Cryptographic Primitives of Blockchain Technology
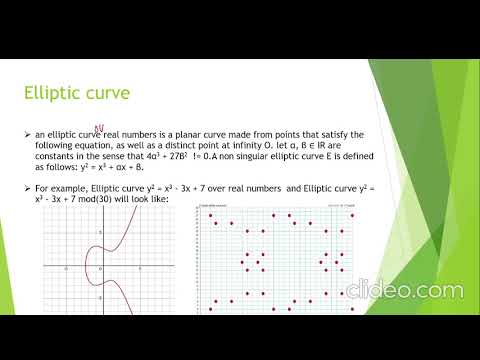
good morning everyone vr group 15 presents you cryptographic primitives of blockchain technology so we are going to see introduction to blockchain technology cryptographic primitives of blockchain ecds algorithm and implementation results so we all know that nowadays cryptocurrencies are very famous but have you ever no wonder that what is the technology behind bitcoin or ethereum or any cryptocurrency so let me introduce blockchain technology which is the core behind the any any cryptocurrencies because of the decentralized and tamper-proof behavior it will benefit us in many ways for example wave 3 decentralized finance and many more the examples are countless use cases are countless for the blockchain technology nowadays so can we we can define blockchain as a distributed ledger that is decentralized secure and open to the public and we have three types of blockchain platforms public chain private chain and the alliance so uh behind of the blockchain technology we have cryptographic primitives means cryptographic aspects which are used in blockchain and without the cryptography blockchain will never give us a high security object any transaction or any privacy related to our data so cryptographic innovatives are very very fundamental for the implementation of the blockchain technology cryptographic cryptography technology is primarily utilized in blockchain to secure user privacy and transaction information as well as to assure the data consistency okay so in bitcoin blockchain anyone can view payers bitcoin address the page bitcoin address and substance of each transaction many advanced cryptographic primitives have been developed to adjust this problem but none of them express their functionality in blockchain system so now we are going to study about the cryptographic primitives cryptographic primitives which are used in blockchain technology okay so we have classified the a primitives in two classes fundamental primitive and optional primitive fundamental primitives are used in building a blockchain secure secure blockchain cryptographic hashes and standard digital signatures are required for the blockchain to function as a tamper-proof publicly verifiable global record and in the optional primitive optional primitives provides blockchain privacy and anonymity for the transactions it covers special signatures commitments accumulators and well-known zero knowledge proof it it strengthens the privacy and anonymity of the blockchain basis transaction okay now we are going to see cryptographic uh our first cryptographic primitives which is used in the blockchain technology which is cryptographic hashes so uh cryptographic hashes are the algorithms that transform the large amount of data to shorter fixed length value means let's say we have a large arbitrary large arbitrary data message and we are going to transmit it but before going to transmit we are in uh going to input that message into the one has function which will give us the fixed length of fixed length of soft random string random string which is often called as digest and the uh these cryptographic hash functions are providing us two major security requirements which are uh which is one awareness and the collision is resistance one wayne s means it ensures that underlying hash function is not invertible and collision resistance means is ensures that finding two inputs with the same hash value is difficult is very very difficult and we are going to see that this cryptographic has functions are very useful in blockchain technologies and we are going to study these four uh use cases of that first is address generation second is merkle tree paradigm third message digest in digital signatures and fourth one is proof of work or we can say that bitcoin how cryptographic hazards are used in bitcoin mining so let us see uh how cryptographic assets are used in making immutable blockchains so in blockchains in blockchain we have many blocks blockchain is made up of uh blocks right so and each block contain each block contain current has its current has and previous previous blocks has block of the previous so and if if anyone wants to change the the haze of the parent means the parents modified has needs change in the child's previous block has reference this causes child has to change which forces a change in grand grandchild's pointer which affects the grandchild and so on so this affects the blockchain transactions and these underlying changes assures that block cannot be modified without forcing all future blocks to be recalculated and this is not possible and this is the very massive work to do so it is not possible to tamper the blockchain block of the blockchains next uh use case is blockchain address generation for the participants blockchain so uh we know that bitcoin bitcoin offers us crypto digital cryptocurrency and uh to transit uh to use that uh cryptocurrency we have to uh do the transactions right so bitcoin hs is a series of numbers and letters that you may provide to anyone who wants to pay you money right by employing one way one way cryptographic hashing the bitcoin address may be obtained from the public key so to generate the bitcoin address bitcoin uses sha plus ripe md algorithm sha means secure has a algorithm and the race integrity primitives evaluation message digest algorithm which is used to generate a bitcoin address from the public key third paradigm is third use case is merkle tree paradigm merkle tree using mercury is used in to quickly aggregate and ensure the authenticity of enormous amounts of data merkle trees are used in bitcoin to summarize all transactions in the block resulting in overall digital fingerprint of the complete set of transactions mercury ensures the data is accurate or not so let's say if anyone wants to change the transaction information which is in the merkle tree then has of that transaction will reflect those changes and this change would cascade up the merkle tree to merkle root so whole merkle drew merkle tree is tempered so changing the value of the merkle root and those invalidating the block so merkle tree look like merkle tree looks like we have one root merkle root and children of that general of the root and each each node contains has of the each node contains hash of the transaction each leaf node each leaf node contains h of the transaction one has of the transaction two and so on these this is are the leaf nodes leaf nodes but intermediary nodes are the combination of the hash functions like has of t1 plus has of t2 hole has is it is the combination of hashes so basically merkle tree provides the quickly aggregation and ensuring the authenticity of enormous amounts of data our next use case of the cryptographic hazards is proof of work or bitcoin mining so we know that nowadays bitcoin mining are very famous and very many miners are uh gaining profits profits of in terms of bitcoin through the mining so basically bitcoin mining is the technique for producing the new bitcoins by solving the computational challenge what we we mean by the computational challenges we have the miners have to guess the nouns number so many have the difficulty in understanding the nouns number so it is basically announced is a random string deciding which string to use as the nouns takes a lot of time trial and error so this is the guessing the number of nouns guessing the nouns number is the main computational challenge to mining to do mining a miner must generate a nouns added to the current headers has re has the value and compare it to the target as the miner has produced a solution and is granted the block if the resultant has value matches the conditions so we have we have one notion about the nouns and we have to guess these by the trial and error method trial and error method if we got the correct grounds then we we have we got the target has target has which mess which matches with match with our difficulty t of the block so next is message diges which is used in dsa dsm means digital signature algorithms so generally in digital signatures digital signatures we pass the message we we have two methods if first one is we we can pass only message only message plus our signature and second one is our message plus has the has of the message plus the signature disadvantage of the first method is that we we are going to loss our data integrity loss of the data integrity and benefit of the second one is we we gain more security and data integrity is confirmed so if anyone change the message the hash of the transmitted message and the hash of the has which is transmitted will be different right so we conclude that the message is legitimate and the data is secure if it is this if it is the similar or if not then a message is tampered and we cannot authenticate the source of the message okay detail signatures digital signature is a mathematical algorithm used to validate and authenticity and integrity of the message so what is the need of the digital signature data signature reduces the risk of duplication and alternation of the document itself digital signature ensures that signature are verified authenticate and legitimate so let me introduce the algorithm which is used for signing the document electronically so here is the working of detail signatures let's say we have alice a sender and bob as a receiver okay so if alice has to send the message in our case the message is a document which we have to send so what she will do she will uh she will apply the hash function which will transform which will give us the digest message digest as we have seen earlier so it will give the message and we apply the uh signature algorithm uh and we will sign this hash function with the sanders private key okay and now we will we will have this our message and signature we will transmit it through the internet and now the bob can bob will receive these two things message and signature now he will verify our signatures that is this document is authenticate or not if this document is of allies or alice or not so what he will do he will decrypt this signature with the sender's public key remember this is the for verification public key is used and for the signature generation private key is used so if the bob uses he who uses a license and allies public key he will get hash function value and from message he will also get one has value so if this both has values are same then we can say that this signature is okay so this document is authenticated and this doc the author of this document is allies so as we have seen the detail signatures are very important there are various algorithms used to use to signature electronically the document like there are rsa digital signature algorithms and there are other uh there are special uh case of uh signature algorithm which are used in bitcoin uh which is ecdsa ecds algorithm elliptic curve digital signature algorithm which we are going to see so for understanding the ecds algorithm first we have to understand what is elliptic curve in ecds algorithm so let let me first introduce the elliptic curves so elliptic curve is a real numbers over real numbers elliptic curve over real numbers is a planar curve made from points that satisfy the following equation as well as the listing point at infinity o let alpha and beta belongs to r are the constants in the sense that alpha 4 alpha cube plus 27 beta square is not equal to 0 then this elliptic curve is called a non-singular elliptic curve is defined as y square equal to x plus alpha x plus b so you can choose this alpha and beta which satisfies this condition 4 alpha cube plus 27 beta square not equal to 0 so let me take an example let's say we have elliptic curve e which is given by this formula y square equal to minus x cube minus 3 x plus 7 in this case our alpha is minus 3 and beta is 7 so this elliptic curve will look like this graph you can see that this this is a symmetric graph over symmetry graph over x axis and similarly if we have a elliptic curve y square equal to xu minus 3x plus mod 30 it means it is over finite field then it will look like this graph which have finite points so use of electric curves in a cryptography and and famous problem called as ec dlp elliptic curve discrete logarithm problem so elliptic curves over real numbers or finite fields that we have seen elliptic codes or over real number is y square equal to alpha x cube plus alpha x plus b enabled to cross over finite field are y square equal to x cube plus alpha x plus beta mod n forms a group under the addition operation which makes it useful to be used in cryptographic operations the mathematical foundation for the security of elective car crypto system is the computational complexity of electric car digital location problem ec dlp here is the city let let me introduce the elective curve discrete logarithm problem which is called ectlp so given a finite so what is the problem problem is that given a finite field f and elliptic curve e over f there are two points on the elliptic curve e c p and q which follows the following relation q equal to gamma into p so the problem is to find the gamma so let me visualize this for you so if we have a elliptical which looks like this and let's say we have a one point b here and another point q here okay so and we have also given that this p equal to comma p so so our problem is to find this gamma so how how many times we we will add this p to get the q so this is the discrete logarithm problem which is very hard to attack now we will see elliptic curve digital signature algorithm ecdsa was created by scott winestone in 1992 in response to lists this quest for public input on their initial dss proposal this signature method can be thought of as a variation of dsa for electric curve setup as we know that ec dlp is harder than the regular dlp ecd esc can be a very efficient algorithm for the purpose of retail signatures so now our actual algorithm starts so before going to uh we know that again in any literal signature algorithm we have two steps first is signature signature generation digital signature generation and the second is digital signature by verification digital signature verification so before going to see these two algorithms uh first let me introduce the domain parameters for the ecdsa so first is capital p which is equal to zero one star binary string uh which will cover the plain text play space a which is equal to which is from z q star to z star with the signature space capital k key space for with the parameters p q e a and b is the derivative curve over f b a is a point on the elliptic curve a and b are the point on the elliptic curve b is given by b equal to m into a p is a large prime integer and q is the last prime integer which is uh order of a on e and m is the private key which is uh constrained by zero uh laser equal to m laser equal to q minus one now we will see the e c d as a signature generation algorithm so as we have given the given the example let allies want to send a message m to bobby by signing the message so she will follow below steps to generate her digital signatures first she will select a random variable k such that 0 is or equal to k is or equal to q minus 1 now she will compute b equal to k into a and this b will given by two coordinates x and y so she will take a first x coordinate and modulo it by q so r equal to u mod q s equal to k minus 1 now s will be k minus 1 into has this is a hash function and for your information it is in in the bitcoin this has function uh the ssh hsa 256 algorithm is used for this hash operation plus m into r more q and now this r and s are used in digital signatures so this r and i s are called electronic signature for this message m now it's a digital signature verification algorithm so bob want to if bob want to verify the signature which is done by allies so for that he will follow below steps first of all he will get he he will get r and s as a digital signature so what he will do he will take in inverse of this s and get w w equal to s inverse more q then i equal to w into has m mod q j will be a w into r mod q and finally you he will get u v which is given by i into a plus j into v p if this bp is a allies public key which is given by m into a if r equal to equal to u and and then finally if r equal to equal to u more q then signature is valid otherwise the signature is not valid it means that if r e r is does not equal to u then we can say that this document or message is not owned by allies okay so this is the two algorithms for digital signature now we will see the ecdsa algorithm in bitcoin blockchain so bitcoin uses this spec 256 k1 elliptic curve with the ecds algorithm and hash function usb in getting the igc's sha-256 this spec 256 k1 has the following domain parameters which are used which are used in which are used in ecds algorithm so first is p which is two raised to two uh which is given by this [Music] second is elliptic curve which has two parameters alpha and beta in which alpha is zero and beta equal to seven so this curve will look like this y square equal to x cube plus seven beta these are the points on the elliptic core and this is the order of the cryptego queue so we have also done implementation in python language so the uh this is the domain parameters as we have seen a b p e q and a first first of all we have generated the message which is we have taken the messages mathematics is the king of all sciences and the number theory is the queen of mathematics and we have generated the hash function now we have our signature algorithm in which we have taken this random key and this private key so we have followed the exact steps that we have seen in our previous slides we have followed this exact exact steps and we have uh gain our r and s as a digital signature now as verification starts at that time also we have followed that exact exact steps and we have get our u and v now we have checked that r is equal to u is equal to u then signature is valid otherwise not valid so let me show you the results of this results for this message so here is our message mathematics is the king of all sciences and number theory is a queen the digest for this message is this which is a fixed length now signature this is our signature are in r and s so we have gained this r and by the verification algorithm we have uh find the you so you can see that this r and u are the same so our signature is valid thank you thank you very much [Music]
2022-05-20 07:18


