Webinar Biometrics in the Physical Channel
Good morning, everyone. This, is Travis Hoban CTO, at FTS I would. Like to welcome everybody who's. Joining. Our webinar on biometrics, in the physical channel. We'll, start here shortly. Give, everybody about 30 seconds, to join as. I see more attendees, joining every second here. The, agenda for the webinar today, is all. They give, a little bit of a lay of the land where. We're at in the biometric space, and financial. Services. A. Little bit of background on biometrics. A rat, today and where we're going. Then, at that point I'll, give, a little bit of time to some of our partners. David. Ershon sin with ida Mia and Andrew. Soto at Hyosung. David. Will be touching briefly on. What's. Available today, in the, space, of access. Control and biometrics. And access control for in. Branch FTE and Andrew will be touching on. Authentication. Biometric, authentication at, the ATMs nit. M's and what's available. Alright well let's go ahead and get started with the poll. I wanted to ask a couple questions just, to get. The wheels turning. Give, us an idea of how you feel about biometrics. Is is it, an effective tool for, your financial institution implement. Something. You. Think would be effective. For your specific, institution. Couple follow-up questions here. You. Share, the results. So about 2/3 of you are, interested, in biometrics, and think it would be good a good, tool. Nobody, said no I like to see that that's interesting. I. Think in general that's what we're seeing in the industry today is. Some. People are excited, and interested some, people are a little bit skeptical but everybody knows that perhaps, it's the future, it's. Very, interesting to see that let's, go on to the next question. You. Just, curious, who has it in who has any form of biometrics, in place right now for access, control so. Not necessarily, authenticating. Members or kin or customers. At. Your, branches or ATMs etc, but rather you're, in branch FTE or your. Corporate. FTE. You. Drum, roll please. Okay. About. A fifth of you have, something, in place and. The. Vast, majority do not 78%. Very interesting, I would. Be curious to have some conversations, with those who do have it in place where, they have an inflation and, how they've implemented, that. Thank, you for sharing, next. Question. For. Those of you who have not or, even for those who have. What were some of the hurdles or what are some of the hurdles. That, are standing in the way of you implementing, it or were, a challenge when you did. You. Privacy. Cost. Consistency. And. Difficulty. In implementing that, consistency. Throughout channels, that is a huge hurdle. Andrew. Soto is going to touch a little bit on on that and how we integrate. Biometrics. Into our current channels. Interesting. To see that that's the largest largest. Hurdle in the mind of of our partner financial, institutions. I would have thought that maybe privacy, or, something. Along those lines privacy, security might have been a concern but, very. Interesting okay, well thank you for sharing hopefully that gets kind, of greases. The wheels a little bit and gets the juices. Flow and the ideas going.
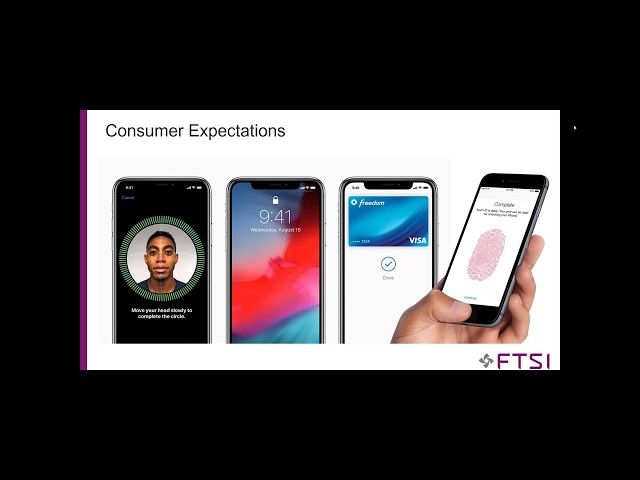
Obviously. There's, a lot that is happening, right now in, the world of. Technology. That is moving. Biometrics. Forward, oh, do. We have. Okay thank you. Biometrics. Is not new actually. If we. Go back all the way to, the. 1900s, the first form of biometrics so to speak was the fingerprint, and. How. That was then used to. Identify. Individuals. And. Then. In the 1970s. From a technologically. Or a digital, standpoint, digital biometrics. The. First form was in, the 70s with voice. Recognition software. That was deployed. By the government, in, surveillance. And such and, an. Authentication of. Individuals. Who were, sending. Receiving messages but. Today. The, reason biometrics. Has really, jumped to the forefront is because. It's. In the palm of. Every. Individual, now pardon the pun I guess but. As consumers. Become, more comfortable with, using. Face ID or, touch ID on their. Android, or Apple devices. They. Begin to expect that same. Frictionless. Experience and. Perceived. Security. That comes with those. Devices and, that technology, and so. We we start to see it in different realms how its translated to the financial, space is interesting, it's it's come into the financial space in several different areas. Next, slide please. Obviously. I think what. We're most familiar with is in the mobile wallet space I'm not going to touch on these a lot a lot. Because I think we want to get to the real meat potatoes of what's available. Right now for our. Partner. Financial, institutions, but obviously, mobile wallets banking, apps. Digital. Insight is using, in their, mobile banking app. Essentially. By vein scanning, in order, to authenticate. Instead. Of face ID and I'm going to touch on the reasons why but. It's. More secure in. Call centers and also. Interestingly. This. Is starting to become more mainstream in, our homes and such as. We. Start to. Be. Recognized, by our voices by our devices, in our homes such. As Alexa, or our Siri, and, as. We move into that. Voice recognition in, our homes the. Ability for our members. And customers, to be able to do. Their banking via. Internet. Of Things or smart devices in their homes, such. As Alexa. Transfer, a hundred. Dollars to my savings, or something along those lines. Point-of-sale. There. Are several. Companies. Out there right now that are pioneering. Facial. Recognition at. The point-of-sale so. That, consumers. Will, be able to put, everything into their basket. Scan, it as they go pay. For it and then walk out of the store without. Having, to interact, with anyone or even. Have. Those items scanned, and then pay for it as they walk out of the store with their, facial recognition, with. The facial recognition software, that's in place of these retail institutions, and where, we'll see this in banking is when members or customers walk into the branch they. Will be, authenticated. Through. Their facial recognition through. Their facial biometrics. And, branch. FTE will know who they are will be able to greet them as they walk up to a counter, or a pod a teller pod or something like that and. Be able to. Transact. Without, needing. To provide any forms of. Additional authentication at. The ATM space Andrew, with Hyosung is, specifically. Going to talk about this and, palm vein. There. Are also. Various. Types of ATMs. Out there more. Popular in the Asian space right now but in Asian, countries but you, have a. Facial. Recognition, that. Is being utilized to, authenticate. At the ATM, you, also have. Use. Of biometrics. Such as fingerprint, at the ATM. At. This point I'm going to talk a little bit more about this but at this point most. Authentication. Biometric. Authentication at the ATM is taking place with two-factor, authentication so. For example those ATMs that are using fake or facial recognition, or. Facial biometrics, to authenticate. Are also requiring a pin after or. Those. That are using a fingerprint, are using. A, card. With, a. Fingerprint. Sensitivity. That can scan your fingerprint, so there's some interesting things happening out there but. It's. Important, for us to, be. Careful what biometric, authentication, we, implement, at our financial, institutions let, me share a few examples of some of the security concerns out there right now. You. So. When we look at some, of the most common. Commonplace. Authentication. That's out there right now that consumers, are comfortable, with and even. That we might be using on our mobile apps. There, are some serious, security concerns out there so in. One, famous example a. German. Hacker was. Able to take, a high-resolution. Photo offline. That. Was available online pull, that online and create.
A, Black-and-white. Rendering, of the. Thumbprint. Of the. German, Minister. Of Defense. It, was then able to use that thumb print rendering, tube and a, 3d printer to print out a, 3d. Version. Of that thumbprint and then. Access. The, German. Minister. Because this, iPhone. It's, it's, interesting, that we use our, thumbprint, for so many transactions. Or. Via. Point-of-sale. Or in, the, financial, services, space, in. Banking, and such through mobile apps yet, with. The right tools that are all readily, available on, Amazon such as a 3d printer and play-doh or. Or. Dental. Dental. Impression. Glue you. Can create a fake fingerprint, in about five minutes and access somebody's I phone which then of course there. Is a lot that you can do once you get on there that's just one example but, it really highlights, the importance. Of choosing the right. The. Right form. Of biometrics. So I'll share another example, we. Think that maybe we've come a long way with face ID, that. Perhaps that's more secure. Yet. It's been shown multiple, times over and over again and you get this YouTube video this. That. You can easily access. Apple's, facial, recognition or, sorry. Face ID. Essentially. Hacked their face ID through these sub masks, 3d, printed masks, and infrared. Printed. Pictures. Of eyeballs, very. Interesting. What you can do in access so just, wanted to highlight the importance, of choosing. The right partner, and the. Right vendor and the, right technology. And. It really makes you think, what are we allowing our members, and customers to do via their phones. And. How. Do we get to where we need to be to feel, like, we are secure, in that transactions. That. We're comfortable with the transactions, that are occurring, there, I do want to share a little bit of where biometrics. Might be going. The origin. Of what. We'll call behavioral biometrics. And that's the next step in biometrics is actually. The, time from, the time of the Telegraph so, during. World War 2 the Allied forces would. Authenticate. That, message is sent via telegram, a telegraph. Were. Actually. Sent by the operator. Of the Telegraph that they that. They were told it was being sent from and the reason they was the way that they would verify this is there. Was a specific cadence that, that. These telegraph. Operators. Would utilize of the, debt which is in the dot the. Dots and the lines and the dashes and they, could know basically. By analyzing. The. Actual, incoming, message that. The person sending it was the person that they expected. To be sending it and how, we see that this. Is just one common example how we see that being, played out today is.
With. Behavioral, biometrics, it's not necessarily, just what you do so. For example in the, instance. Of, logging. Into your your, mobile, phone it's, not just that you put in a password or, it's not just that you push. On the you. Know the little button that authenticates. Your your. Fingerprint. It's how you do it so, how much pressure you use the. Cadence with which you do it maybe the cadence with which you put in a pin into. The phone how. You swipe your hand so, that. Is potentially. The future of biometric. So. Essentially. Adding, in a second, form of authentication. Or, basically. Implicit. Two-factor, authentication not. Only in what you enter or what you do but how you do it how you hold the phone and cetera so that's that's, potentially where biometrics. Is going again. I just want to delay a little bit of a land here. And now what, we're going to do is move into. What. Are a, couple examples of. Technology. That is available today. Through. Through. Some of our partner. Technology. Companies we're, going to have Dave darshan and as I mentioned talk. A little bit about access control, and then we'll move on to Andrew. Sotto who we'll talk about what's available at, the ATM, today, what. You could implement as far as member or customer, authentication so, Dave, go ahead we'll. Turn, it over to you take it away. Morning. Good afternoon everybody. Travis, if you could move to the next slide and get off my ugly picture, there. Thank, you I'm with idem iam we. Are largest. Fingerprint. Biometric. Provider, in the world we've been doing this well over 40 years. Captured, over 4 billion fingerprints. Now let me first explain that, my. Division does access control but a very large portion of our company about 70%. Does, law, enforcement, background check, type fingerprints, tones in the APHIS world AFIS automatic. Fingerprint. Identification systems. There. You can see that we have 60% of, state law enforcement systems, government, agencies worldwide, and, there are a couple the awards that we won by Frost & Sullivan an. Independent, group, that does surveys not just in, security. Industry but other, next. Slide please. I. Wanted. I always like to give an idea that we are not just in the, security, market and where, other areas, that the biometrics, are used first, of course the FBI that, certainly is in that out of the division I mentioned, the. FBI was actually our first commercial, customer, I like, to say we were CSI, before CSI, was cool we. Invented all that stuff but, in other you know verticals, in, our division, Chronos. Is a name that some, of you may know you may actually use it in your facilities, the largest time and attendance clock provider in the world they. Take a little biometric, module, and, integrate into their clock to. Date they buy probably over 40,000. Modules from us a year and over, 65% of the clocks they sell have a biometric. 24-hour. Fitness some, of you on the call may be members there if, you are that's, our biometric check-in, system you're using there they. Had a tremendous fraud problem with people just using cards handing, it to friends. Whatever. To. Get in the car to get into the clubs. They've. Implemented our system over ten, years four and a half million people, involved. For. Cardless check-in all, trust networks is a third-party partner of ours they. Provide a check cashing solution, for, their customers, is verify using the biometric, saves. Time and obviously a higher. Security, and, verification, process and, then Morse watchman's, is a company, that makes a biometric, enabled, lock key. Cabinet and it's, not just to open the, key cabinet with, your fingerprint, it's also for. The user to take out keys at a particular time to return them and such if, you can think of a car dealership somebody. Taking a key out knowing who's taking it and when it's brought back next.
Slide Please. Okay. Why, use biometrics, many. Of you might. Be using card access for. Your facilities, it is, it's actually probably close to 30 year old technology right, now as we, like to say it only proves the credential, is present not the individual. Biometric. Certainly, provide a higher security, for, the provider and convenience. For the user and that weighing. Of security, versus, convenience, I'll speak of a little, bit later eliminates. The cost of management replacing, lost and stolen cards, this. Is certainly a very large example, but, I can tell you the 24 hour fitness, in the first 18 months of implementing our or. Biometric, and replacing, cards saved, over a million dollars in card and printing costs now. Certainly my 20 years in this industry the number one objection, to. Using fingerprint, biometrics is, the public's perception towards the use of fingerprint, Travers, has already pointed out the. Fact that the, the, public's perception of using a biometric on a daily, basis, has, improved with, the iPhone with, something, you know like like, 24-hour fitness so there certainly is a growing trend of biometric, acceptance, and as, my director likes to say. Millennials, they, haven't grown up like an, older person like myself thinking. Fingerprints, for all in for bad guys, next. Slide please. I always, like to touch on the privacy, issue of using, fingerprint, biometrics because. Somewhere in, either. Selling, it a marking, it or you, know offering it to your employees, it, is important, to show, how, it actually works, and so the, first image. Obviously is a live image capture of a fingerprint, we, look for what are known as minutiae, reference, points they, are splits, and ridges, clusters. Bifurcations. We call and it's. Just a minutiae map it's basically triangulated. Turns, it on an algorithm score, and that's, what is stored in. Our readers it is not a back-end server, transaction. Everything is stored locally in, in our reader the most important, thing to take away from this slide meant. To tell your, employees or anyone, is that what, we store in our readers is totally, proprietary. To our readers only cannot. Be re-engineered or manufactured. Into a fingerprint, image that. Can be used in any other type of system in the world and I, can say that with fairly strong conviction, because I mentioned we, are the largest provider of those other types of systems a, physicians. For background inside next.
Slide Please. Show, you briefly our product, line. Any. Of these readers, essentially. Could replace, your, existing card, reader the, same wiring and such they. Work with your current access control system that does your scheduling, for your, employees to get into your facility or employees, to get behind the total line or whatever but. Just some brief. Capabilities. Of it they, can store. Up to a hundred thousand users they, can be used outdoors in, any, kind of environment, you. Can do card, and finger, if you want to do to form verification. And still, utilize your current, card system, it, does have fake finger detection, against no fake facsimile. Of latex or something on those lines there's. A tamper switch if, this thing if the if the reader is pulled off of the wall it, will automatically. Destroy. All the templates stored, on the reader it doesn't destroy the reader you can reload, it when you put it back on the wall but, there's just some of the features we've, included into. The reader next. Slide please. You could start the video. This, is a company video that. Shows. Our latest. Technology, we came out with about two years ago we. Called our Morpho wave technology. This. Is touchless, fingerprint. Technology. They. Could had a little hiccup there as. You can see this is an implementation in, a car parking lot just wave. Your hand through this guided area it's. Picking, up one of four scan fingers, in less than a second sending. The signal on to the access control system which, then in turn lifts, the gate. So, the reader itself it can be mounted either on a wall, or on, a pedestal in front of a doorway, or a, turnstile. Of some sort, so. You can see it's actually scanning, four fingers with, a 3d, camera and. Basically. Reads the first finger if it doesn't match there it moves right down the line, you. Can up, let me stop here this was the first implementation, of the technology, two years ago we called it our tower device. Reader. You'll see we came out with in April is the compact, which. Is much salt smaller in size, let's. Cost and can, be mounted on the wall. Believe, it now continue, to show you just some implementations. How it can be used. Standard. Off a store. Go. Show. Some, gym applications, of restaurants, eating areas. This. Reader has all the same functions, as our standard readers as you can see it can do card and finger or. Finger only your choice it. Works with any access control system in the same manner as our standard readers. This, is a unique feature, these. Will actually read a QR. Code. So. If you have a visitor, management. System so. Share with your facility. Pass. These out would. Not have to go through the, enrollment process of. Enrolling. A visitor. Into your system. These. Are some of my colleagues from over in France action. Next, slide please. Just. Touch on the technology, very quickly as, I mentioned it's a three-dimensional. Video camera. The, most important, thing to point out is if you look on the lower right okay you'll, see what. Is a standard, with it what's captured on a standard, tactile, placement of a fingerprint, in the middle is what are more, for wave reader. Captures, and then, on the on the right is a rolled fingerprint, say from an. Athiest type system, the key here is that the morpha wave actually captures, more information. Than, the tactile placement, why is that key it's, providing, more information that provide a guarantee. Of a faster. Excuse. Me faster verification. Okay we, feel this technology, is the. Best combination of, security. Accuracy. Speed. And high, throughput if you have, points. Where people go through. In. One. Period of time. Next, time. Just, briefly this is a, implementation. Of the the, Morpho towers at a Citibank. Call, center down in Tampa it was one of our first implementations.
Seeing. The photo they actually have it for entry. And exit. Next. Please. On. Do you Andrew thank. You. Thank. You, my. Name is Andrew Soto and I'm with, Hyosung. I'm the FI channel manager, here at heel Sun I will. Be introducing, palm vein scanning, a new, way to authenticate yourself at the ATM without, the use of a carbon pin I. Have. Three simple, slides to go over with you that go over the background, features, and where he'll sign is that stay with palm vein scanning. Today's. Today's, banking consumer, you, know they expect their branch experience to be fast personalized, and more, secure than ever been before. Financial. Institutions need to increase the measures to combat, fraud without hampering or delaying service Hyosung, uses the latest biometric. Technology, to help banks and credit unions mitigate. Fraud while, reducing transaction, times and enhancing the branch experience. Because. Customer, remember simply scans the palm to verify their identity authentication, occurs, instantly, and the consumer, the, customer remember, can be continued, with their transaction, without the need to confirm any other forms of identification. The, palm scanners use invisible, and harmless infrared, light to detect blood flowing through, the veins pattern. Of veins is set to life before a person is even born by. 14 weeks in a mother's room the vein, pattern is created this pattern is very unique even, more unique than a fingerprint. Identical. Twins who may have similar. Though. Not precisely, matching, fingerprints, can have. Completely different palm vein patterns. This. Is that. This is new to the US but not not a rounded. Around the world, there's. A the. First Bank in Japan actually introduced. This for not. Not the reason we're all thinking we think palm vein is is really, out there to make, it you know transactions, more you. Know quicker and faster or. It was actually introduced in 2012, in Japan due to a third, quake and tsunami that hit many. Of their customers. Lost their usual identification, documents, in the, natural disaster, so the, bank's sought out, to. Establish a more reliable link between customers, in their accounts via biometrics, so. Originally. Wasn't you know for efficiency, or security, it was you know they lost their identification, but now once. You know it was a proven case it's a proven case for security. And and a, more. Efficient way to authenticate yourself without the use, of card and PIN so, um. Molly, neck slices, so. Let's get into the key benefits of the. Palm. Vein scanners at the at our ATMs, so. Talk about the accuracy we did we had 10 registrants, do a do. Around a 100, test, 94, were successful, with outreach without having to retry prepare. We also looked at a facial, recognition and, it's about a medium, accuracy rate I, might. You know facial recognition might, not work well due to the, poor lighting conditions or maybe, you're wearing sunglasses or, other, objects, that may cover your face so and. You. Know the face also changes over times over. Time veins typically, are stable. Throughout your lifespan so it's very accurate form of biometric. Read reading. Palm. Green is is, for everybody it, is 100%, in rollable you. Have around two, to four percent of the world's population that cannot. Participate in fingerprint, scanning due to skin, defects or missing limbs or any. Of that, well as long as you have a visible, patch of skin with being behind it you're, able to enroll, that into the. Into. The server so for. Instance if you're missing a hand you can use your elbow or, cheek. Or forehead so. It's, 110, rollable. It's. A we're, seeing it's, very. Convenient, it is it. Is reducing transaction, authentication, time by 93%. Which. Can, take down the overall transaction time down to 15, seconds 5, 15 seconds. Once. The once a u.s. moved into using. EMV chip cards, we saw that transaction, times are doubling in time so, there's. There some instances, where your your card has a bad, chip and you have to use. It one two maybe, three times the, Machine, to ask you to swipe so bit. You're, using UV chips is really delaying transaction, time palm vein scanning, is. Is reducing, that time by 93% so it's very very convenient fast. So, last but not least let's talk about the security behind palm vein scanning. The, digital, signature that your palm treats, contains, up to 3000 digits for, comparison, the fingerprint, usually is. Usually matched based, on an 8 to 16, point of similarities. So, the. The bank has has. A ton of different reference. Points I believe this at, three thousand digits so, next. Night please. So. To find out where Joe Singh is today with Palm brain scanning we have. We. Have the hardware, available for, purchase on all of our BranchCache mission equipment so you're through.
The Wall drive ups you're through all walk ups your Lobby units, anything. That I. Can. Be I guess. Your IP M type. Of ATM can can, be integrated with a palm vein scanner. If. You currently have. Branch. Transmission, equipment it will be it. Will be a filled up field. Upgradeable, so. You can order the parts and upgrade in the field. And. We, all the, palm. Brain will be. Managed. By a professional services, team who, is the most, experienced, core of integration, team in industry, they. Can typically finish a palm. Vein integration. And around 60 days. Certification. Is going. To be cut required by the core, processors, HM networks, we. Have a few that are in process today the, plan. Is to certify, palm. Vein at these, select, cores this. Month in next, month which, is April 2009, team so. We're very excited you, can run this out we actually have up. To credit unions today that are piloting, in the beta tester, for palm. Vein so we should have again. All this wrapped up and tested with a certain, amount of cores and the, march/april, timeframe. There's. Me that will very soon. I. Believe that, is all I have to say I hope. This information I shared with you was valuable. Please. Feel free to reach out to at the aside from, information, on palm vein scanning, as well as the access control, I. Will go ahead and pass it back to Travis, to open, this back up to some q and A's thank. You. Hey. Thanks David Nana appreciate, it we'll, try to close, here quickly a couple questions that, were. Sent in in advance. Can. Any of your devices, be compromised, in any way David. Let's have you answer that, I'll. Address it quickly and in2, from. From two sides number. One for, the template in the reader okay the actual fingerprints, stored the. Templates in the reader are, stored. With 128, AES, encryption on. The contactless, reader it's 256. ATS. So. That's. How, would rest me regarding any any hacking or such I've already talked about you know it's impossible to really recreate the template for use anywhere else um the, other is the presentation, at the reader of. A fingerprint, and, very. Common question in the 20 years I've been doing this is what, happens if it's presented, with a severed digit okay. We. Have fake, finger detection, we do not have live finger detection, nobody, really does yet, I. Think, it's certainly a fingerprint but, if. It's. Probably, a freshly, severed digit, and. Warm and fuzzy it may work but this is where I want to bring up the, weighing of security, versus convenience, okay if, security, outweighs. Convenience. Okay, this is where I think you would enter into using. To form verification, of the card and the finger because you may have one but you don't have that card you don't have that pin. Thanks. Travis, thanks. David these. Next two questions I think kind of roll together and we'll let Andrea answer these I know he touched on these briefly but maybe. Andrew you could talk about, what. Is involved in. For. Example when you're offering, the. Palm vein at the ITM, or the ATM, what, are the various parties involved because the. Short answer is in regards, to what's. Happening, in at the ITM. Any form of biometric, authentication that, will be utilized at the ATM could also be utilized at the ITM, and. Again, we're seeing it in certain countries in certain places where facial, recognition is, being, used and such, but. Andrew maybe you could touch on what. Where. We're going with with.
Biometrics. At the ITM, I know you already touched on what's available today. The. Integration, piece who is involved in that how does that come about what are the various parties you have to integrate with yeah. Sure thanks Travis um well. Yeah. So there's, you. Know first you need the core process or ATM networks to have the technology certified so there's. Some core processors, out there today that are, implementing. Palm vein at the teller line and they. You. Know they have the server, where these the, palm vein scan data, goes into, the server in the back. In. The background so that you, know that will be required for you, know on the ATM, to integrate the. Palm encountered device on the ATM to that data basin on the on the fi server, so it's. It's going to require the core processor, on their side to have this technology, certified again this is in the, works right down today with a few course, we. See the other following, with, biometric. Certifications, so it's it's. A pretty, hot item right now I believe, you know some course I've already started implementing solving at the color-line in 2016. So it's it's. Taken, a little while to actually. Have this rolled out on some ATMs but it's moving very quickly now so we. Definitely, see a move, toward palm gain and other, biometric forms to be certified on core processors, today so, I. Believe. The, believe. That touched on both feet. What. Biometric, advancements, are being made. In the world of ITM so yeah getting your palm gain we. Looked at you. Know there is some, research being done on facial, recognition but, again we're having issues, with you. Know the. Accuracy. Of it so some some days you're wearing sunglasses the, lighting, may not be good in that area so, Paul may really looks like the direction the I guess. ATM market will be going to. Thank. You Andrew we did have a few questions come in from the crowd. Thank. You all for submitting, these Andrew. Can you name at this point the credit unions who are the beta testers, for the Palm Bay. I can't, at the moment but um. When. I all have to you, know find out if that would be okay with them reach. Out to Fe star after the fact and I'll double-check and see if that's okay if I can release. The institution's. Name, okay. Great, fair, enough Andrew anyone. Everyone, arrested in that ID. And. Also, had internet, maybe once we're done with the pilot and it's working we could probably possibly get them together of a phone call and and go over you, know how I was working for them, and, their, best strategies, for it so I'm, all we're always oh great. Yeah. Anybody who is out there interested, in in, further. Information, on who's piloting it, and the results of those pilots just reach out to us at F psi and we'll coordinate that facilitate. That conversation and, then, Andrew we did have a somebody, asked list, of networks that are currently in the, works for Palm Bay. So. Today it is a. If. I serve spectrum. I believe is going to be the first core.
Processor, Followed, by a class of DNA, that's. Soon to be followed by hopefully, prices the, other pricing course so we're. Not sure. Of the other ones at the moment but we. Believe that they, will fall quickly behind the. Pack so. That. That is what I know of today. Great, thank, you we'll continue to update everybody out there as those. Network. Certifications. Come come about pour and network certification, come about. Dave last question, somebody. Asks if you, can access user access, control systems. Not, only for say accessing, the building and such but also. Accessing. Vault night, drops. Other. Other, areas, where access. For, the, in branch FTE is critical. Can. You answer that. Very, simple one more answer, yes. Absolutely. Okay. Great. Thank you Dave all. Right well that's all we have for today I appreciate everybody's, time thank, you for joining us hopefully, it was somewhat. Enlightening, informative, this, is just a couple of the products that are available today please. Reach out to us if you're interested in anything in regards to mobile. Ivan. Scanning, authentication. Or, or some of the other areas, that we mentioned, that that, technology is available. We, appreciate, the, opportunity to, partner with you on any, of your biometric. Authentication needs, and please reach out to us if you have any questions, contact information. Of course is available, here on the screen we'll also be sending this out to all, the, participants, so thank, you very much and David. And Andrew, thank you for your time as well Thank, You Travis great. Make sure you. Look.
2019-03-08