analytics um [Music] we'll talk briefly about sentinel which is a sort of like corner but sort of i think asia monitors kind of like a sort of like a date a data aggregation platform with a little bit of analytics like very like like mini sim like uh but then sentinels kind of like a full blown sim like with all the bells and whistles and um you know the threat hunting capability and all that which we'll talk we'll touch upon but so yeah so this is agent monitor do so it can it can take it could take um logs and events from all of it azure basically and then um and then also from external sources on-prem sources um like we just talked about with the web infrastructure so some of the azure activity logs that could we can bring in you can bring in administrative activity logs um security logs policy logs service health logs all that's available at azure monitor you can monitor azure 8d all of azer activity logs uh all the security logs um uh you can set up set up something and we'll talk about a little bit so it's a workspace where you bring all these um ajd logs in and then you can do some analysis on you know different there's some insights you can go to like you know and now analyzing uh you know you know atypical travel like atypical log ons you know you know ip addresses with malware password spraying all this is doable um within uh azure monitor um and not not to uh i'm focusing on just because of for sake of time i'm focusing on azure azure um the azure side of the house for cloud um with with azure modern sentinel but splunk can do the same as well here splunk has the same capabilities it can uh it can it can take these take these logs as well you could take the weft logs as well with the heavy forwarder so so this is just because just focusing on azure for cloud right now for a sake of time so yeah so that's azure ad monitoring which you can do um with uh with azure monitor um then infrastructure monitoring um this this this actually um lets you uh monitor infrastructure and this is kind of would be on vms and you know that's not infrastructure components of vms running in azure or vms running in uh um running in on-prem so so the either you would have the log analytics agent which is apparently being deprecated now and we got asia minor agent um is coming um actually into more into uh play and then but that requires your modern agent was an arc um it's a it's an external multiply as your framework will touch on that very briefly but anyway so for infrastructure monitoring so you got these these agents um they can run in azure on azure instances both linux and windows and uh also on-prem so you can you can sort of integrate your whole azure infrastructure with your on-prem infrastructure very nicely and this is um so uh so in order to uh get started with logging right so you basically uh basically uh create this thing called the log analytics workspace so this is kind of in azure monitors it's kind of where you bring all the data into and where you manage the data so this is a this is what the log analytics workspace looks like as you can see bring in different data sources and then um you can then proceed to do analysis some type of an analysis on it i've got a few slides on on that as well so yeah so so this this would be okay so this would be um like sort of uh you know a log subscription centralized log log architecture on azure right so you have the you have the different subscriptions the nice thing about it is these subscriptions can be in different tenants um right in different accounts different tenants and you can actually have a central central um log blog aggression workspace um and then you can just pull only the logs that you want into the central uh log subscription which is nice for security because you may not want you may not want application logs or performance logs and that type of log in in the sort of a security analytics space so this is not lets you just grab like resource logs which which tell you what's going on in the uh with the azure resource monitor and like what what the infrastructure what's happening in the infrastructure of these these different subscriptions so this is kind of a nice like centralized log architecture highly highly distributable um yeah and then this is this is kind of the the what the log analytics workspace looks like when you're bringing different types of data in so these are this is this is the vm on the left and these vms can be these instances can be in azure you know i believe it could even be in other clouds um and then um or on-prem and then um you've got the log analytics agent which then uses the source editing key to push data to the uh to the log analytics workspace um you can also azure monitor metrics right so just some you know metrics could be pushed then you can um for azure monitor agent which is uh requires an azure vm or arc as we said uh yeah you then then that that the nice thing about azure monitors is it deals with all this um you know work system the system assignment it manages identity endpoint identity for you makes it a little easier to bring data in that goes to log in especially a nice thing and you can do also in a workspace you can also push push data out to storage um you know cold storage um different types of storage so you can have archives and stuff like that and just have only only certain data where it works at one time save money and then um you can push out software event hub so if you're doing alerts and stuff like that and then sentinel actually sits on top of um workspace uh logins workspaces so you put a sentinel instance um and i know i know that a lot you know each each college with it with the a5 licensing or or is going to get some of this is just available right out of the box as part of your package so you can actually a lot of this you already have you're able to you're going to be able to set up some long analysis workspaces you have to throw you can even throw your own little sentinel on top of it uh so you have a with and with the wefweck architecture you could quickly do very nice sort of like you know build your own log log log analytics infrastructure in a highly scalable easy to manage way we are having enough time very stuff okay all right well i'm almost i'm gonna get there how much more five minutes ten minutes five minutes is good yeah five minutes okay i'll quickly go through the rest okay so so i think i think we got the message that's that was kind of mostly what i wanted to get through like so you got you got the uh you've got the uh building your windows infrastructure logging aggregating that and then bringing it into the cloud as in this case the azure monitor with the login analytics workspace then um this is this is a little bit about arc so arc is uh this is the arc architecture so this is basically the on-prem stuff and then this is this basically lets you put push data to log analytics and this this is needed if you're uh using the uh the ama architecture and then azure sentinel real quickly it sits on top of login workspace that we just talked about has over 96 source data sources very very very robust test soar so you can actually create security playbooks um with uh with all your data so you can actually analyze the data and then do automation on the analysis and then do responses um scripted responses um and uh yeah so what is the value of sentinel as machine learning as correlation analysis rules analysis rules you can crystal query language alerts create incidents monitor workbooks rule templates um yeah so different different you you set up the types of events you want to alert on like mfa simple user password spraying you can fire all playbooks that integrates with azure logic apps where you see a bunch of password spraying and so you've been lock you know create a lot you know lock out that particular endpoint uh a malicious endpoint um or uh mfa's full user send them a warning or disable them there's all kinds of things you can do with these playbooks okay hunting it's got built-in hunting templates so you can set up queries on your data and integrate data that comes in and then you can look for uh you know anomalous activity uh these are the these are the workbooks this let's also let's you set up analyze the data um set up charts and like graphs of statistics this was really great for doing and out the quick and quick analysis hands-on the live analysis of events and especially um if you're looking to see some statistical uh graphs and stuff like that very good for that deceptive workbooks these are the playbooks that you talked about you can create playbooks um so you can do a full automation of your responding to uh certain events um it also has a uh center has a nice integration of threat intelligence so different threats angels feeds are totally integrated so you can actually bring in your threat intelligence free through the text taxi framework um and then yeah the conclusion so so yeah web is in whack is a great way to aggregate logs which in large environments it actually works great in small environments too but but once you get thousands of thousands endpoints instead of trying to manage agents on each endpoints great way to go you can manage your subscriptions using filters so you don't have to mess around with with uh you know tuning logging on each endpoint you minimize your sim agents your log collector agents you get sim flexibility which means you're not stuck on a certain sim um you can move push data to multiple sims if you need to uh and then azure monitor with log n smooth space provides effective way to aggregate multiple log sources and perform analysis and then you got sentinel as well which is kind of like the you know more advanced uh you know full-on security security um an analytics framework and yeah that's that's basically it and then there's a nice reference uh which goes into configuring setting up uh wek wef um which a lot of luck covers a lot of what i covered but you got it you got also a guy guiding you through it hands hands-on so so hey so that's what i got so any questions yeah i think somebody had her their hand raised if they can type their question see it did jennifer had a question uh cindy or yes i can understand this no i just say you sent uh some message here oh dan has some questions okay can you use other accounts beside network accounts no i'm not sure about that um it's a good question uh you mean for the uh for you mean for the for the for the data collection [Music] you mean i guess maybe uh if you want to send an email to yeah i mean he said if you can uh then use uh powershell endpoints in rm and set services accounts uh you know it's pot it's possible i don't know that the the minimum the minimum requirement is that the log the log the log readers group in order to to set send data to the wac needs to have that permission um you know it's possible i didn't tried that method uh but uh but yeah i mean um i'll i'll look into it and let you know um and as far as i see that other question uh right you know generac isn't really load balance capable uh you basically your load balancing but what you can do is you can spec okay so you could specify multiple wax in the in the uh in the group policy and you can if one weck isn't available it'll go to a different way so that's kind of how you would do the load balancing actually um yeah yeah yeah so so yeah so but definitely i'm about to end point permissions that i didn't need to research on that but uh but yeah and this is kind of um the architecture you know as as we work on the sockets the architecture we're going to go with for the for the end points and um you know we probably right now we're about to splunk as a sim but this is a good architecture to get to get get the up points up and going um and then oh yeah so the other one is the pass the hash attack um well um you know evil evil win rm um yeah you want you want to make sure that the that you know that that you've the win rm is locked down you have good good good authentication um um yeah so the pass the hash attack is gonna you know you wanna make sure that um yeah i mean you you're you're you're sort of locked down and the hashes hashes aren't easily accessible um and uh you've got something maybe running on that end point that prevents the uh prevents the uh pass the hash type of activity but but yeah there's something to do something to do with your lateral you know your your endpoint edr and your lower movement um sort of strategy and make sure you're not you know you're not leaking hashes on the network with the nmr and all that stuff so so um so yeah so passage attack is actual infrastructure recommendation um um it has nothing to do with this this is this this wind arm is required for the communications uh between between the uh the wek and the weft so that's mostly what it's about um oh okay then there's a okay all right there you go no dan figured it out when rm can have ip allow lists up okay so so there there's the answer where you can you can limit you can limit what what can connect so you can just just keep just keep just keep um yeah so you can lock down um the wek left interaction yeah and that's probably configurable through the group policy like we when you push down the uh the group positive configuration for the for the weft all right i guess uh if you guys have any further question uh cindy if you fiona post larry's email address uh folks can email him and he will respond accordingly uh uh let's regroup in 10 minutes around 11 20 with our next talk after the break so thank you very much hang tight
2022-07-12