CASB explained, and the stealth required to test it
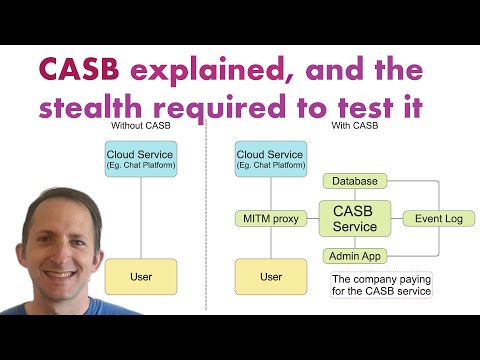
Hello, I'm Michael Mintz, and welcome to "CASB explained, and the stealth required to test it". So, this is going to combine two of the worlds that I'm in, which is the cybersecurity world, and the automation world. So, here's a simple diagram that explains what CASB is: So, without CASB, the user connects to a cloud service, and data is exchanged freely between them so that any data between the user and the cloud service is strictly between them.
Whereas with the CASB service, there's an MITM proxy, which stands for "Man-in-the-Middle", that basically intercepts all that data going back and forth between the two, and therefore the CASB service can process that data, put it inside a database, display it in an event log, and there's also usually an admin app where the CASB service can be configured. And this green part here is the CASB service and it usually belongs to the company paying for it, and the user is generally a member or employee of that particular company. So, "What is CASB?", and "What can CASB do?" So, CASB stands for "Cloud Access Security Broker". It's a software tool that monitors and enforces security policies for cloud applications.
CASBs can be deployed on premise or in the cloud. So, how does CASB work? So a CASB acts as an intermediary between cloud users and cloud service providers. It monitors all activity between users and cloud applications. It enforces an organization's security policies.
It provides visibility into cloud app activity. It helps organizations comply with cybersecurity regulations. And there are lots of benefits such as being able to control sensitive data, and being able to monitor and detect suspicious activity. So, this diagram should make a little more sense now. The CASB service basically comes in between the user and the cloud service, intercepting all the data, and then processing it, in summary. So, let's talk about CASB in the news! So recently, Tulsi Gabbard, the Director of National Intelligence for the United States, basically fired more than 100 intelligence officers from the CIA over messages that appeared in a chat tool.
And those discussions went beyond work to sexual themes and political messages. So basically, the CIA employees were doing things that they shouldn't have been doing, and they got fired for it. Here's another example in the news for that same story: "Tulsi cracks down on Deep State sex chat". So there you have that. And there's also another article in the New York Post: Tulsi Gabbard says she's firing more than 100 intel employees who took part in obscene sex chat rooms.
So, how did these employees get caught? Well, there was a CASB service between them and the chat platform that they were using, and all the data was intercepted, and it was basically configured so that if maybe people said something bad, that then, that data would appear in the event log, and then someone appointed by Tulsi Gabbard would probably go through the event log, and be like: Oh, wow, these employees were saying things they shouldn't have been saying, on company time. Very inappropriate stuff... So then, they could be fired for that particular behavior. So, that's just a quick example of how CASB works. So, CASB can catch bad employees in the act, just like that example there you saw in the news, and here's just a simple photo from a TV show called Mr. Robot, where bad employees might be up to no good. So, CASB can detect and monitor online activity, and that includes inappropriate online activity such as the reason for firing those CIA employees.
So, CASB can also fight crime. Here's a... just another stock photo, of perhaps a malicious actor about to do something bad. So CASB can prevent cybercrimes, cyberbullying, DDOS, hacking, data theft, data loss, and all those things, because you know hackers are out there, and hackers have to be stopped from doing the malicious activities that they intend on doing. So, CASB also helps schools... So, CASB can prevent students from cheating in class or on exams, for instance, if a student was trying to use ChatGPT in order to do their homework for them, then the CASB service would be able to intercept that, and then the teacher would be able to see that the student was cheating.
It'll also prevent students from visiting inappropriate websites, such as porn sites while they're at school, and also maybe prevent them from playing computer games on school computer labs when they should be studying for their exams or doing homework. So yes, it will prevent students from doing things that they shouldn't be doing. So, CASB can also save lives. So for instance, CASB can prevent: planned attacks, terrorist attacks, school shootings, and self-inflicted harm, and by self-inflicted harm, perhaps a student is researching ways to harm him or herself, and therefore, those keywords would appear inside the event log, and then the teacher would be able to identify students with problems and then maybe do something before it's too late. Another stock photo of a hacker.
So, where does one get CASB? Well, the market leader in the space is a company called iboss, which provides CASB, as well as a lot of other powerful cybersecurity services such as ZTNA, SWG, SD-WAN, Browser Isolation, etc, which basically allows organizations to secure their data. And iboss is trusted by lots of organizations worldwide, such as ADP, Verizon, and Comcast. And also, schools use iboss in order to secure internet access for their students and their staff. So, schools might use iboss in order to install CASB on students Chromebooks so that students can be prevented from cheating or also catch students that may be planning malicious activities.
And here's just a huge overview of all the various things that are provided with the educational package that iboss provides. Basically, you can monitor students activities when they go to YouTube, and there's also classroom management, a parent portal, just various ways of enforcing safe policies on students Chromebooks. And of course there's also the government category, where there's lots of various services that iboss can provide to governments. So, a little about me: I'm Michael Mintz, and I created the SeleniumBase framework.
And I also lead the automation team at iboss. Nice photo of me there. Here's a photo of me on the job. And here's another great action shot. And here's a fun fact: My wife and I once got to meet Tulsi Gabbard at a house party.
And this combines the cybersecurity worlds cuz I work in cybersecurity and Tulsi Gabbard is the Director of National Intelligence. So, cybersecurity people meet, without even knowing it. Closeup, of that. So now, let's talk about configuring CASB.
So, depending on the service provider that you're using, there's probably going to be a menu with advanced controls where you can configure various things. So, for instance, with iboss, there might be a security policies tab where you can set Resource Policies, Routed Policies, (you know), maybe set Web Categories to block certain categories from Chromebooks, etc. You could set Allow Lists, Block Lists, etc, so that maybe you don't want certain sites to be allowed at all, or maybe you do want to always allow certain sites.
You can set Policy Layers. There's a YouTube Manager. You can set Keywords. There's just lots of different settings that can be configured in order to fully configure the CASB service. So, for instance, there might be a GenAI chat protection switch so that you can basically prevent data loss prevention, and other things from happening when an employee is using ChatGPT for a query.
So, for instance, that is part of the ChatGPT Risk Module that iboss provides, where it can monitor ChatGPT interactions and also detect risky behavior and block activity and monitor and report all that to administrators. So, for instance, in this example here, a user tried to input email addresses into ChatGPT, but due to the CASB service setting that was set via iboss, you'll see that an error occurred because it detected that email addresses were in the message and therefore it was going to block the content directly. So, once content is blocked or maybe something is filtered there's going to be an incident report and there's going to be an Incidents tab that you can check on where administrators can go in and see what exactly was blocked or reported on and triggered. So, for instance here, incidents were triggered via an AI Risk incident because someone was sending data into ChatGPT that they shouldn't have been sending. And here you can see it contained email addresses, and you can click in to get more details, but essentially, this thorough report is generated, and then this basically provides important details so that people can take action.
So here's a more detailed view of a specific incident, where you can see all the various details that occurred. And you can go in, you can see email addresses that came in, IP addresses involved, the time when things occurred, etc. You can see that it'll show the vendor as ChatGPT. It'll show the username, and the trigger message, which includes the email addresses that tried to be sent, but then were blocked. So this is exactly- probably the case of what happened with the NSA, where Tulsi Gabbard fired intelligence officers because there was probably an event triggered when people were using inappropriate language inside their chat tool, and then those messages all appeared in an incident report, and then via the incident report, an administrator could go in and see- okay, these people are taking part in something that they shouldn't be on company time, and therefore Tulsi Gabbard came in and fired those employees.
So that's all part of the Alerting, Auditing, Logging, and Reporting feature of iboss. So essentially, any business, government, school, etc, can have access to all these different features such as the ChatGPT Risk Module that was described earlier. There's also plenty of other different capabilities that you have such as Detailed Logging and Reporting, Risk and Threat Reports, Digital Experience Management, etc. There's a lot of different tools that are available to customers. So that all comes back to this diagram that I showed you earlier, where the CASB service essentially comes in, connects between the user and the cloud service to intercept all the data, and then, all that data can be processed, in the database, and get sent to the event log so that the system administrator can view the data and take appropriate actions as necessary. And of course, there's going to be an admin app where everything is going to be configured, and there'll be lots of switches where you can (you know) turn something on, disable this feature, turn on this feature, different tabs where you can set different settings, etc, so, it's a very powerful tool.
So now, let's talk about automating CASB testing. So, as you saw before in the diagram, there are cloud services out there, such as chat platforms. And sometimes, testing is going to occur with real cloud services such as ChatGPT. So, these cloud services can include: search engines, email platforms, AI chat platforms, streaming platforms, etc. And many cloud services are protected by anti-bot services, making test automation tricky because the test automation would possibly get blocked unless it was modified to get around the anti-bot defenses. So, in order to fully test CASB, it may be necessary to bypass the anti-bot services that are there so that automated testing can work accordingly.
And that's how I personally got involved with making automation stealthy. And that's also called "anti-bot bypass" to make your automation get through so that you can access websites without being restricted. So, here's the test automation framework that I built: It's called "SeleniumBase". You can find it on GitHub. And, basically, the description as it shows here: "Python APIs for web automation, testing, and bypassing bot detection."
And as you can see here, there are a lot of GitHub Stars, so it's quite a popular tool. So, SeleniumBase already has over 25 million downloads from PyPI, which is the Python Packaging Index where people go in order to download Python packages. So here's a view of SeleniumBase from the GitHub page directly: You can see all the data and details for it such as: Stars, Forks, number of people watching, the number of tags, etc. And if you scroll down from there, you'll see a powerful ReadMe with lots of details and tools that SeleniumBase provides such as (you know) a recorder for instantly generating your tests, or a dashboard so you can view test results, but more importantly, since we're about to cover anti-bot bypass, there are two special modes called: UC Mode and CDP Mode, which are used to provide stealth. So with UC Mode, that allows bots to appear human, which lets them evade detection from anti-bot services that try to block them or trigger CAPTCHAs on various websites.
And I have a few different YouTube videos about that. And the successor to UC Mode is CDP Mode, and that's a special mode inside of UC Mode that lets bots appear human while controlling the browser with the CDP Driver. And CDP stands for the "Chrome Devtools Protocol".
Now, although regular UC Mode can't perform WebDriver actions while the driver is disconnected from the browser, the CDP Driver can because it's using the Chrome Devtools Protocol in order to perform the various actions such as: typing text into text fields, and clicking buttons while remaining undetected. Alright, it's live demo time! So let's back out of that and go over to here, where there's a lot of SeleniumBase examples in the CDP Mode folder. So, for instance, if I want to have a test that queries ChatGPT, I'm going to run a simple test: `python raw_chatgpt.py`,
and I'm going to run that. It's going to go in to the ChatGPT website, and it's going to type in a query: "Compare Playwright to SeleniumBase in under 178 words", and then it's going to grab the results there, and then print that out to the console when it's done, like here. So this is just an example of an automated test going into a website and grabbing data where normally there's anti-bot protection.
So the same can be done with a Google website. So, for instance, if we type: "python raw_google.py" from the SeleniumBase examples folder, we're going to do a Google search.
You can see here it's searching for SeleniumBase, and going into the SeleniumBase GitHub page. Now, you might not realize that SeleniumBase is bypassing bot-detection unless I turn off the stealth ability. So let's go into the script and make a modification. Going to open "raw_google.py", and I'm going to remove the part that says: `uc=True`, and now I'm going to run the script again so you can see exactly what happens when you're not trying to use stealth mode to bypass bot-detection. So let's do: "python raw_google.py",
we're going to go into Google, and immediately, you can see that you're getting a reCAPTCHA appearing because the system detected unusual traffic from the computer. So, this is an example showing that if you don't have the SeleniumBase stealth mode enabled, then you will get blocked by Google, or any other websites that try to block standard automation. So I'm going to put the `uc=True` right back here, and then I'm going to run the script: "python raw_google.py", and this time, since I put it back, I am now able to do the Google search and go straight to the GitHub page. You can see that the "raw_google" example worked. So, this is just one of many examples where we're bypassing bot-detection so that test automation can properly go in- to the cloud service, and get the data, and that's just one component of testing CASB, because if there's a cloud service involved, you need to be able to bypass that bot-detection so that you can thoroughly test the CASB platform.
So that is that, and let's jump right back in to the presentation that we had. So let's go back and click... So in conclusion, CASB is powerful, and it needs to be carefully tested, because if you have the government using your software as a paying customer, then you had better be certain that your software works well, because if the government isn't satisfied with the results, then you'll be in the hot seat... just like Zelenskyy is here... being grilled by Trump because he didn't accept the deal that he was offered.
And I certainly don't want to be in that tough situation. That's why I got to make sure I have 100% test coverage, or else it'll be me in that hot seat! So that concludes this presentation. Visit iboss for CASB, and all the other cybersecurity services that you may need, such as: ZTNA, SWG, SD-WAN, Browser Isolation, etc.
There's a larger list here. For instance with "Security, Authorization & Access Controls" you've got Malware Defense, you've got Data Loss Prevention, you've got Browser Isolation, Device Posture Checks, SSL Decryption, etc, there's just so many different capabilities that are extremely important for businesses, governments, schools, etc, in order to safely and properly secure the data that you have, and basically make everything secure for your users, your customers, and everyone else involved. And also, be sure to visit SeleniumBase on GitHub for all your web automation needs, and it's quite popular, and there's a lot of documentation in the ReadMe, so be sure to check all that out. And I'll see you all next time!
2025-03-23 15:29


