Deploying and managing Windows Information Protection - BRK3011
Welcome. To windows information, protection. Windows. Information, protection, is a policy that IT admins, can deploy to help protect enterprise, data from, being accidentally, copied to the wrong place. Let's. Look at how Windows Information, protection can, help protect data. John. Is a busy professional trying, to get some work done from home, he. Needs to update a PowerPoint, presentation with the latest sales figures so, he saves an excel file from Outlook on the desktop the. Spreadsheet, is tagged as a work document shown. Here by the briefcase, he. Opens a spreadsheet and copies the latest sales numbers. Then. He goes to onedrive to open his presentation, which is also tagged as a work document by the briefcase, and file ownership. He. Saves the updated presentation, with a new name, PowerPoint. Is aware this is a work document and keeps the protection. While. Editing the presentation. He sees an email from another parent, reminding, him to add the pizza budget to the PTA newsletter. He. Highlights the pizza budget but gets interrupted before he could copy it. When. He returns he sees the pizza budget is highlighted, and creates a personal word document, for the school. When. He tries to paste into the newsletter, a warning, says that the action will add work content, to a personal, document, he. Realizes that he forgot to copy the pizza budget and still has the sales figures on the clipboard from. The email he copies the pizza budget and pastes it into the PTA newsletter, the, warning helps John avoid a potential, mistake, Windows. Information protection helps, John prevent accidental, leaks and keeps, his work document, secure by automatically, protecting. The content, to learn more about what windows information, protection, can do for you see, aka ms, forward, slash WIP, Docs. So. Good morning everyone. I'm, actually surprised, that there's only like, more. Than three people here on a Friday morning thanks. Everyone for coming I, hope, you've had a really great ignite so far learned a lot and we'll. Be able to take that home and and be more successful, those. Of you who are playing, the Microsoft, mission, statement, bingo may check up the right hand box. Out. Of curiosity how, many people have heard me speak about windows information protection again uh before. As, a few of you okay, I apologize in advance the, jokes are no funnier the second time. Wow. You're a cold room is everyone really hungover Wow. Okay. So. I'm going to cover the who what when where why and how of Windows information protection not. Quite in that order but pretty close my. Name is Derek Adam and I'm a senior program manager in Windows and I work on endpoint protection. Technologies. One of them obviously has windows information protection the reason you're here hashtag, ma'am on Windows, I. Think. We'll start with who and I'm gonna do this in a strange way, I'm. Going to introduce you to you I think. About the enterprise customer, a lot, and. There's a couple of personas, that we think about the. First one of course being, the IT admin, I. Know. That you guys have a really tough job actually. Not. The least of which because most of the time the people that you are serving, don't. Understand, what, you do how you do it or more, importantly why. So. As a misunderstood. Character, I'm gonna compare you to another. Misunderstood. Character, oh. It. Got awkward for a moment there didn't it. Yeah. Well. Okay so mixed, feelings here right if you. Think about it it's not all bad right the P but the people he serves. Want. More of what he's got. They. Ascribed near magical, powers to him. But. If you felt a little uncomfortable it might have been because he's a little off-center.
Maybe, He's crazy. Crazy. Why is he crazy he, wants absolutely everything walked down in his domain, nothing. Is ever supposed, to leave the domain and you, have all these rules and, procedures, to keep it that way but. He's wild about the eyes because, he, knows that things are still leaving you know it he. Knows it, mr. slugworth knows it I. Submit. To you that if you are also going crazy it's because your users are making you crazy. Here. Are some crazy numbers, from real life. This. Is from a survey a few years ago but I think it's still meaningful because it's about human nature. 87%. Of. This. Was a survey of senior, managers, so VP and up said. That they regularly, uploaded, work files to. Personal. Cloud or personal. Email and more. Than half had, admitted, in writing that they had accidentally, said something. Sensitive. To someone that they really, should not have and there. Are real dollar costs. Associated. With those. Breaches. So. What do you need. You. Need your users to be able to respect the stewardship, of data that you might give them, not. Reveal company's secrets, and. Respect. Your boundaries your terms of use so. You're not the only enterprise. Customer I think about there's, also your user. The. Information worker I've. Started a theme can, anyone okay no spoilers, for people who've seen this before can, anyone take a guess about who, this might be in my theme, that I started go, ahead and shout it out oh. This. Is probably, the best the, children, that's, pretty good actually because it's just the people in the story people, like you and me and, what. Do we want, we. Just want our stuff, we. Want access to our personal files we wanted some little, management, as possible, and. If. There's going to be a DLP solution it, really. Should recognize, that we make mistakes we're all human. It. Happens to the best of us I'll give you a few examples. About.
This Time last year, Statoil. This. Is the, Norwegian, energy company had, a massive bridge, a tons. Of PII was available searchable. On the web and this happened, because. Some. People just wanted to get their job done they uploaded, things. They needed translated, to a free translation service, and. Free. Meant that they were going to be using, some help on Google, so. Now things like. Contracts. Dismissal. Letters reductions. In force. Passwords. Code. This, is really sensitive stuff. Okay. You might say well Derrick you're just you're cherry-picking, okay. Well I'll let me take another one. Heathrow. Airport. Some. Member of the public found a USB, stick that had megabytes. Upon megabytes, of data. About. The, Heathrow Airport, things. Like this, is where the Queen needs to go and these are the credentials, that you need in order to escort, her. The. Secret passages, for getting ministers to and fro this was considered a national security risk and it happened, because. They. Didn't encrypt the files. Okay. I like, to keep this fresh so. I went looking for things this year and I didn't find odd thing I found lots of things and rather than just pick on one company I just went for an industry, health. Care health. Care should protect your data right well. The most frequent, cause of breach, in health care last. Quarter. Was. Human error oh. By. The way it was also the same. Highest. Cause the, quarter before that and the. Quarter before that and the, quarter before that and the, quarter before that and each, of those quarters. Were higher than the last quarter, you can go and look this up at least for the last year. So. This is a risk that you need to, prioritize. The. Risk is actually greater for access. Within and it's usually. Accidental. This. Is something you need to worry about not just on your mobile. Devices this, is also, about laptops, and desktops. Because, where do you have the most access to work data to potentially, leak it there, you go. To. Try to get, this idea across to people my, marketing team a. Couple, years ago put together a. Kind. Of a Super, Bowl. Ad. Style. Thing. It's, not on brand so I'm gonna just acknowledge this up front to the marketing people who are saying don't play that because, it doesn't have the new brand this, was when it was still called enterprise data protection, I.
Hope, That they'll I'll. Be able to work with the mic marketing team to to, get this on brand but it's just so good I had to share it have a look. Most. Data leaks will. Not, really intentional, I managed. IT farrelly clouds marketing, org which is, four. Hundred and fifty seats. Like. Any place around people. Just can make, mistakes. They. Try to upload confidential. Documents, onto personal, cloud, storage. Yeah. What. I would like to say is that is the stupidest. Idea I have ever heard. And. Copy. And paste business. Information. That's really confidential, on to, the non corporate sites. We. Needed a solution that, could tell the difference between the, personal documents, and those really critical, business documents, that need to be protected. Because. A lot of people around here they just they. Don't see. Microsoft's. Enterprise data. Protection I, do. Sleep a little, better. Just. A little. Wow. Right that's, what you have to defend against. You. Have a lot of protection needs I know it and it's, not just one technology that will give it to you we understand, that so, I want to put Windows. Information, protection in context. Where, is it with. All of the other things that we do to help prevent, data leak so. On the one end you've got device, protection you've, also got data separation. Leak, protection and, you, do occasionally, need to restrict, your sharing, but so you are sharing but in a specifically. Restrained, way on. The. One end we have BitLocker. This. Is for the case where the mistake that was made is that they literally just lost their laptop. Okay. And on, the other end of the spectrum we've, got sharing. Protection, and this is where the users present, thinking very carefully about security. And. They. Want to say limit. Who it is that they're sharing to they may want to set extra policies, that apply within, the. Document. Or etc and for that we have Azure information, protection, we. Also have office, information protection that helps protect against leaks. Through. Say email, you, know that's where you get that gold bar that says you're sending this outside of the company. But. Then that leaves most of the time most. Of the data. People. Are just doing their job not thinking carefully about security, and that, is where when, is information protection, fills. A gap so. We. Can separate out work data from personal data we, do this with encryption and we protected, it rest, locally, and on, removable, media, we. Can protect. Prevent, unauthorized, apps from accessing, that data and. Giving. A common experience across the whole thing so, you don't have to feel like you're jumping into a little container you just use Windows the way you always have. Giving. A seamless, integration, across. Any. App and this. Has actually been available since Windows. 10. Anniversary. Edition so 1607. All of you should already have it, now. This is where it gets a little sketchy I you. Probably noticed I was making. Some changes here at the beginning this. Demo is something, I set up like literally. In the first 10 minutes of this hour so, wish me luck I. Mean as well just show you how it works okay. So, this starts off with policy. There's. A, number, of ways that you can get policy. The. The, way that I'm gonna show you here is on an MDM. Managed. Device so. This is like, the BYOD, scenario, I've, also done this with, an azure joined, machine and a domain, joined machine, so. Regardless of how you're getting policy, once, we give you policy this is when we start using context. To, protect that data, one. Of those places that you get work data from is say onedrive for business and you can see right now all. Of these files are getting protected based, on the fact that this is an account that's work and this, is an account that is not you. Shouldn't be applying. Policy, to my personal, data and that includes you shouldn't be wiping it turns. Out Dropbox, does the same thing, they. Protect, data on download, in. The work account but not in a personal account, these. Applications. Partner. To. Guard. That boundary for you right and. For. Example if I try to share. A document I'm gonna share it into my onedrive, for business well. Actually no I dropped it onto my onedrive personal, oh okay. Um I, don't really want to be audited for doing something like that so I'll cancel that out, another. Another way that data might leak off of this machine is. Say. I could put it into a USB. Stick and. Let. Me choose. Something to. Drop. Into this, USB, stick. So. I have a couple of options here, my. Policy, is to allow overrides. It. Makes for a better demo I can show more things but. I'm going to copy this as a work document and this is where I'm going to go for some audience participation. Can. I have someone who, has a laptop in, the front row and is.
Not A Microsoft, employee. Maybe. You okay. Try. To open. Up. This. File. Alright. Yeah. Back in your seat actually while he's doing that why don't I go. And start. Showing you something else doing. The Martha Stewart thing here while that simmers, we'll go on to something else. There's. Another place that we get data and that's through a browser and here. I have this. Is literally my, work. Onedrive, for business dialed-in, and if I download. A document, from. From. There because this is a managed site you see this briefcase, over, here when, I save it and, open. It you. See it's automatically, protected, but I could just as easily have gone to. Onedrive. Personal, and, download a document from there and, it. Would not be protected. Looks. Like I'm having some Network difficulties, so I'll just pick. Up a different. Pick. It up from a different location I've, got. My. Onedrive here. So. I can open up something. Like this cookie recipe, and. I can open it in any application, right I could, open it with something that only opens. Personal. Files right. Try. WordPad. No. Problem. But. If I tried to open up that secret document that I downloaded let. Me pull, that up my. Downloads. And, I, try to open that with WordPad. Let's. Find out ooh access. Denied. That's. Because we. Restrict, which applications. Your work data can be accessed with, and this. Actually. Helps for, safe third-party, sync engines let's say that I hadn't put. Dropbox. On my list then it wouldn't literally, not be able to open this file. If. I want to open up this secret. Formula I'm gonna have to use a work application. And. That's. Gonna be word. Opens. Work and personal, files. There. It is my secret formula for, success. And. You can see like I could. Get a pretty, busy desktop, here I've got like four or five windows, and it could be that I want to copy some of this data what. If I want to copy it into that report from my. My. Weekly report to my boss or something like that ah that. Wasn't actually a work document we can detect this boundary and. Protect. The data from being accidentally leaked that way as well. There's. Actually so. I've talked, about context. In a couple of different ways one is by account through, these, enlightened, applications. Like say Outlook. Outlook if. I tried, to take this, this. Is dialed into my work account and I tried to take this and put it into my personal. Hotmail account say, for example it also guards the boundary. But. We've, actually added another, way of detecting, work data you, might have seen in some of the. Keynotes. That. We. Have something, called this Microsoft, Information, protection initiative. Where. We can label office, documents, and PDFs and that sort of thing to, indicate that their work we, also have done an integration, with them so you can indicate that a label is.
Oh. Thank. You were you able to open it no. No. Open for you there you go come, on round of applause for our. All. Right so I have my personal hotmail, account my, friend Mike were. You know friends outside of work and so he has both of my email addresses, he was maybe, labeling, a document, on his you. Know word on Microsoft. Sorry, Microsoft Word on a Macintosh, and he's, sending me an email and, he has both my email addresses he, ends up sending it to me at a what, is my personal email, right this doesn't have a managed symbol on it when, I download, this confidential, document. And. Save. It. Windows. Defender ATP, is actually scanning files for viruses. And whatnot it can also scan, it to see if it's got a label on it and if it does it. Will automatically, protect that data. Okay. Come on come on that's, pretty good right it's. New at least it's, new. I'm. Gonna see if I, was to, download, power bi in the background while we were doing this Oh miracle. Of miracles it did. What. I want to show you now is another context. And that. Is an. Unenlightened. Application. Unaligned. Applications. Are well. Okay this, might take a while so I'm gonna skip it I also. Have some slides to talk about this point so I'll just move on. I want. To leave enough time for you to have your questions, so. If you're keeping track at home we've talked about who we've talked about why and, we've talked a little bit about what, here's. A little bit more so there's this idea of you've got personal applications, there's, this one experience, you're used to in Windows, and there's. Things that just don't need to have access to work data right. Your social media applications. Maybe, utility it's like the weather application, or your games those. Are all of your, unmanaged. Applications, and at. The other end we've. Got managed. Applications. Things, that only handle work data, the. Data is isolated. It's, kept encrypted, at rest, you, control, the keys and. It's. Manageable. Through MDM, even, for mam which by, that I mean, without. Enrollment. We. Block into audit, the exchange of data between these two things I showed. You overrides, but, there's another, enforcement. Level that we call hide overrides, it's. Exposed, in in tune as block just, for simplicity's, sake so, people get the idea, by. Now you've probably noticed, though that I left a little gap in the middle that's not a gap. That's. The list of applications that are actually standing on the boundary between those two worlds they, are handling both, kinds, of content, and, keeping. Them safe and secure even. From each other. I'm. Going to spend another couple of minutes on this because this is the space, that I get the most questions on. There. Are a ton of app applications. There enlightened, you. Saw some of them here's a bunch more these, are the first party applications, so, you have office. You've got browsers. You've got, utility. Applications. In Windows so you can view content. There's. Also unenlightened, applications. And. This is where the questions usually arise how, do I manage this, there's. Two options one. Option is, allow, it. When. You allow the application. And it's not enlightened, we, put baby in a corner. Everything. That it writes to disk every dip, every file that it modifies becomes, work data so, caution, if, that's. Going to touch personal, data you could be invading, their space it might not be a good idea this is really meant for line. Of business applications things, like power bi or. Maybe. Your HR, application. Internal. Finance apps that sort of thing and. This. Is something you can do on a fully managed device. With. MDM policy, the. Other option, is you can exempt, it and. By. That we mean essentially. For that application. What, policy doesn't apply we don't Auto encrypt, it we. Don't apply any copy-paste, restrictions. But. You do get access to your work, and personal data, without, impacting, the experience, and if you're using some of these other ways to protect your data it's still at least being protected, and usable, and you're.
Going To get the value, out of, office. And all of these other applications. Protecting. Data between them, 80%, of your data is going, to be in office another. 10% is, in PDFs, that you can read, in edge. So. Go ahead and get the value as quickly as you can there, is of course a third option really. That third option is go, and enlighten, the application, if you, own an application. As an, ISV, or, maybe you have an. Internal IT department, that develops applications, and you want to be able to have that used. On a man managed device. There's. A fairly easy way to do that you you can declare it as. Safe. For auto encryption, and. Recompile. The application if. You. Want to have that good experience, of handling work and personal, data I direct, you here to their our dev guide and. If. You. Have, difficulties. You can go, ahead and reach out to the development, assistance. That we have at Microsoft, it may even eventually, get to me. Protection. Across data flows is probably what you're most interested in, I've. Talked about this a little bit already but. The idea is policy. Comes down we. Provision, keys on the device. And then. That. Data coming from your, corporation, whether it's a corporate. Cloud or, from. Your local area network it's automatically. Protected. Apps. Can also automatically, protect data if they're, an unenlightened app or they're an app that knows that this is coming from a work location, and it's, maintained. Anywhere, as you just saw. I'm. Gonna go on a limb, selectively. Wiping, corporate data on demand. Who. Would like to see me actually wipe this machine. Okay. I have. Not rehearsed this so. Wish, me luck. So. It's as simple as, on. The client machine you. Can do this on either side right if you. Are. If. You're, managing it in in tune what. You do is you retire the device that does a selective, wipe but, if the user themselves, ahead and disconnects, the device. Okay. First we're gonna warn you we're gonna remove some stuff is that okay with you all. Right I will go ahead and do that thing ah. That. Looks gone. Let's. Go ahead and see what happened to Outlook I've never done this on stage before by the way and my. Boss is gonna be super mad at me because now I don't have access to all my work data. Oh. Because. I closed it hard go. Ahead and open it. What. I'm checking now is to see did I even have my work account. Nope. It's gone all I've got is my hotmail, so. They're you you actually have a Selective wait experience. On full, Windows. Come. On that was dangerous give, me some applause killing. Me people. All. Right so. A lot of questions that I get also, are about, where. Does Windows Information protection and as your information, work together we. Have a lot of things that are branded with information, protection in their title we, know that and we've started working together and just to call it a Microsoft, Information protection initiative. Back. In the day when we first launched, windows information, protection these were side by side technologies. WIPP. Gave you that context, of where, protection. You. Didn't have to take an action it was built into the action you were taking already, downloading. The data using. A work only application. I didn't. Show this before but the clipboard experience between to, work applications. In a work context. Is seamless, you don't see those pop ups that I was showing you they only show up when you're crossing the boundary. The. Protected, sharing, story is really, keep it in the family you, can upload that to SharePoint Online if, it's my SharePoint online you can put that on my file servers, but. You can't send it anywhere else that's how you're going to share the data the. Data will end up leaving the machine in the clear but, it will not be going to a place that shouldn't. As. Your. Information, protection on the other hand gives, more granular, policies, than windows information, protection, usually.
It Has some, smarts within the application. Like if you've ever sent a do, not forward email, that's. A IP at work you. May be familiar with this as the azure RMS, technology, but, at a IP builds, on that to include labels it. Does, require a user action though and, that's. The that's, probably one of the main differences. These. Were side by side technology. Different. Keys but, complementary, scenarios. Then. We did our first integration. In 1703. Also, known as the creators update. This. Is when we added that rms key being used to protect files when. They roam, like. I said before as your information protection is the, protected, roaming, data scenario, and. So. We removed one of those seams in our story, you. Off to the azure RMS server and on. A creators update or later machine, you, just get access to your data, it's. Actually very easy to set up I'll show it a little bit later you have a tenant wide user access, by default but if you want you, can also apply an RMS, template. That, can enable you to scope. It down to, a smaller group say, you want to have a special policy, for your, senior. Leadership team or, you can broaden it and say I want to have a business to business relationship and, anyone. That these two companies can do it what. You need to. Get this going is. You. Need to check a box basically you need to have an, e3, license, in Intune and. That's. It. And. Of course you need the creator's update which most of you should already have if you haven't rolled it out yet. Why. Not skip to 1809. Speaking. Of 1809, what have we done for you lately right. We. Did another, integration, with. AIP. Myth. Labels. What. You get is that when. You whenever, you create or modify or download. A a. File, the. That has that label it's, automatically, set and protected. I. Didn't. Show you that did I oh well, too late I wiped my device. What. You need is M. 365. Microsoft. No. Story protection, Microsoft, comm. Go. To the security, and compliance Center and you. Need Windows 1809. With, WD, ATP Windows, Defender advanced, threat protection. That's, the thing that's scanning files for malware and that, now can be scanning for labels in your office, and PDF files. In. Fact why don't I show you how that's set up. Okay, unintentionally, this is also a windows hello demo. All. Right so. You start off here in, protection. Dot office comm I'm currently being. Redirected there and it's, as simple as this you go to classifications. Choose. Labels. You. Look at your sensitivity, labels. Go. Erase those dots say. I want all of my confidential, data to be automatically.
Marked. With. Whip I'd go into the data loss prevention section. Edit. That and it's. One click, save. It, that's. It I just I just configured, whip for her labels, okay. It wasn't that exciting but it was fast. Going. Forward I can't, really talk about, future. Plans but, I can talk about ideas, we. Want this to work together we're gonna see more integrations. In these technologies, we want a IP to benefit, Windows, Defender ATP. To benefit, whip and vice versa. So. Here are a few ideas have, been throwing around with my partners one. Is that W. DHCP could use whip for, a number of things auditing. Good. Idea to know when data is leaking, right and then, maybe when if you see something, being leaked and that, kind of triggers it like sure I send, you your w-2 to your person. Or to your work email and yeah you're gonna have to decrypt that to send it to your accountant. Or something like that but if you're doing this to a thousand, files maybe I want to put a stop to that in fact, maybe they will put a stop to that and halt. Exfiltration. Maybe. I. Don't. Know what if there's even a timeline for this but you, can see that these things can come together. We. Could have more, client classification. We could have more labeling, we could have whippin. A IP protection. Being an, outcome, not just one whip. Could maybe trigger a IP sharing scenarios, the. Long and the short of it is that we recognize that. Asking. The user to do more thinking is actually taking, away from their, energy to do their job and you, you don't get any security, benefit when they make a mistake so we want more data to be protected, automatically. Okay. Is there anything else. Yes. Ma'am. I, told. You the jokes not no better. Without. Enrollment, is what we mean so ma'am. Without, enrollment, limits the policy, scope you can get ma'am policy, delivered through MDM on my Azure, Active Directory joint. Machine my, domain joint machine what have you but, if you want to do this on a personal. Device. They. Kind of don't appreciate it if you have the ability, to go and nuke it and do a factory reset so.
With, A without, enrollment, policy, you can't do that but, you still have control over some of your data and with, is the app management. Part of mam. One. Caveat here is that only your enlightened, applications. Can, be managed. On a mam only. Device, that's, because we don't want to have any risk of messing up the user experience, on a fully. Managed machine sure you, want to go ahead and tag, everything as work and you tell them upfront this is my device my policy. All my, data okay but you can't do that to their personal device so. Unenlightened, apps aren't allowed. Maybe. You want it to be maybe, you haven't a. Line, of business app that you want to enable you. Can mark it that's, the asterisk, in the enlightened. Tag. It as safe, for auto encryption, and then they will still be able to use it it. Requires. A ad integration, but. The good thing is it's, available on home and enterprise. And pro so. You can actually have real mam on any device that's a desktop, with. Windows 10. 17:03. If. You're. Very interested, in mam in general, and maybe. You are because you're here on a Friday morning, there's, a great talk that you missed yesterday. From. My good friend Matt be. Arcade. 3005. You. Go ahead and stream it after this. What. Else have we done we, made it a little easier for you to get your policy, right one, of the big points of angst was, not. Knowing what. Apps are actually being used for work this, kind of surprised us but, no really you don't know and you have good reasons not to know maybe, your spread across lots of geo locations, so. We gave a way to detect unknown, applications. Accessing, work data. In. Tune will store that data for a couple of weeks for you that's. Just because, you have in tune if you. Have as your log analytics, it, used to also be known as operational. Management, suite and they. Can store it for up to a year depending, on what your subscription, level is this. Works in all enforcement, load. Levels. Right, so it's not just in a so-called audit, mode, you. Probably need to know this even when you're fully.
Deployed, The. People who do, mam management, might not be the same people who deploy applications and, so, when they go and do that if you haven't talked you've at least got another channel, to discover that application, giving, you confidence, in your deployment, so. You know when you're complete you, can actually go and turn it on and then detect, changes. Let. Me give you a demo of how you can use this whip learning. Oh. This. Is fun. I might, not be able to do this for you folks, wish. Me luck. In. Fact I can't all, right. There's. A great ignite demo that I did last year and you can go look it up on channel 9. All. Right. I'll. Just go to the slides that follow it, how about that so, it looks like this you go into the device. Health. Section. Of your OMS. Or as, your log analytics, and, you see that there's a blade here for, whip. App. Learning. If. You drill into that you can find the information that you need to copy into your. In. Tune app, list. And away. You go and over time you'll be able to see that, the, reports, of those not being in your policy, will go down and you'll be able to turn it on. Still. More. Automatic. Recovery. Your. End users are not the only ones to make mistakes if. You, click the wrong thing and revoke the wrong device that could lead to a lot of time. Loss. The. Fix is in for, 1709. We. Backup a key to, the users, account. So that when. They reenroll. Like. I'm going to have to do after this talk I get, access to all my data again. There's. A number of things that our, partners have done obviously. Office. 365. ProPlus. Supports, whip in, tune has made a number of enhancements over, the last, year. Supporting. The the man without enrollment. Giving. A one click, experience. For adding. Recommended. Applications, which I'll show you in a minute. And, now. I'm going to break it down for what has which. Support, so it's System Center Configuration Manager. If you, you, need at least 1706. To get that us be roaming setting that's, when they added the RMS.
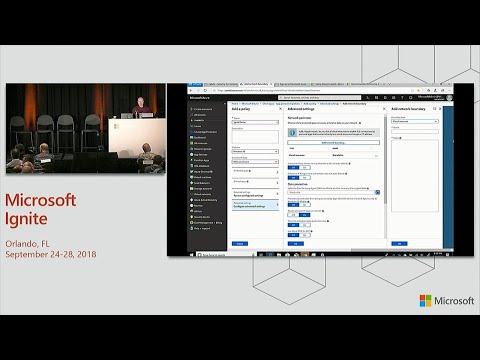
Support With. 1802. We now support whipped co-management. And. Now. With 1809, we have office, mitt. Label support and. See. We, did who we. Did why we, did what. Let's. Talk about how. So. Here I am in in tune and. Actually. Why don't I just start from the beginning so you can see how I got here within, in tune, there's the, client app protection. Section. If, my dots will finish racing. We. Set up our app protection, policies. Again. This is the same if you've already set this up for iOS, or Android this will look very familiar. Let's. Go ahead and add a policy. I'm. Gonna set my wife's and see how quick I can do this. All. Right stopwatch, started, ignite. Demo. So. Choose my platform, I want, Windows 10 I have. Choices here I could do without enrollment, that's the ma'am only experience, or I can do with enrollment say I'm doing it for an on-prem, and. Then I choose my protected, applications. All. Right I'm gonna go ahead and add applications. And. Here's. My recommended. Apps one-click. Option, boom, and, I get all the things that I showed you on that splat screen before including. Office, 365. So. I'm gonna go ahead and click OK. Validated. Cool. So. Now I've got a set of applications, that I'm gonna manage I could, exempt some I'm not gonna I'll skip that and let's go to the required settings as. Soon as I save off my list of applications. There's. Not very much beyond an app list that's actually strictly speaking required, I, need to set a policy I'm, gonna say silent, for now maybe I'm feeling a little timid and I just want to roll out quickly, I need. A corporate identity and then I see what's this say ah so, if I have any additional domains, I need to add them under. The network perimeter hmm. Ok that's. Very handy let, me go to that advanced. Configuration. Oh. That's. Interesting, cloud. Resources have, already been pre-populated. Look. At that in. Toon searches, the graph detects. All of the sharepoint online sites, for you and automatically, adds them to your policy so you don't have to think about that, but. I came in here to go and add the, other domains, that, I have. Protected. Identities. For so this, is my identity domains. I'll. Add contoso. Dot-com. Because, I have email that, comes in for contoso and. Let's say that I also have a company that I have bought say it was fabric ham. Dot-com. Maybe. You have more I'd I, know, that a lot of insurance companies end, up having a very long list of, subs. That. Might take you longer but for most companies it's pretty quick see. What else I have to do now. If I were just doing a cloud only experience, I might, be done now and that only took me. Even. With the dawdling at the beginning under, 3 minutes. But. Let's say that I want to do this for an on-prem, experience, and I want to actually set up my my network perimeter here's. A protip there's, a guy who's already done this he's the guy who's in networking and setup your VPN, configuration. He's already defined the corporate boundary for you so. First. I'm gonna set the DNS, names that are internal, this, is gonna be the thing that you, know we have the default configuration. Suffix. In in, when you go ipconfig. /all. Satis. You. Want those to be in here so. Let's. Say when I'm on Corp at contoso, I, get, this domain and maybe when. I'm on the. Fabric. Ham Network, I'm internal. Dot, fabric. Am. Calm. Alright. Now. I'm not really done I need to also define the IP address, ranges that should be associated. With that so, let me go ahead and do that. IP. V4. LAN. And. I'll. Just take this since. We're doing it as an example. Now. You might notice here if you are a networking person, that this includes a private domain range right. 192.168. Blah blah you. Probably have a router at home that's serving up addresses, like that why. Is it that I do that well, it is safe because we. Only. Consider, it work if it has an IP address in your range and that. IP address is bound to. One of your domain names so, when, you're on a 192, dot a thing. At work and it's bound to corp.contoso.com. Domain. Thing. For ipv6, but you get the idea, let's see you is there anything else I need to do up my proxy servers proxy. Servers indicate, things, that are leaving, your network so, you, can leave that range there and then that's basically the hole in your network I'll say I've got a proxy, I could. Do this with IP address, or I could do it by name. If there's, a this. Is a trick we've used in a couple of instances because this indicates that that's personal, if within. Your corporate network there's some place that you want to send out cat pictures or something like that it's it's, really strictly, for personal use you could list it as one of your proxies and then it would not be considered work data I.
Neutral. Resources. This. Deserves a moment. To, explain, so. When. You are in your browser and you. Need, to redirect to an identity provider if. That. Identity provider could be used for work or personal so for example, the secure token server from Microsoft, can serve up a Microsoft, account or. It could serve up an Azure Active Directory account, token. For you in the, middle of that redirect, you don't want the context, to change right. You're going to be going, to, a work site it redirects you to the identity provider which, redirects you back to the work site if that changed to personal that would be problematic. Right so, we. Created, this notion, of a neutral resource. And I talked long enough that Intune decided, that I had gone away. Well. It's thinking let me think you, know what I'm just gonna walk through one of the other examples so you don't have to wait through me copying, and pasting all that stuff over again in fact I could just use one of these ma'am examples, and. There's. The protected apps list, there's the exempt last there's, the required settings oh look the UI just changed, while we were sitting here that's how fast we deploy. There's. The Advanced Settings and I went through all the network stuff if. You're. Doing a mam setting, there's we, also do this kind of in a one-stop shop thing, where we include all of this information, about how you'll access, it setting pins and what not you can accept the defaults, there, you. Can also. It's. It's safe to choose, the defaults here so, IP. When. Is this called Enterprise proxy servers list is authoritative, what, that means to say don't. Consider, anything else as a proxy even, if you detect it I'd. Much rather that you detect a proxy that gets added to the local segment as external. So leave that in the off position. Enterprise, IP ranges, is authoritative, again, you've set a list of IP address, ranges, but. We could consider anything let's link local to you or if, you're on a domain joint machine.
The. Active Directory sites. And services can tell you whether something is, is work, or not and you can leverage, that if you leave this in the auto detect scenario. You. Might also want. To have a way, of restoring, that data without going. Resorting, to the user re-enrolling, right, if you get a device back you might want to have a, certificate. A. DRA, and if, you have EFS. You probably already have, a data recovery agent certificate. And you would just issue it here. You. Do want to revoke access to, data, on unenroll, that was what I showed you earlier we, give you an option to turn that off say you're migrating between two, MDM, solutions, you might want to do that but, leave it in the default I. Sometimes. Will change this so that I show in my demos, those little brown briefcases, if you don't like seeing them you can just leave this and then, this is the part that I really like is the azure RMS, for whip so. I. Just. Clicked this to on and that's how I get that USB, protection. That Rome's. Actually. You know I never, did do that demo, of showing. It actually working for somebody is if someone who's in a Microsoft, employee here. That, could, maybe try. To read a file off a USB stick you. All. Right, let. Me know if you can read that file. Alright. And while I'm at it I think, that. We're basically, done, oh I also suggest. That you keep the search, index or on because if you don't do that then outlook, can't search email it's kind of annoying, alright. And that's it, that's. How long it takes to set up ten. Minutes with. A bunch of blather bad. Connection. I think you can afford the time. The. Secm configuration. Is also very similar it's, just in that very familiar gunmetal, gray. Same. Settings, I can scroll through that list and that's what it looks like. If. You have SCCM. 1802. Then. This is where we actually allow, you to get off of SCCM. You. Slide this little toggle in the wizard, down. To the right and, now. You've got windows. Information, protection among other things. Were. You able to access the file not yet okay well we get, back to me. So. I showed you how to set up a policy but you actually have a lot of different, options here, so. Let me talk through a few of them because, maybe, you want to have a little guidance, and an advice about how, to get started and then how to ramp up I, like. The I call this the Quick Start if. All you want is the Selective wipe and you don't care to see all of those copy/paste. Errors this, is what you get all. Your apps still work there's. No copy/paste, block. Sharepoint. Onedrive, and. Outlook. All of those contents, are encrypted. On download, and. You. Get this protection. Of the USB stick. At. The same time you also get to learn I, didn't. Get to show you that but you, can actually see which applications are being used with work data. You. Also get the audit if you. Go and decrypt a file it'll, go into the audit log and. Data. Gets revoked when. You remove, the account either from the server side or on the client. How. Do you get that. Okay. Take. The recommended, apps good, experience. The.
Enforcement, Level is silent, and. Your. Network configuration is, practically. Automatic, you. Get the SharePoint online sites that. Are pre-populated, for you, and. If. You have a lot of email address domains, that are more than just your as your tenant, identity. You. Can add those. Include. Recommended, neutral. Sites there's only two on the list you can find those under, AKMs. Ford slash whip docks it's. Under the recommended, section on the left hands all right yeah the left hand side of the navigation. Turn. As your RMS protection, on, you. Don't need a template, this will allow anyone in your. Tenant. To be able to access that data and. For. The rest of it you can take defaults, with one caveat if you. Have not deployed at least 1703. I would highly recommend you have a Dra. Data. Recovery agent, because. The user when they you. Know turn it off and turn it on again it will have a whole lot of revoked data that you'll need to restore for them. Another. Option may, be you're past the point of doing just selective wipe and you want it at least have a little light enforcement. On your users, what. Could you get. Selected. Apps. Do. Prompt for disclosure. They. Just and the rest of them just work right. More. Of your data is will, be Auto encrypted. The, idea being you'll, add your line of business applications and, those and. Your LAN. Configuration. So that when you're downloading from, the local area network it's, getting protected. You. Get that default. Protection, on the USB copy. You. Can still audit as I, said before you, can also additionally, audit. Things, like an. Upload, to edge to. An on the corporate, site and you, get to audit, paste disclosures. Which are not available under, silent, because there aren't any paste prompts. And. Of course you get revoke. How. Do you configure that I. Take. All the allowed all. Of the recommended apps and put those in your allowed list and, now. You can add your line of business applications. You. Can you should explicitly deny, social. Media apps and. Then. This is a bit of a trick deny. The exemption. To any of your allowed, and denied, applications. Exemption. Supersedes. Allow so. Why would I do this because you're gonna exempt. Everything, else I call. This the exempt, star configuration, I, have a couple customers that do this so, they get that good experience. And they don't have to worry about app compat for the universe. Of applications, they don't know about and they're still getting the benefits. Of the copy/paste, restrictions. For. Office, etc etc etc you. Can. Do and allow overrides, so, if we're going that you know that there's the baby bear this the mama bear. It. For network you take it as the QuickStart and then add your land configuration. As I showed you, turn. On as your RMS and then again as the QuickStart for the rest of it. I'm. Gonna add an optional, item here it, might be that you don't want everything, that you download, from the local area network to be protected, and you, could even dial that back by.
Setting. The file. Types that you want to encrypt if there's only a few that you consider sensitive. Strict. Enforcement. There's. There may be some of you that want this. This. Would be where only your applications. Can, open work files and. Your. Corporate land locations, your cloud sites most. Of the data will be Auto encrypted. Basically. Most of the files in the users profile. You. Get encryption, on USB, of. Course and I suggest, that you would configure this in SCCM. Because it would be on-prem likely. Allow. The recommended, apps plus your line of business apps, and then exempt, only the things that you feel you need to for app compat reasons. Hide. Overrides, so this is the most strict you could get you could also do it with allow overrides, depending, on the group. The. Same network configuration, that you used for light. Enforcement, as your on and everything. Else is the quick start and then this is the juice because. Your on-prem you could deploy known folders, redirection. To onedrive, for business, everything. That goes into onedrive for business. Gets. Protected. You drop it in the folder it's automatically. Tected. All. Right a few more last deployment. Tips, and then we'll probably have time for questions here. Are a few real life lessons that we took when we deployed this at Microsoft, do. This gently start, in rings we, do this in Sophos where there's like the, feature team for, you would be maybe the I tease. In. A pilot, and then choose some Canaries, you know the next ring out that, are representative, of the departments, that you want to roll out to. This. Lets you experiment. With your policy, right, when you go home and you start your first ring which is you and your personal mission or your one, work machine. You. Can goof around in that policy when you feel comfortable with it spread it around. Also. You can like I showed you use that silent, approach to. Just get started. Because. It's very gentle you can, learn and grow as necessary, to add more enforcement over time I. Also. Highly, recommend that you deploy conditional. Access. You. Want to have some way of forcing people to actually have this policy on their machine before they get access to your data, this. Also helps mitigate third-party. Browsers, I didn't. Show this but one of those highlighted, tips in in tune is you should add app compat, without. App compat. Any. TLS. Connection from. An onion, on allow, dap Lakai ssin will be refused, because. The firewall doesn't usually have enough information to to, decide and will fail on the secure side app. Compat, lets you fail on the permissive, side so those applications. Like I know your. Your favorite browser that. Isn't. Allowed access. Needs. To still be able to say search Google Chrome or. Maybe. You want to go to and, even. A new safe that uses TLS, you want that to work so. With conditional, access we. Can actually restrict, that from, getting to, say, SharePoint, because, we're just not going to serve up a token to the unallowable. Onedrive for business like. I just talked, about in the strict enforcement you. Can use that folder, redirection to, have a stricter, enforcement because, more of your data will be automatically, protected. Everything. In onedrive for business gets, protected. You. Probably also want to audit this many, of you are going to have a security. Information and event monitoring. System. Or SIEM. So. Setup windows event forwarding for the WIPP audit events. You. Can also use this trick with Azure log analytics, or OMS. Alright, so, we did who we did why. We did what we did how now. We're up to when, when. You get home I want. You to be able to look at your auditor. In the eye and, say yes I took commercially. Reasonable efforts. To protect my data and I think it's worth the two minutes to get started, so get started protecting your data right away turn. On a basic policy at least then set up some groups make, your deployment, rings and start. Getting that data protected, I want. You to also know that there's lots of resources, for, getting this done right. There's, fast track there's. The customer acceleration. Team for larger companies you've, got a tsp, probably, consulting. Services, there's, your. Technical, Account Manager for many of your larger companies, the, ATS your, account technology, strategist. I'm. New, to Twitter so be gentle okay, but, I put my Twitter handle up there as well and. That's. How we can work together to have trust and, finish. Your ride in a, success, elevator together. There. Are a number of related sessions on nip. We. All got together on a Friday morning and I really, appreciate your time I hope. You. Can give me a good evaluation and. If it isn't well okay I might be looking for another job so give me a good evaluation.
All. Right and we're ready for questions I think. Sorry. I've one just on file, formats so. Look. I'm, looking, for you there you are hi did I promise, I'm not a Microsoft shield so. You're either slide earlier on and I've had the various different apps that were enlightened. Vizio. And Project weren't honest is it to do are. They not included, or they didn't fit on the slide, they, are actually not included. So. There, is we. Started off with the. You, know the the. Biggest apps that. You could. For. Now office. Is saying that the, ideal. Approach for that is just to exempt them and those. Files are probably coming in through onedrive for business anyway. So. That's the story right now there. Is an initiative though, to, meet that customer promise for more applications. And so over time I do expect that they will get enlightened but I don't have a timeline for you right now that's. Related. Question is is the protection, foil. Format, related or application, related so does it work in the web versions, and what if your PDF is not associated with if. Its associ with Acrobat which is a very common scenario right, it's it's application, based so. We, don't protect. Based off of the file format, we protect off of the context, where did it come from and. Potentially. Whether it was labeled or not so. I think labels, are currently. In the, main suite I don't think that they've been applied to. Visualize. That. Way as well but, I think that probably what you're gonna want to do right now is, to. Rely on onedrive. For business being, that place, where those video files are coming from and you have it protected there and, you. Can use exempt, for that I, would. Caution against. Doing the allow, you. May have you may run into app, compat issues because those older apps don't know what to not protect. Ya. Against. So you say onedrive for business I presume that until the chap on the line, yes. It does okay i sharepoint online is, actually the backing store for onedrive for business yeah. Thank, you great, over. Here so. I, understood, correctly if I have a unenlightened, app and it's it, saves off say a binary file or in a text-based file I can, set up the protection so those files get encrypted, right even. If they're not like were Excel, just straight binary or sorry. Repeat, the question about the offline part so oh no I mean if I have an unencrypted, app and it saves a, file, to the disk and it's in its binary or text non-microsoft I can have any it protect all those doesn't matter if it's a Microsoft. Document, or not can be any kind of document, yeah the protection, can be applied to anything okay actually yeah can the labels as well. Labels, are restricted, to at this point enlightened. Applications, which of, and by enlightened I mean nip aware, okay, which. Is the the main office suite Word Excel PowerPoint, I'm. Not sure about OneNote, but, definitely Word Excel PowerPoint and outlook our label. Aware, the. Windows, versions of those are gonna be in preview by the end of the year in the meantime what, you do is use. The AIP plug-in to classify, your documents, okay, and then the the one last thing is is there a way to prevent. A, safe. Protected document that is in a specific, location or labeled somehow from going to office 365 so it has to me has to be has. To stay on a work. System. Purpose. Being like if I have PCI. Data a credit credit card data in a file mm-hmm, I label. That as work data I want it encrypted, I went labeled I want, it to not go to a SharePoint, or onedrive because, I want it to stay on my on-prem. That's. An interesting scenario you'd. Effectively, have to say that that's not a work location, in order to prevent it from going there which would be a little weird wait, everything, and not just that but, I think that you might want to look at the office information protection, DLP. Scenarios, where. They can do things like scan a document in, an email or on point and apply new rules to it so they might be able to do something for you where if.
It Hits that you know threshold, number of. Credit. Card numbers or social security numbers or whatever you, can set up these rules to be custom but there's also a number of, pre-canned. Rules and they can do things like, apply. An RMS template so then only. The. People. That are allowed, to access that template could access that data even though it's in SharePoint, gotcha. Thank you over. Here I have a question about conditional. Access policies. Okay. I'm not a super expert on conditional access but I'll try now it's in combination with Windows, Information protection yes it can, all access policy, in place targeting, users and. The. Setting requires, the device to be compliant, correct. These, users have laptops, but. Some of them might. Want to work home, on their, own device, as well okay. But. Because of the conditional, access requiring. A device to be compliant, I, cannot. Use Windows information, protection on. The, manage devices. Okay. I actually, want, to solve that scenario we're. Not quite there yet, but I think it's possible. If. You, don't mind waiting a couple of minutes I'd like to get your contact info because. I want to use that as part of the discussion. With my partners around the, priority, of that scenario, it should, be possible but it's not right now and I'm, just gonna say sorry, but we're I think we we need to probably. Loop back with you great oh wait okay. Over. Here. Oh, now. He's pointing to you go ahead thank. You. One. Of the things that's. I'd. Be interested in is is cloud. App, security. Mm-hmm, engine there's a big you know informational, release about exact, match the, exact data match service it's. My understanding that, the engines, that evaluate, the DLP on have. Traditionally, been different, for a IP and, the cloud app security module. Is that correct of those engines still different, or will they consolidate. To this exact, data match engine. So that you can have one. Set of DLP, data to scan, and match again and trigger policies. I'm. Gonna be very honest with you I just don't know I'm not an expert on the EM cast side of things the extent that I've talked to the MKS people is that I'd like to I'd. Like to learn about what. Cloud. Applications. Are being allowed so, that we can maybe automatically. Put it in the policy, someday but, I actually don't know how they're doing there their technologies, the quick follow-up so you understand, that what I'm talking about that. That. There's this, whole side of the proxy world where you're trying to get into that flow and read DLP, to cut it there mmm-hmm and the way that this plays is it's trying to play off the device based on enlightened, applications, and things like that. The. World my organization, has went down as we've used the third-party vendor for a lot of years and the integration, is just horrible, but. We, and. We have those products we have DLP we have a proxy, solution. And now we've implemented a caddy to, get in front of all this data and there. Is this massive fight happening with it and some of it some of the questions that I have with it are answered with this presentation, but.
I Still see some conflict, in Microsoft, and the, big problem is is how does this get ahead of SAS like, I would love to switch from my third-party solution to something that Microsoft, is putting it at an API level on the system, to get in the front of things instead of a kludgy, third party but, I have to have that whole story made makes, sense to me in SAS is a big part of everybody's lies now you, know it's not just word and outlook that I have to protect against, its other requests from the organization, with with SAS applications. How do I get ahead of those other than always use a word document that has encryption on it, okay. I think this is great feedback. The. Good of Microsoft, is that we have a lot of technologies, the. Bad is that we have a lot of technologies, and. Trying. To put them together is. One of those things that we try to we. Try to make that seamless, we don't always get there but, we're always on that journey together so. I. Think, probably, we should follow up and see what we can do because. I probably need to sync up with my MCATs counterpart. Yeah. Boy. You got some good questions today, go, ahead right, do, you ever see whip being, used, in. Terms of segmentation instead. Of like a corporate, and personal, profile. On the same device separating. Development. From production, on the same device ooh. So. Honestly we don't we, don't really optimize, for the developer scenario, you can imagine that when, we are developing, a new application, we don't know about it in the policy, side right away so. It's kind of impossible to add it right. The. Thing to do there it'd probably be do. Do. That star exempt light enforcement. Mechanism. At best, I. I. Know that I actually exempt, my developers, from from policy, because of that. Maybe. We can have a better story in. The future but yeah. Right right now I wouldn't, I wouldn't, put that burden on someone who has to make an application run. Yeah. At, least that's what we've been doing. Okay. I think that's it thanks very much everyone.
2018-10-11 07:55



hi everyone ,if anyone else wants to learn about how to attract abundance and wealth try Sarparder Abundance Miracle Starter( search on google ) ? Ive heard some unbelievable things about it and my mate got excellent results with it.